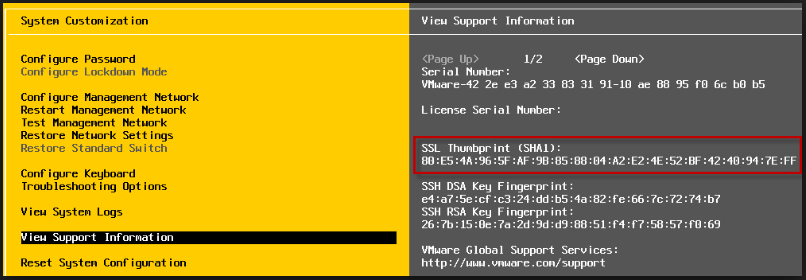
What is ESXi Lockdown Mode?
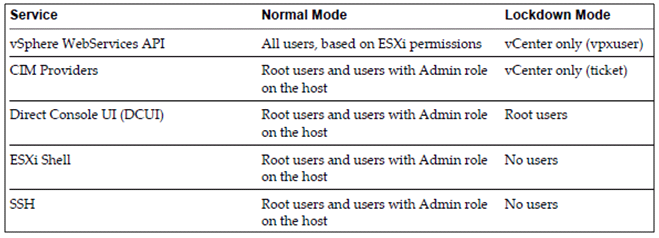
To increase the security of your ESXi hosts, you can put them in lockdown mode. When you enable lockdown mode, no users other than vpxuser have authentication permissions, nor can they perform operations against the host directly. Lockdown mode forces all operations to be performed through vCenter Server.
What happens?
- When a host is in lockdown mode, you cannot run vSphere CLI commands from an administration server, from a script, or from vMA against the host. External software or management tools might not be able to retrieve or modify information from the ESXi host.
- The root user is still authorized to log in to the direct console user interface when lockdown mode is enabled
- If you enable or disable lockdown mode using the Direct Console User Interface (DCUI), permissions for users and groups on the host are discarded. To preserve these permissions, you must enable and disable lockdown mode using the vSphere Client connected to vCenter Server.
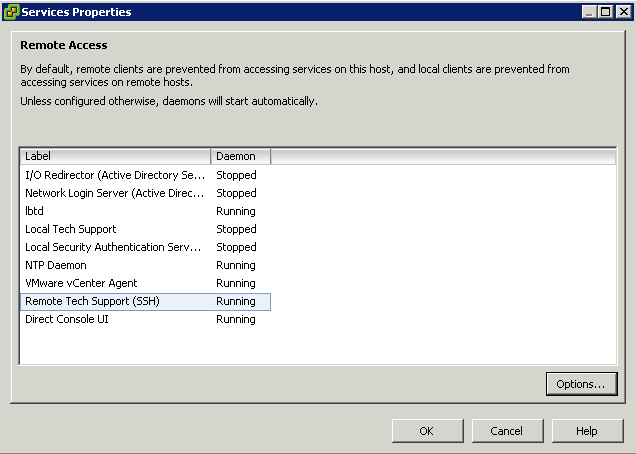
- Enabling or disabling lockdown mode affects which types of users are authorized to access host services, but it does not affect the availability of those services. In other words, if the ESXi Shell, SSH, or Direct Console User Interface (DCUI) services are enabled, they will continue to run whether or not the host is in lockdown mode.
- Lockdown mode is only available on ESXi hosts that have been added to vCenter Server.
- Users who were logged in to the ESXi Shell before lockdown mode was enabled remain logged in and can run commands. However, these users cannot disable lockdown mode. No other users, including the root user and users with the Administrator role on the host, can use the ESXi Shell to log in to a host that is in lockdown mode.
Lockdown mode behaviour
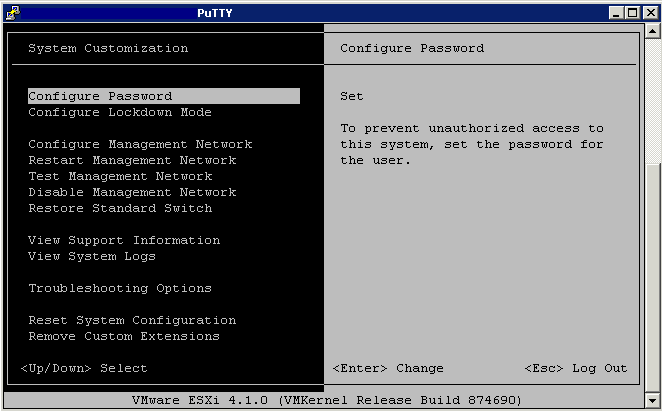
Enabling Lockdown Mode
- Through the Security Profile
- Through DCUI
- Through adding a new host to a cluster
Through the security profile
- Select the host in the inventory panel.
- Click the Configuration tab and click Security Profile.
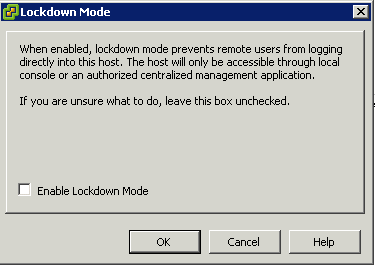
- Click the Edit link next to lockdown mode.
- The Lockdown Mode dialog box appears.
- Select Enable Lockdown Mode.
- Click OK.
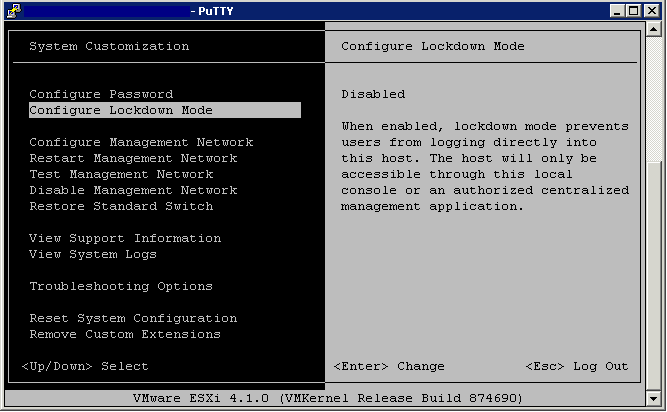
Through the DCUI
- Log into an SSH Session or directly into the Host console screen
- Press F2 and login
- Scroll to the Configure Lockdown Mode setting and press Yes and Enter