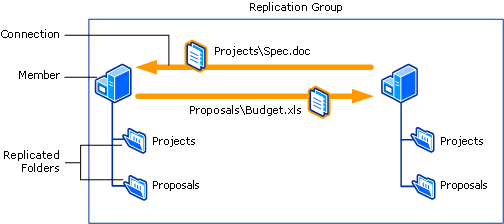
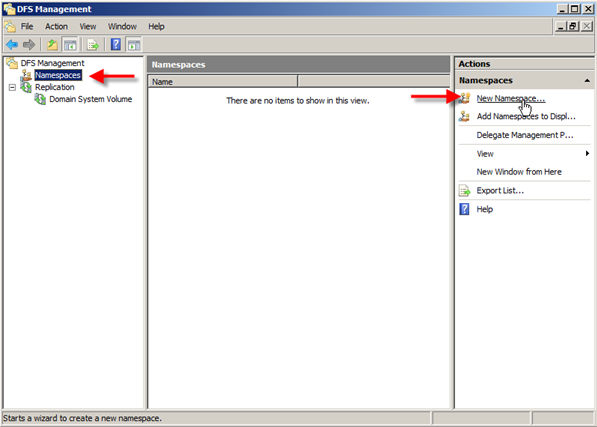
What does the Command “Route” do in Windows?
Displays and modifies the entries in the local IP routing table. Used without parameters, route displays help.
Syntax
route [-f] [-p] [Command [Destination] [mask Netmask] [Gateway] [metric Metric]] [if Interface]]
Explanations of switches and commands
Parameters
Clears the routing table of all entries that are not host routes (routes with a netmask of 255.255.255.255), the loopback network route (routes with a destination of 127.0.0.0 and a netmask of 255.0.0.0), or a multicast route (routes with a destination of 224.0.0.0 and a netmask of 240.0.0.0). If this is used in conjunction with one of the commands (such as add, change, or delete), the table is cleared prior to running the command.
When used with the add command, the specified route is added to the registry and is used to initialize the IP routing table whenever the TCP/IP protocol is started. By default, added routes are not preserved when the TCP/IP protocol is started. When used with the print command, the list of persistent routes is displayed. This parameter is ignored for all other commands. Persistent routes are stored in the registry location HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Tcpip\Parameters\PersistentRoutes
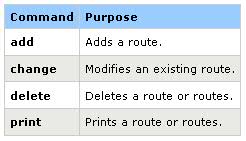
Commands
Specifies the command you want to run. The following table lists valid commands
Specifies the network destination of the route. The destination can be an IP network address (where the host bits of the network address are set to 0), an IP address for a host route, or 0.0.0.0 for the default route.
Specifies the netmask (also known as a subnet mask) associated with the network destination. The subnet mask can be the appropriate subnet mask for an IP network address, 255.255.255.255 for a host route, or 0.0.0.0 for the default route. If omitted, the subnet mask 255.255.255.255 is used. Because of the relationship between the destination and the subnet mask in defining routes, the destination cannot be more specific than its corresponding subnet mask. In other words, there cannot be a bit set to 1 in the destination if the corresponding bit in the subnet mask is a 0.
Specifies the forwarding or next hop IP address over which the set of addresses defined by the network destination and subnet mask are reachable. For locally attached subnet routes, the gateway address is the IP address assigned to the interface that is attached to the subnet. For remote routes, available across one or more routers, the gateway address is a directly reachable IP address that is assigned to a neighboring router.
Specifies an integer cost metric (ranging from 1 to 9999) for the route, which is used when choosing among multiple routes in the routing table that most closely match the destination address of a packet being forwarded. The route with the lowest metric is chosen. The metric can reflect the number of hops, the speed of the path, path reliability, path throughput, or administrative properties.
if Interface
Specifies the interface index for the interface over which the destination is reachable. For a list of interfaces and their corresponding interface indexes, use the display of the route print command. You can use either decimal or hexadecimal values for the interface index. For hexadecimal values, precede the hexadecimal number with 0x. When the if parameter is omitted, the interface is determined from the gateway address.
Displays help at the command prompt
Examples
To display the entire contents of the IP routing table, type:
route print
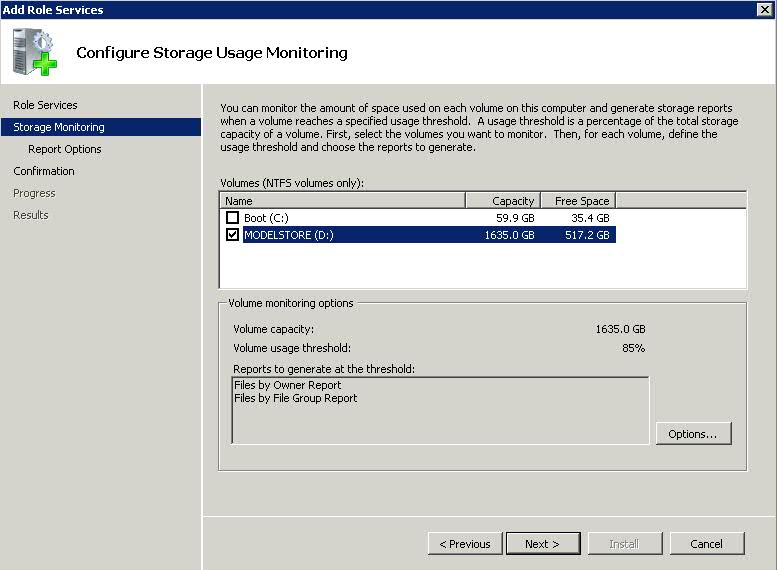
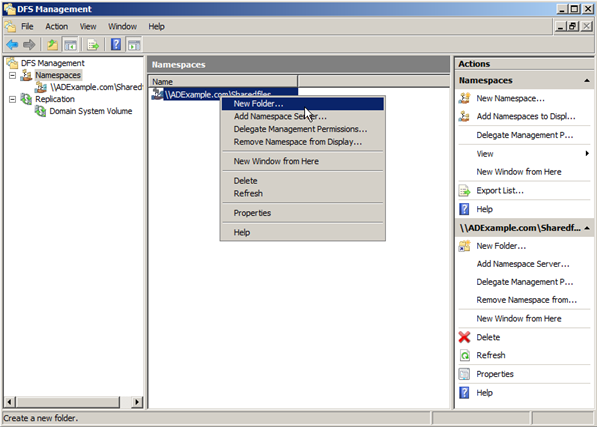
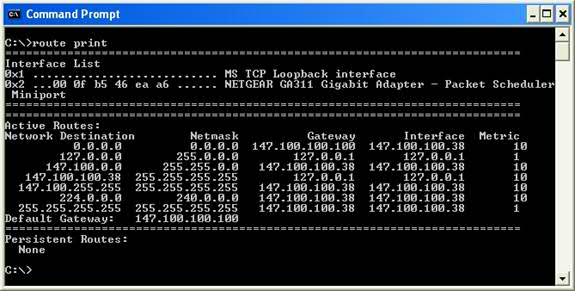
The routing tables are an important part of Windows’ TCP/IP protocol stack, but they aren’t something that the operating system normally displays to the casual user. If you want to see the routing tables, you will have to open a Command Prompt window and then enter the ROUTE PRINT command. Upon doing so, you will see a screen similar to the one that’s shown below
To display the routes in the IP routing table that begin with 10., type:
route print 10.*
To add a default route with the default gateway address of 192.168.12.1, type:
route add 0.0.0.0 mask 0.0.0.0 192.168.12.1
To add a route to the destination 10.41.0.0 with the subnet mask of 255.255.0.0 and the next hop address of 10.27.0.1, type:
route add 10.41.0.0 mask 255.255.0.0 10.27.0.1
To add a persistent route to the destination 10.41.0.0 with the subnet mask of 255.255.0.0 and the next hop address of 10.27.0.1, type:
route -p add 10.41.0.0 mask 255.255.0.0 10.27.0.1
To add a route to the destination 10.41.0.0 with the subnet mask of 255.255.0.0, the next hop address of 10.27.0.1, and the cost metric of 7, type:
route add 10.41.0.0 mask 255.255.0.0 10.27.0.1 metric 7
To add a route to the destination 10.41.0.0 with the subnet mask of 255.255.0.0, the next hop address of 10.27.0.1, and using the interface index 0x3, type:
route add 10.41.0.0 mask 255.255.0.0 10.27.0.1 if 0x3
To delete the route to the destination 10.41.0.0 with the subnet mask of 255.255.0.0, type:
route delete 10.41.0.0 mask 255.255.0.0
To delete all routes in the IP routing table that begin with 10., type:
route delete 10.*
To change the next hop address of the route with the destination of 10.41.0.0 and the subnet mask of 255.255.0.0 from 10.27.0.1 to 10.27.0.25, type:
route change 10.41.0.0 mask 255.255.0.0 10.27.0.25