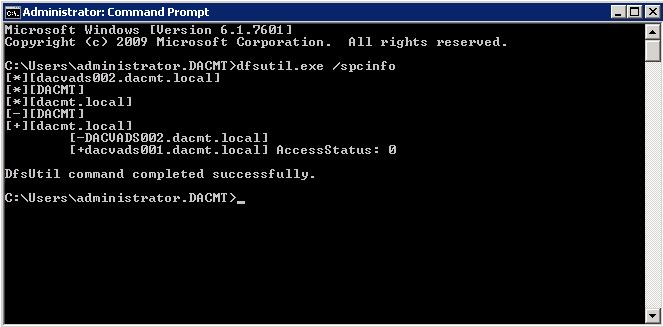
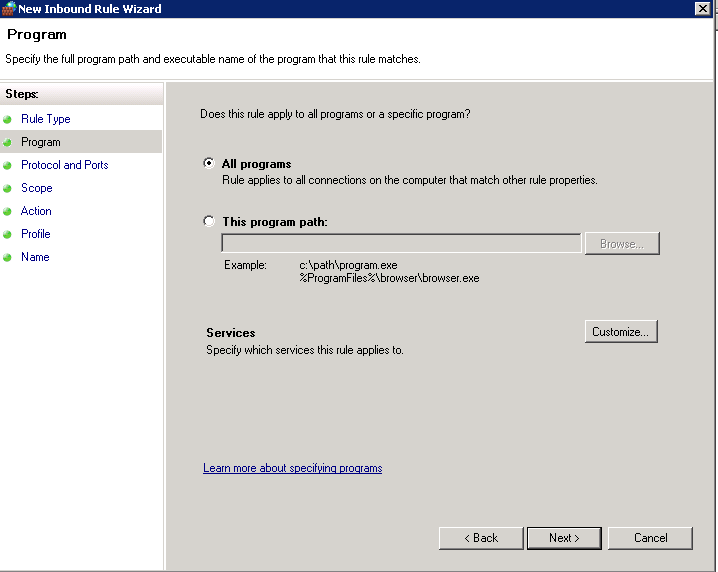
What is File Auditing?
In order to track file and folder access on Windows Servers, it is necessary to enable file and folder auditing and then identify the files and folders that are to be audited. Once correctly configured, the server security logs will then contain information about attempts to access or otherwise manipulate the designated files and folders. It is important to note that file and folder auditing is only available for NTFS volumes.
In Windows Server 2008 R2 and Windows 7, all auditing capabilities have been integrated with Group Policy. This allows administrators to configure, deploy, and manage these settings in the Group Policy Management Console (GPMC) or Local Security Policy snap-in for a domain, site, or organizational unit (OU). Windows Server 2008 R2 and Windows 7 make it easier for IT professionals to track when precisely defined, significant activities take place on the network.
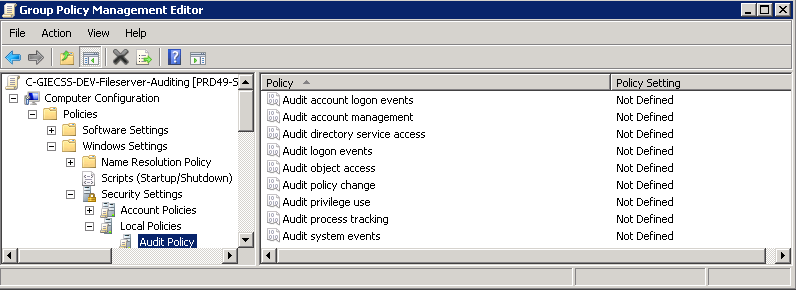
The nine basic audit policies under Computer Configuration\Policies\Windows Settings\Security Settings\Local Policies\Audit Policy allow you to configure security audit policy settings for broad sets of behaviors, some of which generate many more audit events than others. An administrator has to review all events that are generated, whether they are of interest or not.
In Windows Server 2008 R2 and Windows 7, administrators can audit more specific aspects of client behavior on the computer or network, thus making it easier to identify the behaviors that are of greatest interest. For example, in Computer Configuration\Policies\Windows Settings\Security Settings\Local Policies\Audit Policy, there is only one policy setting for logon events, Audit logon events. In Computer Configuration\Policies\Windows Settings\Security Settings\Advanced Audit Policy Configuration\System Audit Policies, you can instead choose from eight different policy settings in the Logon/Logoff category. This provides you with more detailed control of what aspects of logon and logoff you can track
Planning
In addition, to plan and deploy security event auditing policies, administrators need to address a number of operational and strategic questions, including:
- Why do we need an audit policy?
- Which activities and events are most important to our organization?
- Which types of audit events can we omit from our auditing strategy?
- How much administrator time and network resources do we want to devote to generating, collecting, and storing events, and analyzing the data?
Requirements
- Auditing has to be enabled in the system’s security policy and in the Access Control List of a resource to successfully log events
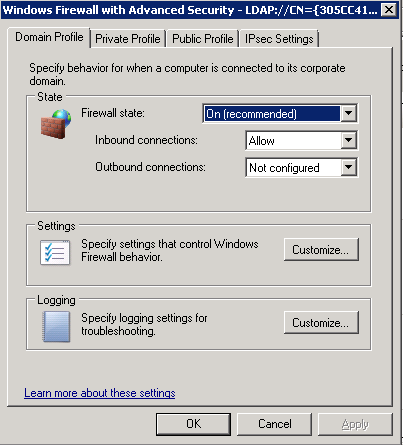
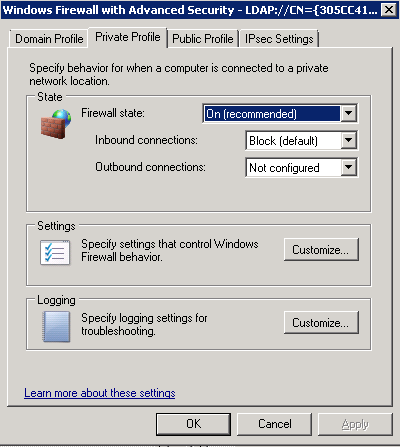
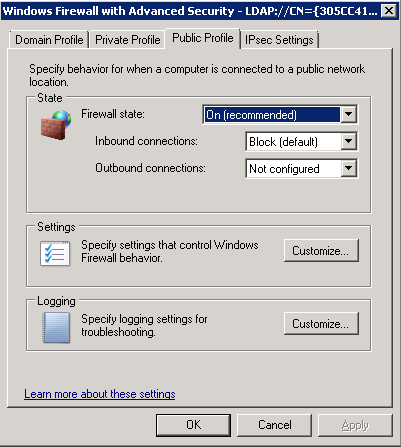
- Audit policy can be enabled either through group policy or the local security policy
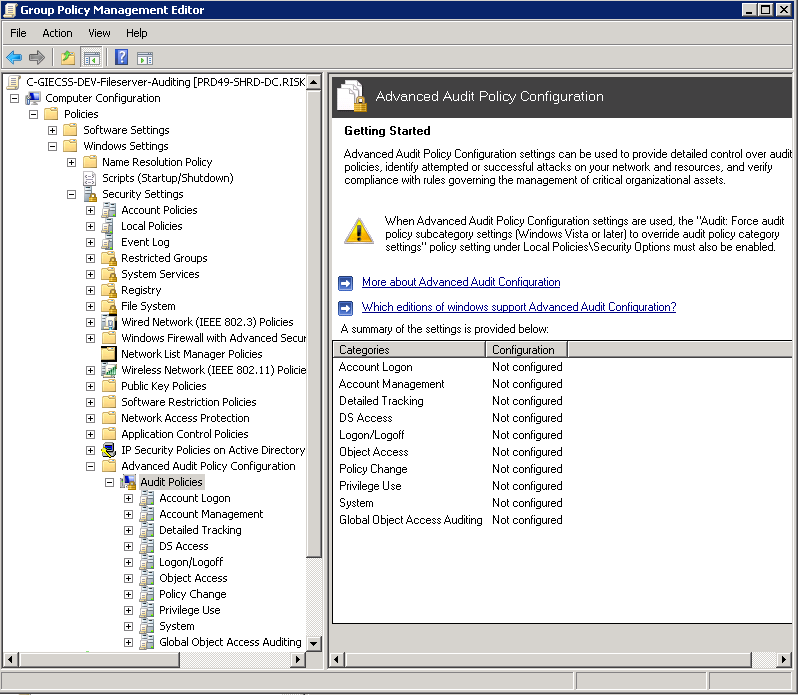
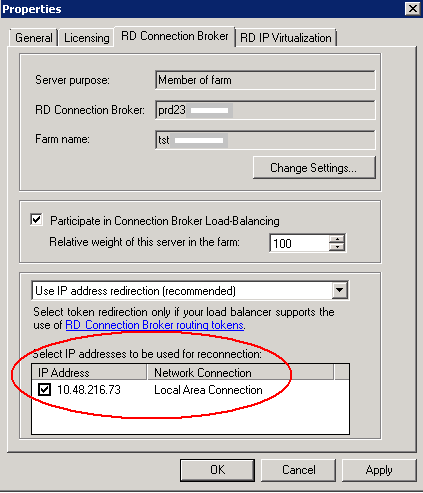
- If this is a Windows Server 2008 R2 or later operating system I recommend using the Advanced Audit Policy Configuration (Computer Configuration\Windows Settings\Security Settings\Advanced Audit Policy Configuration\Audit Policies\) as opposed to the older Audit Policy (Computer Configuration\Windows Settings\Security Settings\Local Policies\Audit Policy\)
- Do not mix use of both Advanced Audit Policy Configuration and the older Audit Policy: If you enable audit policy through Advanced Audit Policy Configuration either through group policy or the local security policy, I recommend using the Advanced Audit Policy Configuration at every level (local policy, site, domain and OU-linked group policy)
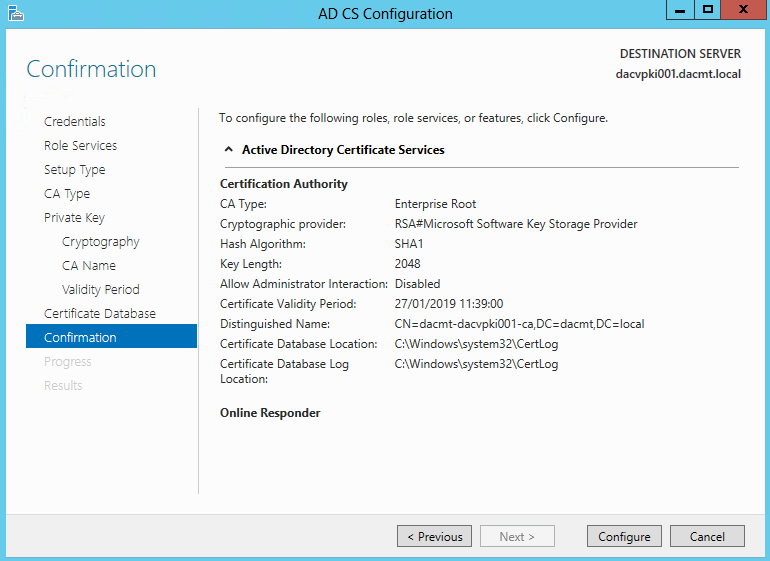
Configuring an Advanced Audit Policy
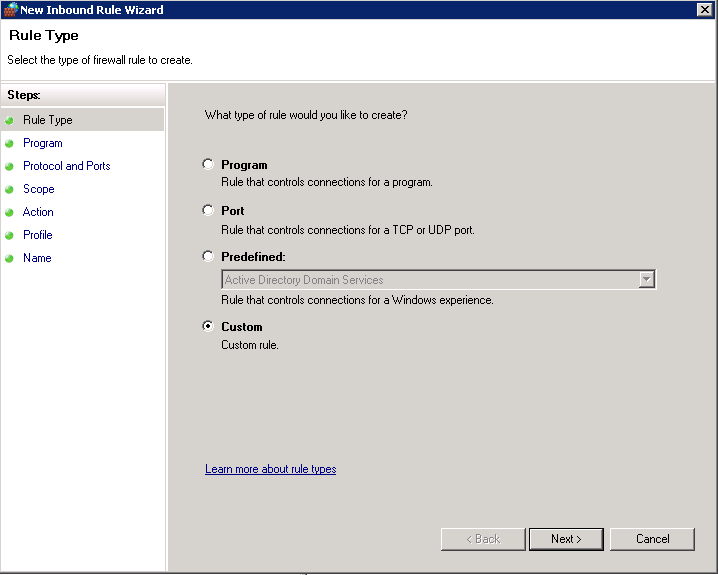
- Create a Group Policy Object and name it something to the effect of File Server Audit Policy
- Edit the GPO, browse to Computer Configuration\Windows Settings\Security Settings\Advanced Audit Policy Configuration\Audit Policies
- For more information on each setting click the following link
- http://technet.microsoft.com/en-us/library/dd772712%28v=ws.10%29.aspx
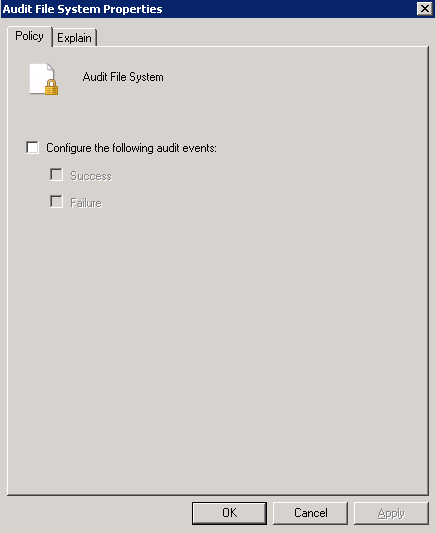
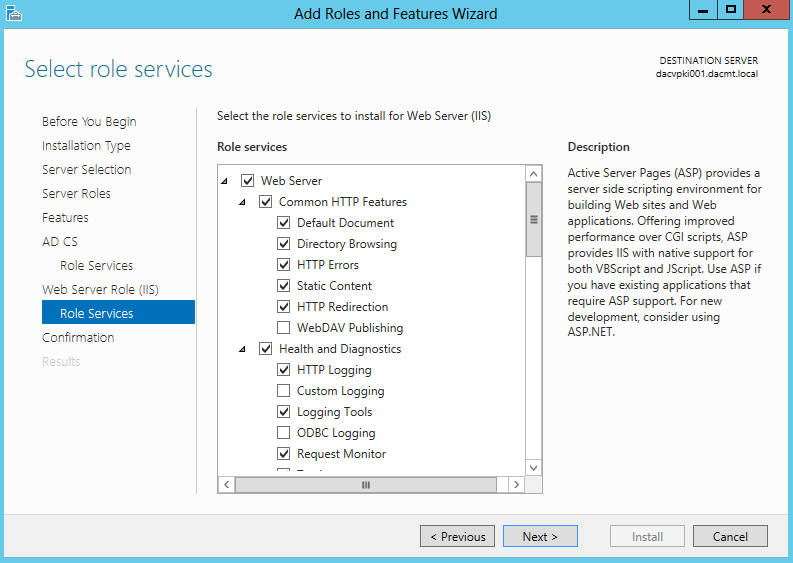
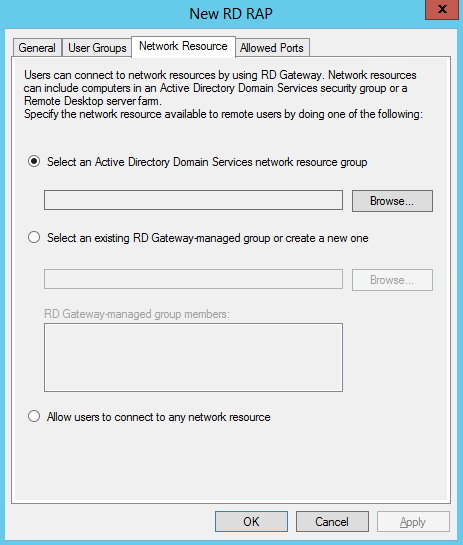
- Select Object Access
- In the Sub Category, select Audit File System. Put a tick in Configuring the following audit events and select whether you want to audit for Success or Failure
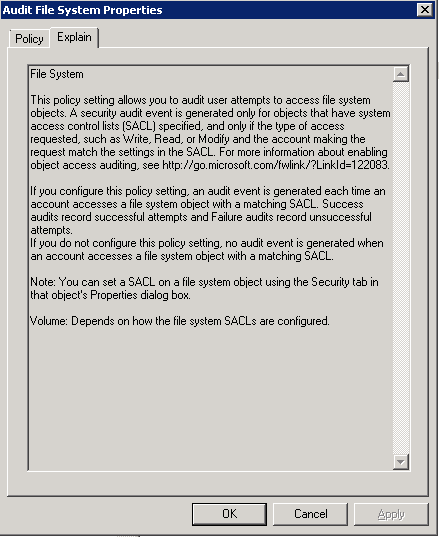
- If you click on Explain, this will tell you exactly what this policy does
- Once file and folder access auditing has been enabled the next step is to configure which files and folders are to be audited. As with permissions, auditing settings are inherited unless otherwise specified. By default, configuring auditing on a folder will result in access to all child subfolders and files also being audited. Just as with inherited permissions, the inheritance of auditing settings can be tuned off for either all, or individual files and folders.
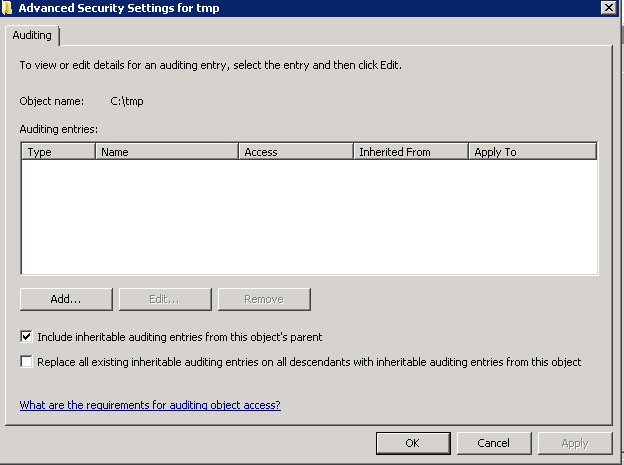
- To configure auditing for a specific file or folder begin by right clicking on it in Windows Explorer and selecting Properties. In the properties dialog, select the Security tab and click on Advanced. In the Advanced Security Settings dialog select the Auditing tab. Auditing requires elevated privileges. If not already logged in as an administrator click the Continue button to elevate privileges for the current task. At this point, the Auditing dialog will display the Auditing entries list containing any users and groups for which auditing has been enabled as shown below.
- You can add Active Directory Security Groups or you can put the Everyone Group
- Use the drop down list to control whether the auditing setting is to be applied to the current file or folder, or whether it should propagate down to all children files and/or sub-folders. Once configured, click on OK to dismiss current dialog and then Apply the new auditing settings in the Auditing Entries dialog.
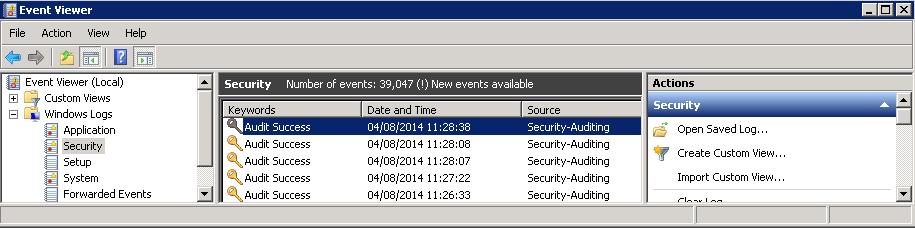
- From this point on, access attempts on the selected file or folder by the specified users and groups of the types specified will be recorded in the server’s security logs which may be accessed using the Events Viewer
Links
http://technet.microsoft.com/en-us/library/dd560628%28v=ws.10%29.aspx