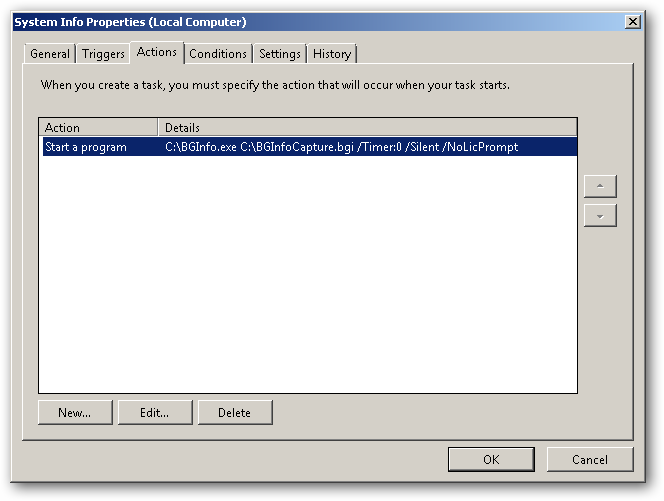
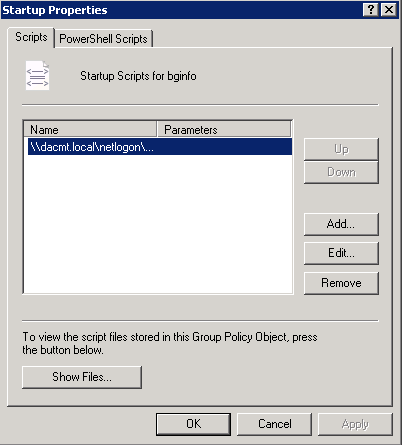
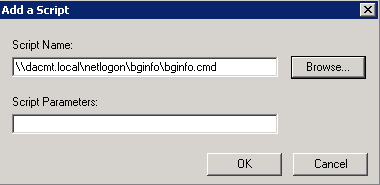
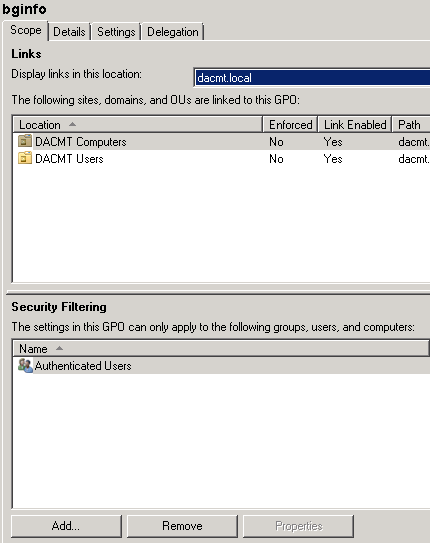
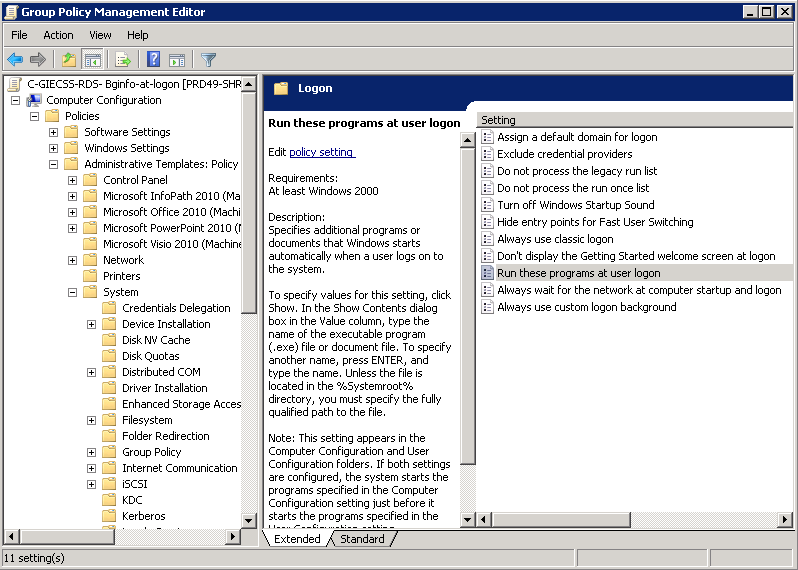
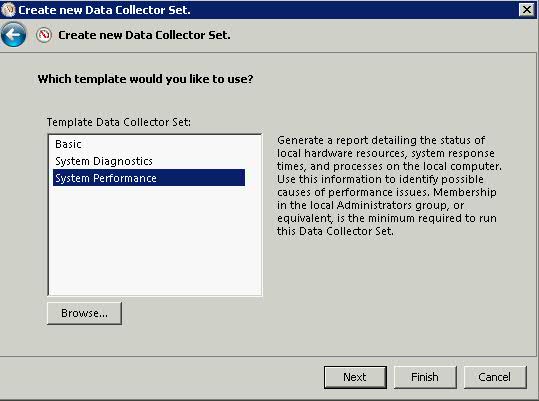
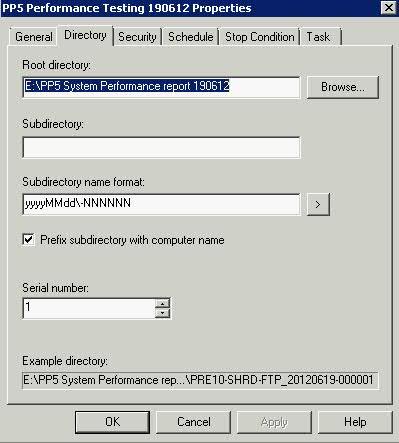
What is DFS?
DFS stands for Distributed File System and provides two very important benefits for system administrators of Wide Area Networks (WAN) with multiple sites that have a need to easily store, replicate, and find files across all locations.
- The first is the benefit of being able to have one Namespace that all users can use, no matter what their location, to locate the files they share and use.
- The second is a configurable automatic replication service that keeps files in sync across various locations to make sure that everyone is using the same version.
Distributed File System (DFS) allows administrators to group shared folders located on different servers by transparently connecting them to one or more DFS namespaces. A DFS namespace is a virtual view of shared folders in an organization. Using the DFS tools, an administrator selects which shared folders to present in the namespace, designs the hierarchy in which those folders appear, and determines the names that the shared folders show in the namespace. When a user views the namespace, the folders appear to reside on a single, high-capacity hard disk. Users can navigate the namespace without needing to know the server names or shared folders hosting the data. DFS also provides many other benefits, including fault tolerance and load-sharing capabilities, making it ideal for all types of organizations.
Two very important aspects of DFS
DFS NameSpaces
Each namespace appears as a folder with subfolders underneath.
The trick to this is that those folders and files can be on any shared folder on any server in your network without the user having to do any complicated memorization of server and share names. This logical grouping of your shares will also make it easier for users at different sites to share files without resorting to emailing them back and forth.
DFS Replication
This service keeps multiple copies of files in sync.
Why would you need this? Well if you want to improve performance for your DFS users you can have multiple copies of your files at each site. That way a user would be redirected to the file local to them, even though they came through the DFS Namespace. If the user changed the file it would then replicate out to keep all copies out in the DFS Namespace up to date. This feature of course is completely configurable.
DFS Namespaces Illustrated
The following figure illustrates a physical view of file servers and shared folders in the Contoso.com domain. Without a DFS namespace in place, users need to know the names of six different file servers, and they need to know which shared folders reside on each file server.
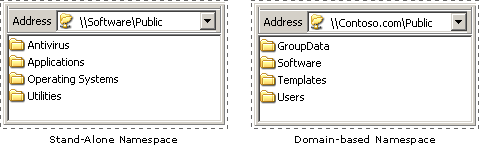
When the IT group in Contoso.com implements DFS, they must first decide the type of namespace to implement. Windows Server 2003 offers two types of namespaces: stand-alone and domain-based. The IT group also chooses a root name, which is similar to the shared folder name in a Universal Naming Convention (UNC) path \\ServerName\SharedFolderName.
The following figure illustrates two namespaces as users would see them. Notice how the address format differs — one begins with a server name, Software, and the other begins with a domain name, Contoso.com. These differences illustrate the two types of roots: stand-alone roots, which begin with a server name, and domain-based roots, which begin with a domain name. Valid formats for domain names include \\NetBIOSDomainName\RootName and \\DNSDomainName\RootName
Installing DFS
Installing DFS Management also installs Microsoft .NET Framework 2.0, which is required to run the DFS Management snap-in.
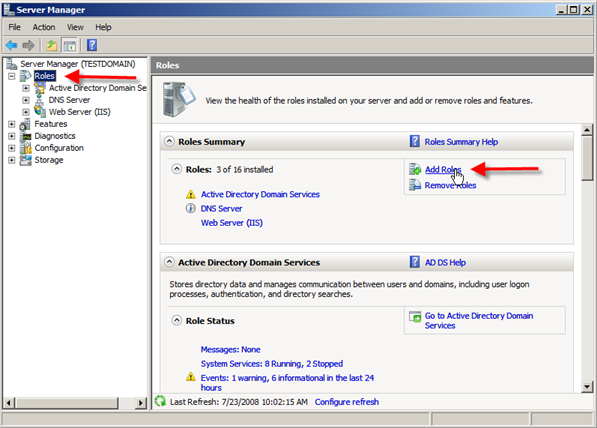
- Open Server Manager.
- Click Roles > Click Add Roles
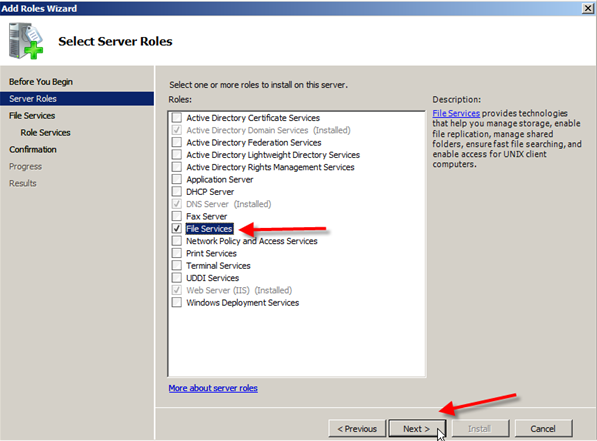
- Select File Services from the list of roles.
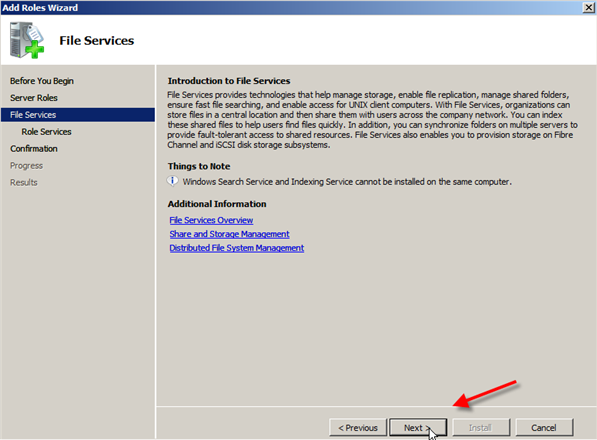
- Now you will get an Introduction to File Services information screen; read through it and move on by clicking Next.
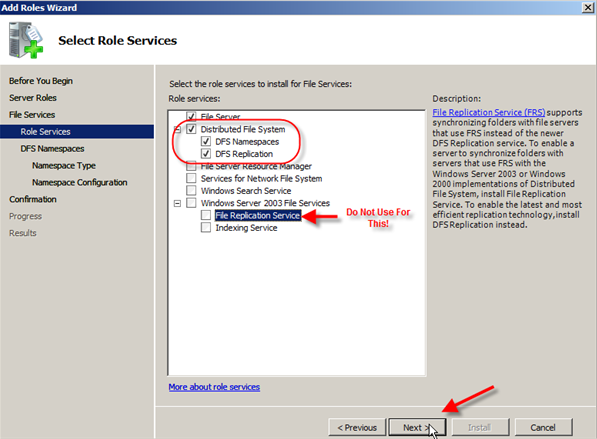
- In Select Service Roles you can click on Distributed File System and it should also place a check next to DFS Namespaces & DFS Replication; after this click Next.NOTE: At the bottom you will see Windows Server 2003 File Services and File Replication Service. You would only choose this if you were going to be synchronizing the 2008 server with old servers using the FRS service.
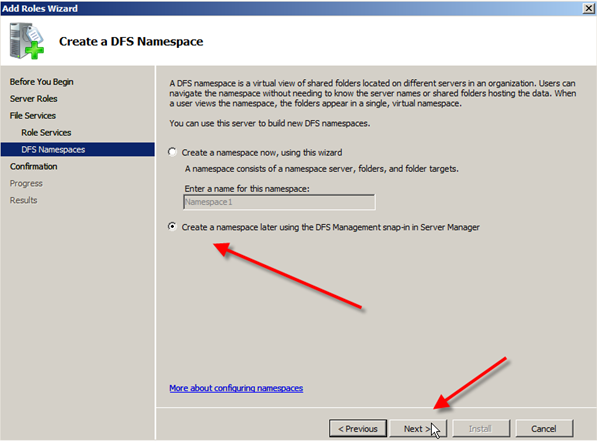
- On the Create a DFS Namespace screen you can choose to create a namespace now or later.I am going to create one later. So I am going to choose Create a namespace later using the DFS Management snap-in in Server Manager and then click Next.
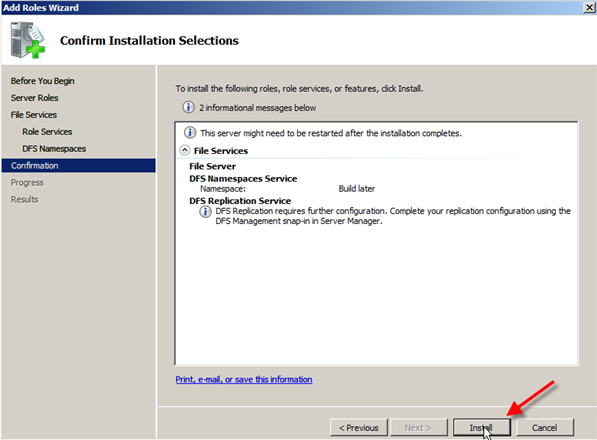
- The next screen allows you to confirm your installation selections, so review and then click Install.
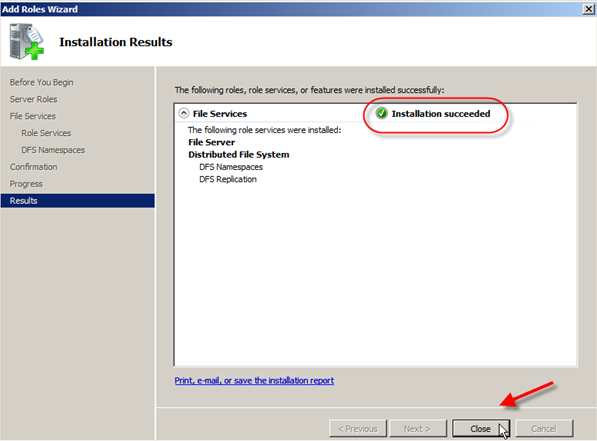
- After a short interval of loading you will see the Installation Results screen which will hopefully have Installation succeeded in the top right. Go ahead and click Close.
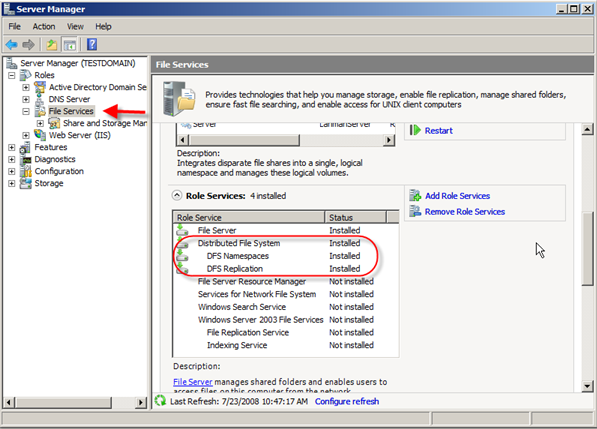
- In Server Manager you should now see File Services and under the Role Services you will see the installed components:
DFS has the following dependencies:
- Active Directory replication. Domain-based DFS requires that Active Directory replication is working properly so that the DFS object resides on all domain controllers in the domain.
- Server Message Block (SMB). Clients must access DFS root servers by using the SMB protocol.
- Remote Procedure Call (RPC) service and Remote Procedure Call Locater service. The DFS tools use RPC to communicate with the DFS service running on DFS root servers.
- Distributed File System service dependencies. The Distributed File System service must be running on all DFS root servers and domain controllers so that DFS can work properly. This service depends on the following services:
The Server service, Workstation service, and Security Accounts Manager (SAM) service on DFS root servers. The Distributed File System service also requires an NTFS volume to store the physical components of DFS on root servers.
The Server service and Workstation service on domain controllers.
See the next Blog Post for information on Configuring DFS