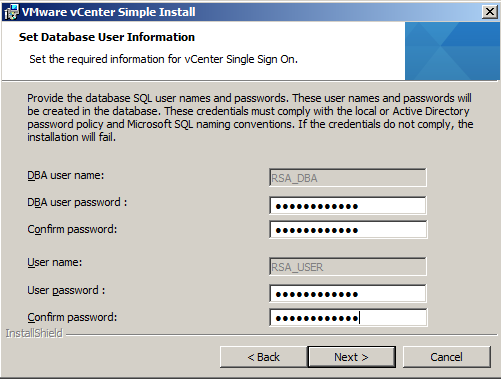
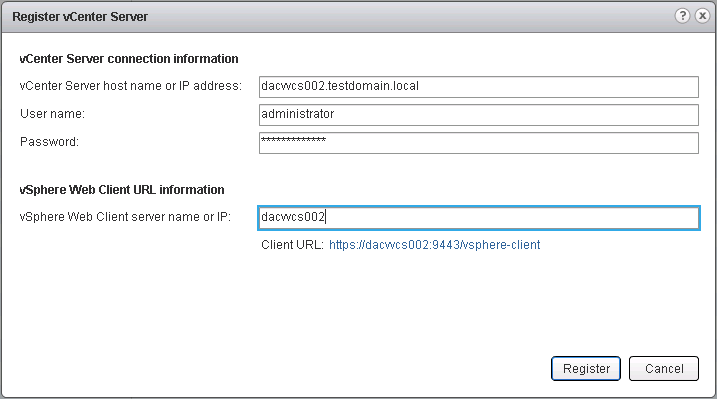
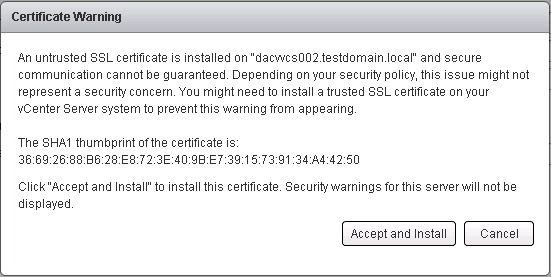
Group Policy Processing
Group Policy Objects (GPO) are a collection of configurable policy settings that are organised as a single object and contain Computer Configuration policies which are applied to computers during Startup and User Configuration policies which are applied to users during logon.
Group Policy has 2 main configurations
- Computer
- User
When the computer starts, it processes all of the computer policies that are assigned to the computer object from AD in this order:
- Local Policy
- Site
- Domain
- OU
- Child OU
- Any startup scripts that were assigned to it in Group Policy
When a user logs in to the computer, the computer processes all of the policies assigned to that user object in this order:
- Local Policy
- Site
- Domain
- OU
- Child OU
- Any startup scripts that were assigned to it in Group Policy
What is Loopback processing?
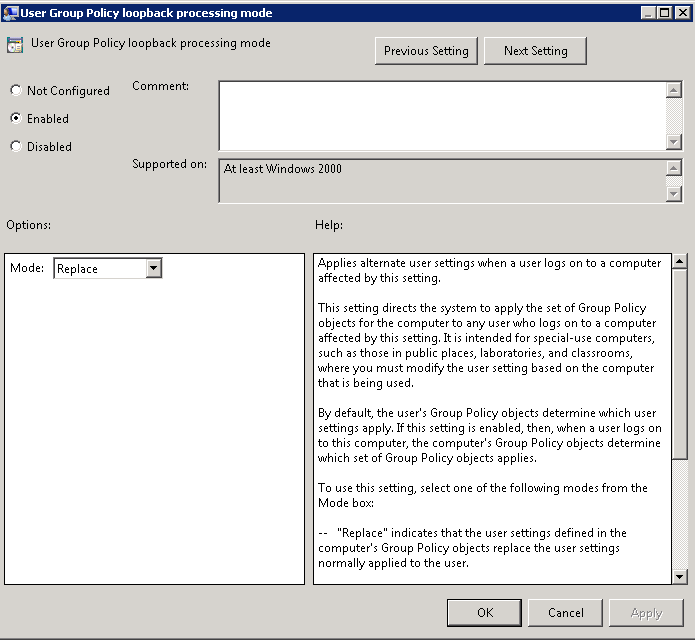
The User Group Policy loopback processing mode option available within the computer configuration node of a Group Policy Object is a useful tool for ensuring certain user settings are applied on specified computers.
Essentially loopback processing changes the standard group policy processing in a way that allows user configuration settings to be applied based on the computers GPO scope during logon. This means that user configuration options can be applied to all users who log on to a specific computer.
Where is Loopback Processing found?
Loopback processing is configured in the Group Policy Management Console in Computer Configuration / Policies / Administrative Templates / System / Group Policy / User Group Policy loopback processing mode.
Modes
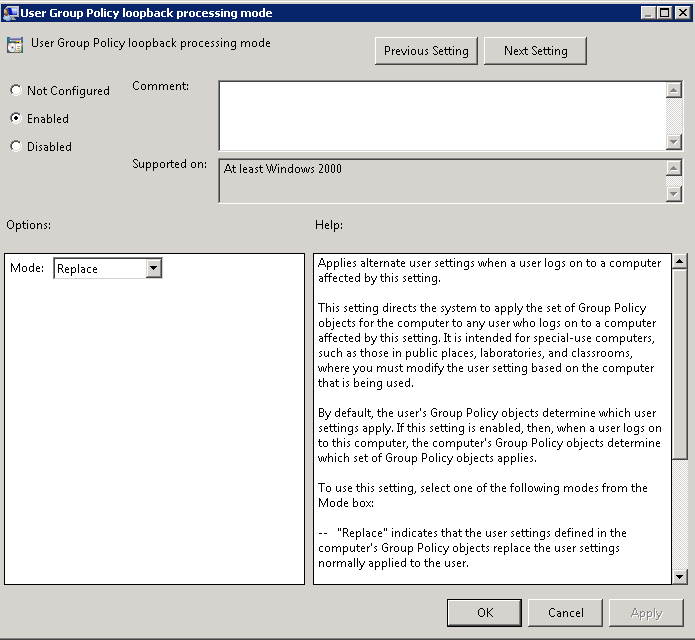
- Replace
Replace Mode replaces the User policy that is assigned to the user. In the Computer Configuration, set the loopback processing mode to Replace. Next, assign user policies to the computer in addition to the computer polices, you would normally assign. When the computer starts, it will process the computer policies. When the user logs in, instead of processing the GPO’s assigned to the user, the computer will apply the user policies that are assigned to the computer object.
Where can it be used?
- File, Print, and other servers that non-admin users don’t typically access via the console or Remote Desktop. When someone with admin rights logs in via the console or Remote Desktop, they only have the default policy or any other policy
- Redirecting folders, mapping printers, or assigning software with Group Policy; you don’t want unwanted drivers or software showing up on your production server that now has to be maintained or removed.
- Kiosk systems. An Administrator would typically have an unrestricted desktop experience. If that user logs onto a Kiosk machine, he or she would normally have a “wide open” desktop. This might be dangerous, so it may be useful to enable Replace mode to enforce a specific set of enforced settings.
- Any other environment where the user settings should be determined by the computer account instead of the user account.
- Terminal Servers
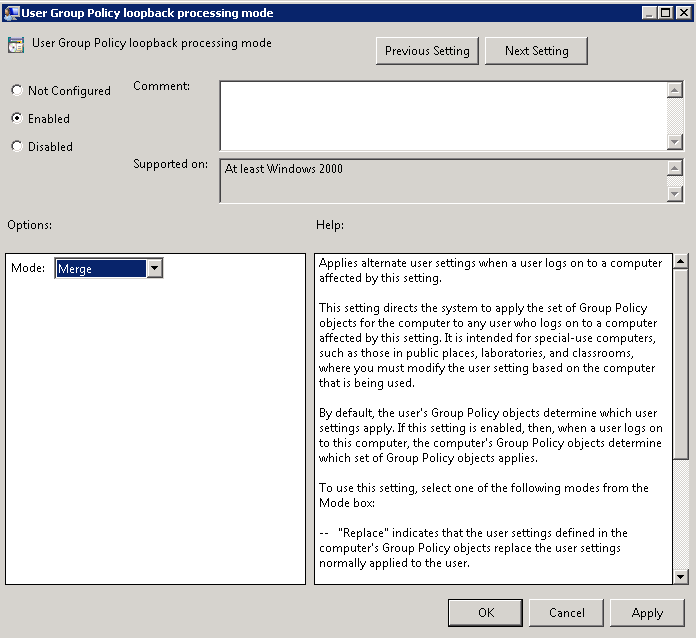
- Merge
Merge Mode combines the policy that is assigned to the user instead of completely replacing it like in Replace Mode. When the computer starts, it will process the assigned computer policies. When the user logs in, the computer will process the user policies assigned to the user as it normally would and then processes the user policies that have been assigned to the computer object.
Where can it be used?
- Merge Mode can be useful if you need to make additions to a policy or override a general user policy that a user receives when he/she logs in to a computer
Processing order of Loopback Mode
Without Loopback
- Computer Node policies from all GPOs in scope for the computer account object are applied during start-up (in the normal Local, Site, Domain, OU order)
- User Node policies from all GPOs in scope for the user account object are applied during logon (in the normal Local, Site, Domain, OU order).
Loopback processing enabled (Merge Mode)
- Computer Node policies from all GPOs in scope for the computer account object are applied during start-up (in the normal Local, Site, Domain, OU order), the computer flags that loopback processing (Merge Mode) is enabled.
- User Node policies from all GPOs in scope for the user account object are applied during logon (in the normal Local, Site, Domain, OU order).
- As the computer is running in loopback (Merge Mode) it then applies all User Node policies from all GPOs in scope for the computer account object during logon (Local, Site, Domain and OU),
- If any of these settings conflict with what was applied , then the computer account setting will take precedence.
Loopback processing enabled (Replace Mode)
- Computer Node policies from all GPOs in scope for the computer account object are applied during start-up (in the normal Local, Site, Domain, OU order), the computer flags that loopback processing (Replace Mode) is enabled.
- User Node policies from all GPOs in scope for the user account object are not applied during logon (as the computer is running loopback processing in Replace mode no list of user GPOs has been collected).
- As the computer is running in loopback (Replace Mode) it then applies all User Node policies from all GPOs in scope for the computer account object during logon (Local, Site, Domain and OU)
Useful Link
http://kudratsapaev.blogspot.co.uk/2009/07/loopback-processing-of-group-policy.html