What is a Roaming Profile?
A roaming user profile is user data, stored in a specific folder structure, to follow users as they log on to and log off from different computers. Roaming user profiles are stored on a central server location. At log on, Windows copies the user profile from the central location to the local computer. When the user logs off, Windows copies changed user profile data from the client computer to the central storage location. This ensures that the client data follows users as they roam the environment.
Roaming user profiles solve part of the roaming problem, but it also creates added concerns. User profiles can increase in size, some as large as 20 megabytes or more. This increase causes delays in user logons, because it takes some time for Windows to copy the information to the local computer. Another concern with roaming user profiles is that they are saved only at logoff. Therefore, when a user logs on to one computer and changes data within their profile, the changes remain local and remain local until the user logs off, making real-time access to user data challenging in a roaming user environment. Folder Redirection reduces some of these problems.
Folder Redirection
Folder Redirection is a client side technology that provides an ability to change the target location of predetermined folders found within the user profile. This redirection is transparent to the user and gives the user a consistent way of saving their data, regardless of its storage location. Folder Redirection provides a way for administrators to divide user data from profile data. This division of user data decreases user logon times, and Windows downloads less data. Windows redirects the local folder to a central location, giving the user immediate access to their data when they save it, regardless of the computer they are using. This immediate access removes the need to update the user profile.
Folder Redirection helps with slow logons and missing data problems because the Application Data, Desktop, My Documents, My Pictures, and Start Menu can be supported by Folder Redirection in Windows XP/Vista/7
Windows XP Profile Folder Locations
* These directories are hidden by default. To see these directories, change the View Options.
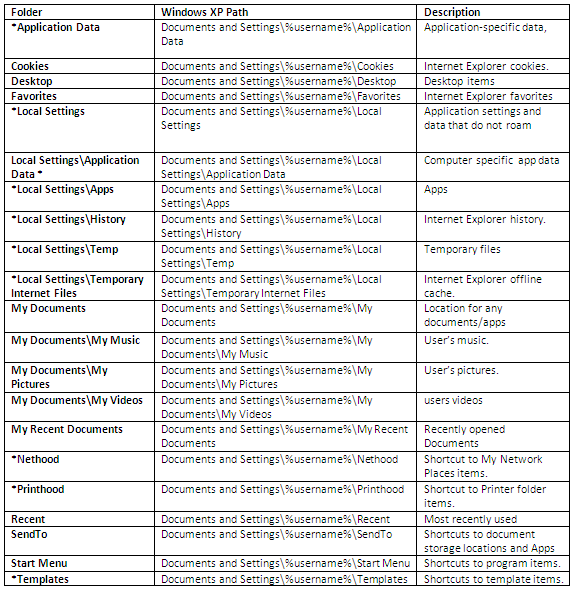
Windows 7 Profile Folder Locations
- The biggest change is the location of the profiles themselves – the user profiles are now located under c:\users\<username> instead of c:\documents and settings\<username>
- Appdata – This is now a combination of c:\documents and settings\\application data\ and c:\documents and settings\\local settings\ – this folder contains three folders – “Local”, “LocalLow” and “Roaming”
Setting up a Profile and Home Directory Folder Requirements
Note: Profiles and Home Directories can be on the same server
- A Profile Server
- A Home Directory Server
Instructions
When setting up the file server you need to be sure that the permission on the folder are setup so that a user can create a new folder however you also need to ensure that they can only see their own files.
Note: When creating the Share, it is Best Practice to add a $ sign to the end of the Share which will keep it hidden from regular users
- Create a new folder and call it Profiles
- Click the Sharing tab and then click Advanced Sharing then click Permissions
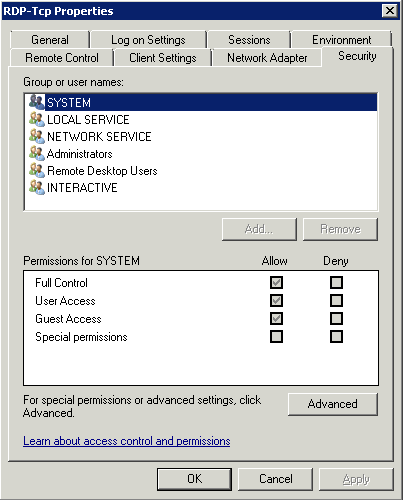
- Make sure the Everyone Group has Full Control
- Make sure the Administrators Group has Full Control, you may have a differently named Admin Group so add as necessary
- Make sure the SYSTEM group has Full Control
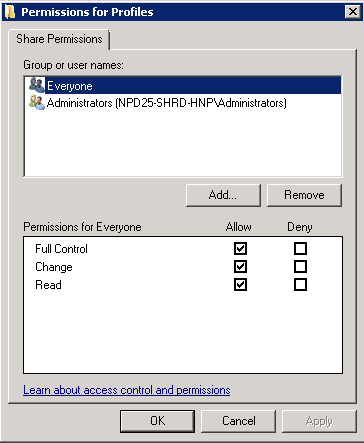
- Click OK
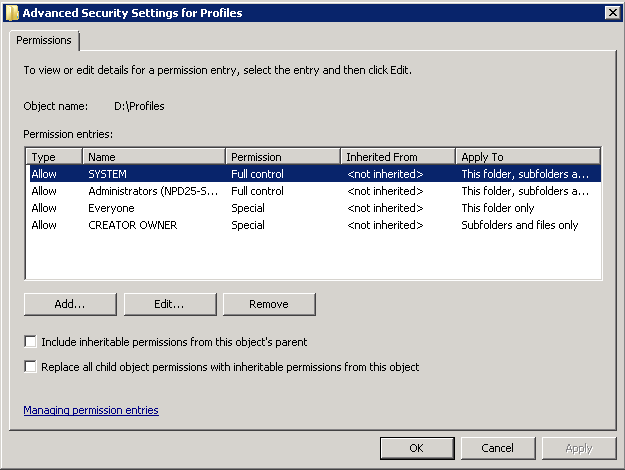
- Click on the Security Tab and Untick “Include inheritable permission form this object’s parent”
- Click on the Security Tab and Select Advanced
- Select Change Permissions and make sure your permissions look like the below screenprint and conform to the below information
- Configure the folder to not inherit permissions and remove all existing permissions.
- Add the file server’s local Administrators group with Full Control of This Folder, Subfolders, and Files.
- Add the Domain Admins domain security group with Full Control of This Folder, Subfolders, and Files.
- Add the System account with Full Control of This Folder, Subfolders, and Files.
- Add the Creator/Owner with Full Control of Subfolders and Files.
- Add the Authenticated Users group with both List Folder/Read Data and Create Folders/Append Data – This Folder Only rights. The Authenticated Users group can be replaced with the desired group, but do not choose the Everyone group as a best practice.
The share permissions of the folder can be configured to grant administrators Full Control and authenticated users Change permissions.
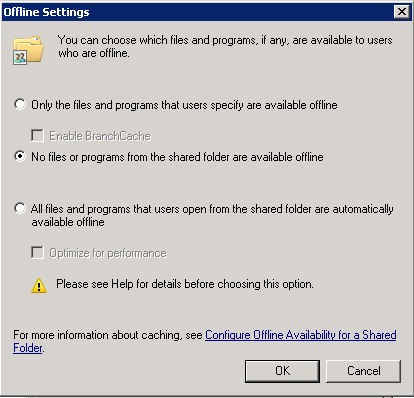
- After you configure the share and security permissions, click on the Sharing tab and then the “Caching” button and select the “No Files or programs from the share folder are available offline” options then press OK then OK then Close.
- Next do exactly the same to create a shared folder for the Home Directory folder
Setting up a User account with a Profile Path Remote Desktop Profile Path and Home Directory
NOTE: This can be controlled by Group Policy but do it manually while you test a user
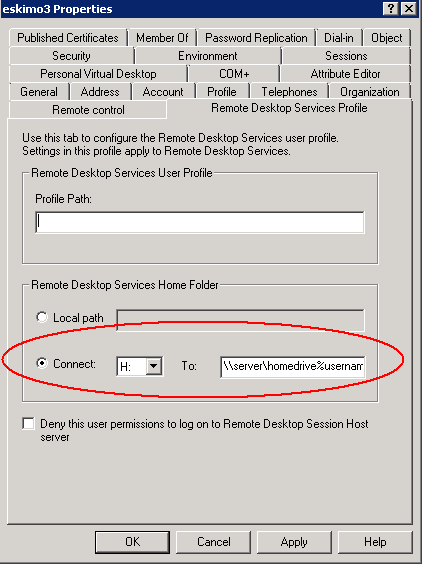
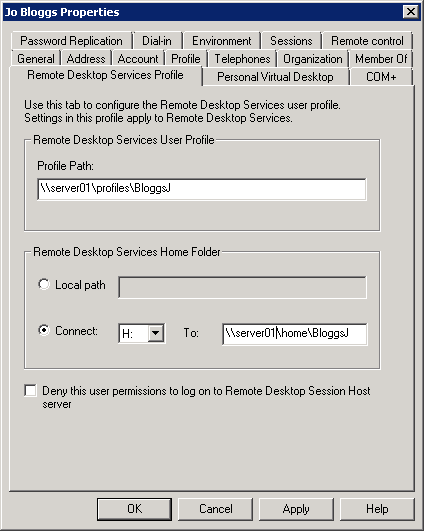
NOTE: I had to put the same path in the Profile Path and the Remote Desktop Services Profile Path to get full roaming profile on my folders
- You configure the profile location for a user on the Profile or Remote Desktop Services Profile tab within Active Directory Users and Computers. Type a UNC path to where Windows should create the user profile. The following screen shots below give you an example a user account configured with a profile path and a Remote Desktop Services Profile
- The folder redirection client side extension is only able to process two environment variables: %username% and %userprofile%. Other environment variables such as %logonserver%, %homedrive% and %homepath% will not work with folder redirection.
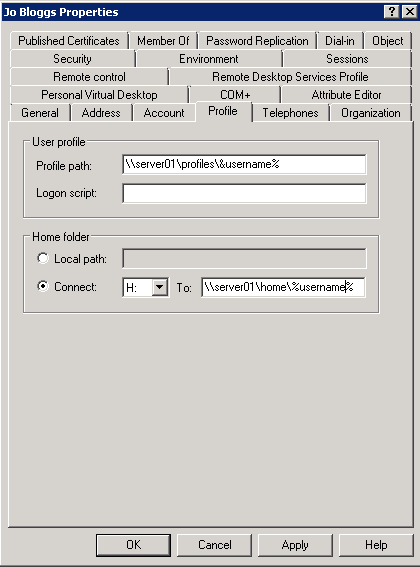
- And also add the same for the Remote Desktop Services Profile (Note this can be controlled by Group Policy as detailed at the end of this document. For now, I’ve just added it in manually so you can see where it is)
Setting up Group Policy for re-directing User Profile folders
- To start the Group Policy snap-in from the Active Directory Users and Computers snap-in, click Start, point to Programs, click Administrative Tools, and then click Group Policy Management
- In the MMC console tree, right-click the domain or the OU for which to access Group Policy and select Create a GPO in this domain and link it here
- Click New, and type the name to use for the GPO. For example, type Roaming Profile GPO
- Expand the OU so you can see the new Policy and right click and Edit to open the Group Policy
- Click Edit to open the Group Policy snap-in and edit the new GPO
- In the Group Policy console, expand the User Configuration, Policies, Windows Settings, and Folder Redirection nodes. Icons for the personal folders that can be redirected will be displayed
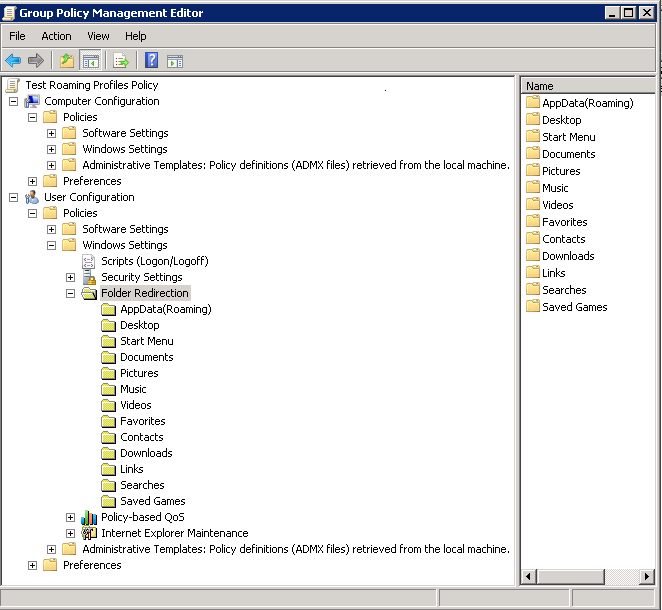
- Right click on AppData (Roaming) and select Properties
- There are 3 settings to choose from – Not Configured, Basic Redirection and Advanced Redirection
Basic Redirection and Advanced Redirection are available to all folders listed in the snap-in. You use basic redirection when you store the selected folder in the Group Policy object on the same share for all users. You use Advanced Redirection when you want to redirect the selected folder to a different location based on a security group membership of the user. For example, you would use Advanced Folder Redirection when you want to redirect folders belonging to the Accounting group to the Finance server and folders belonging to the Sales group to the Marketing server
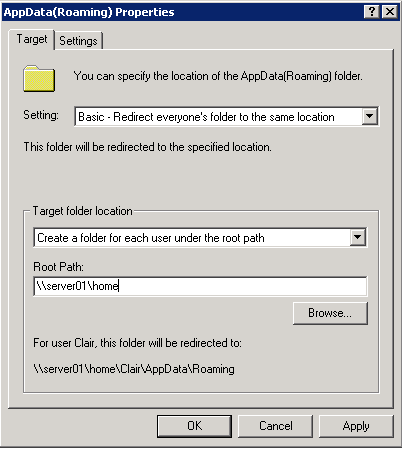
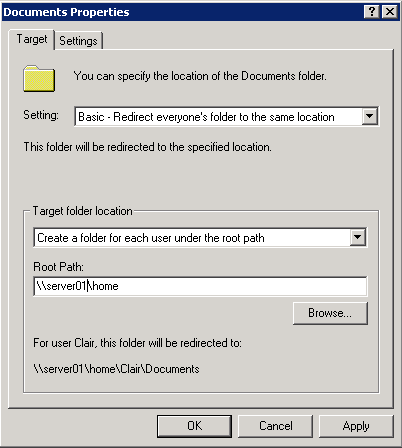
- Choose Basic – Redirect everyone’s folder to the same location
- Choose Create a folder for each user under the root path
- Type the root path to the shared folder
- Click Settings
- Untick Grant the User Exclusive rights to AppData(Roaming)
If you leave “Grant the user exclusive rights to Documents” ticked then when the folder is initially setup Windows will block inheritance on the folder and grant exclusive access to the users on these files. This will lockout even administrators to the files which makes administration of these folders very difficult. If an administrator did need to access these files they will need to take ownership which in turn removes access from the users to their files. The admin will then need to ensure that they need to re-setup the permission on the folder to ensure that they users can still access the files.
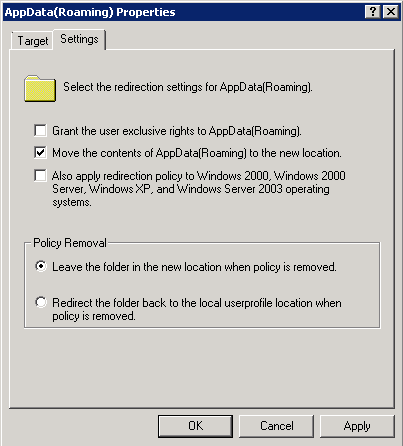
- Only apply redirection policy when you have multiple O/S’s
- Generally recommended for Policy Removal to Leave the folder in the new location when the policy is removed
- The Pictures, Music and Videos Properties page provides an additional options for the folder as seen in the below screenprint: Follow the Documents Folder
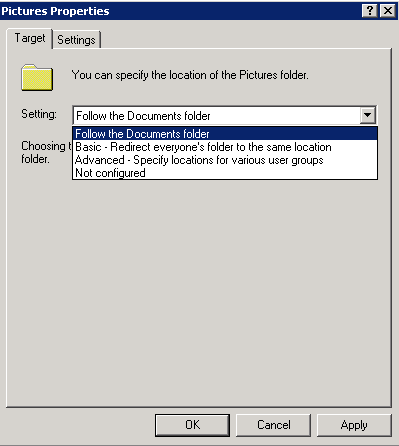
- When it comes to the My Documents/Documents folder there are several options again
- Note: Unlike Windows 2000, you do not need to type in the %username% variable. The folder redirection code will automatically create a My Documents folder for each user, inside a folder based on their user name. For example, type \\FolderServer\MyDocumentsFolders rather than \\FolderServer\MyDocumentsFolders\%username% as you would on Windows 2000.
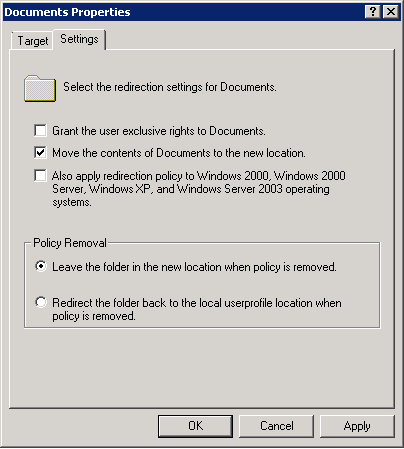
- Click the Settings Tab
- By default, Administrators do not have permissions to users’ redirected folders. If you require the ability to go into the users folders you will want to go to the “Settings” Tab, and uncheck: “Grant the user exclusive rights to” on each folder that is redirected. This allows Administrators to enter the users redirected folder locations without taking ownership of the folder and files.
- Note: If you already have a shared home folder as we set up earlier, it is best not to select Redirect to the Users Home Directory. See Link below for more info
http://support.microsoft.com/kb/321805
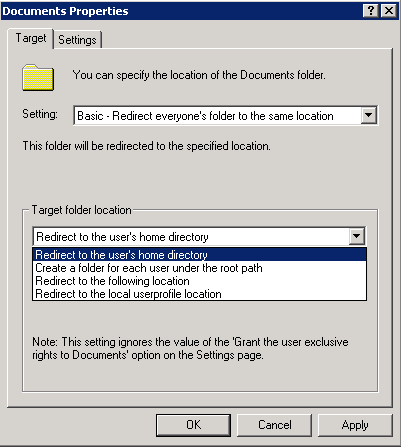
- Go through all the rest of the folders you want to redirect
- Finish
When you enable folder redirection for users for the first time, you will find the logon to be very slow. You are in effect copying the contents of all the user’s personal folders across the network to the server and you can imagine the effect if you are doing this for multiple users at the same time when the login. Before applying this policy to an OU containing hundreds of users, it may be worth creating a new OU and migrating a few users at a time across and will also help you troubleshoot easier without thousands of helpdesk calls about profiles.
You can enable Access based Enumeration however if there is going to a lot of user folders on any one of these shares you could experience degradation of performance. Enabling ABE on a share does come at a price of performance
Other Group Policy Settings
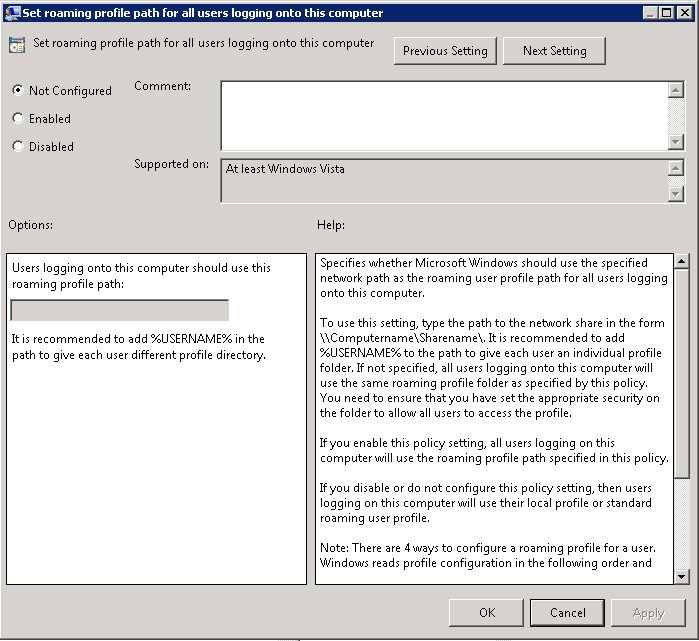
- Setting the same Roaming Profile path for all users logging on
Navigate to Computer Configuration > Policies > Administrative Templates > System > User Profiles and enable the “Set roaming profile path for all users logging onto this computer” and configure the path to the shared folder for profiles.
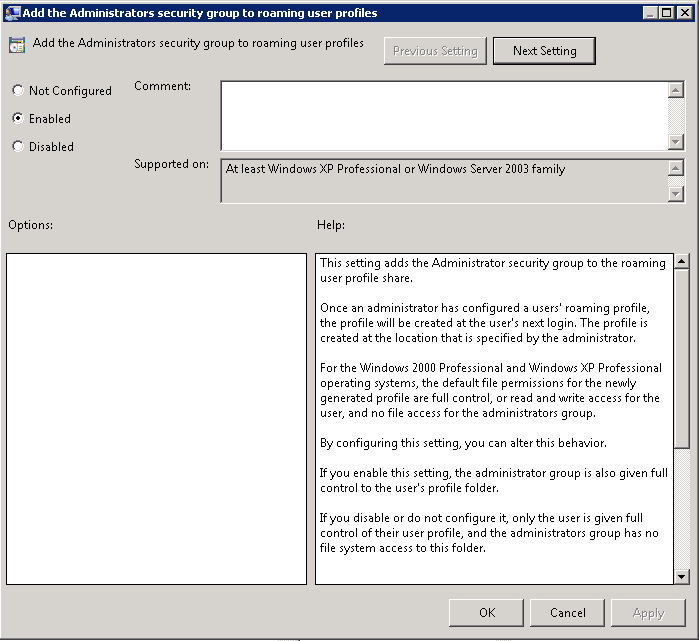
- Add the Administrators Security Group to roaming user profiles
Navigate to Computer Configuration > Policies > Administrative Templates > System > User Profiles and enable the “Add the Administrators Security Group to roaming user profiles”
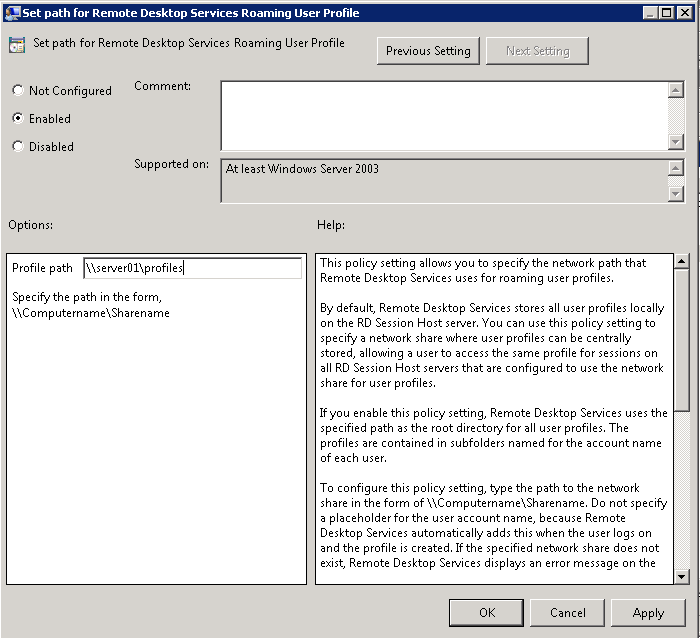
- Set Path for the Remote Desktop Services Roaming User Profile
Navigate to Computer Configuration > Policies > Administrative Templates > Windows Components > Remote Desktop Services > Remote Desktop Session Host\Profiles
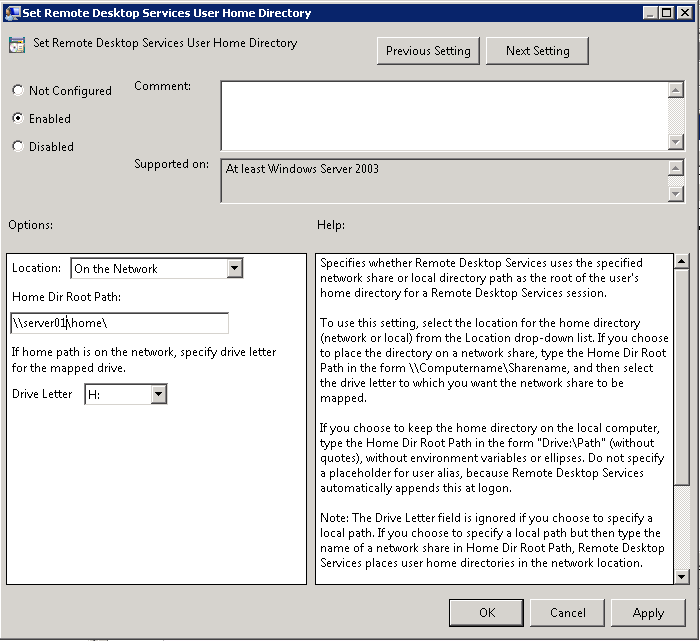
- Set Remote Desktop Services User Home Directory
Navigate to Computer Configuration > Policies > Administrative Templates > Windows Components > Remote Desktop Services > Remote Desktop Session Host\Profiles
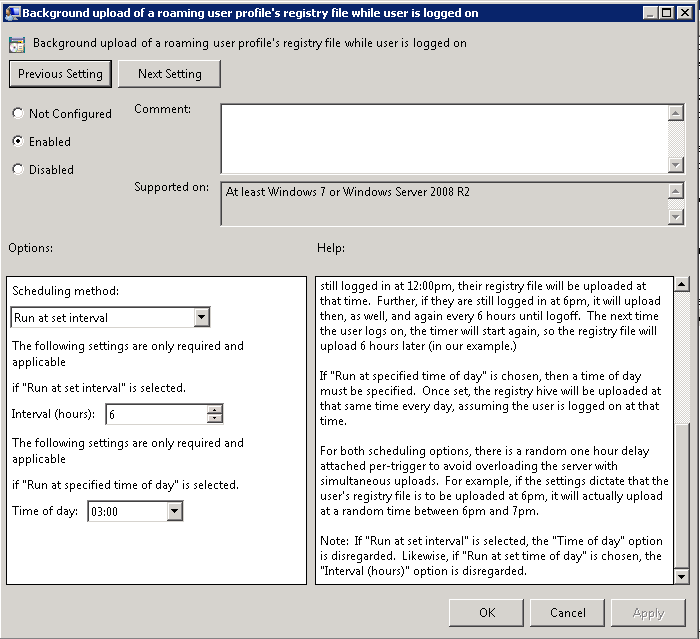
- Background upload of a roaming profile’s registry while user is logged on
Navigate to Computer Configuration > Policies > Administrative Templates > System > User Profiles > Background upload of a roaming profile’s registry while user is logged on
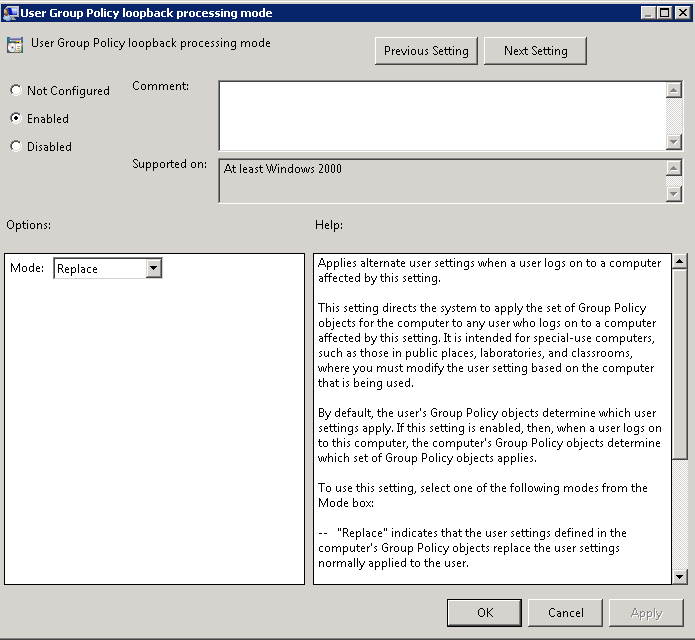
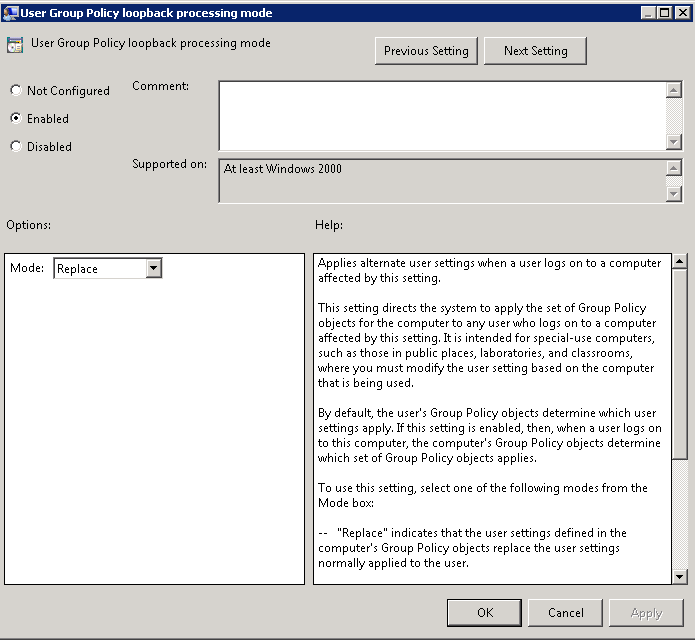
- User Group Policy loopback processing mode
Navigate to: Computer Configuration > Policies > Admin Templates > System > Group Policy and change the following setting: User Group Policy loopback processing mode to Replace
Quotas
Quotas on Profile and Home Directories can be controlled to stop them growing large. Please see the following Blog post for details on setting this up
http://www.electricmonk.org.uk/?s=quota
Issues
- If you set the Group Policy Computer Configuration > Administrative Templates > Windows Components > Remote Desktop Services > Remote Desktop Session Host > Profiles > Set Remote Desktop Services User Home Directory as per below
and
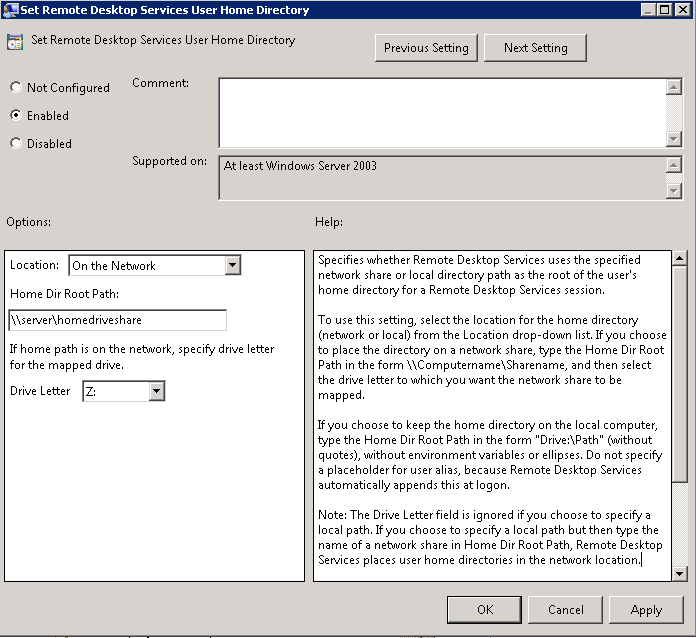
- You will get a folder mapped which is actually \\server\homedrive%username%.%domain%
- The username only folder which is what you actually want when it is mapped not the username.domain folder is created just after the username.domain folder, this is actually when the redirection policy is running. The folder redirection is creating the username directory and you will see the redirected folders underneath this. If you try redirecting to %username%.%userdomain% it starts to mess redirection up.
What can you do?
- You could live with the fact that your \\server\homedrive\%userame% folder is holding the redirected folders and
- You could live with the fact that your \\server\homedrive%username%.%domain% folder is the offiical GPO created tshome folder
- But you can not set this policy at all and simply leave it as unconfigured and set the home drive on the user’s AD Profile as per below
- Then it setups correctly and you’ll see all your redirected folders in here as well.