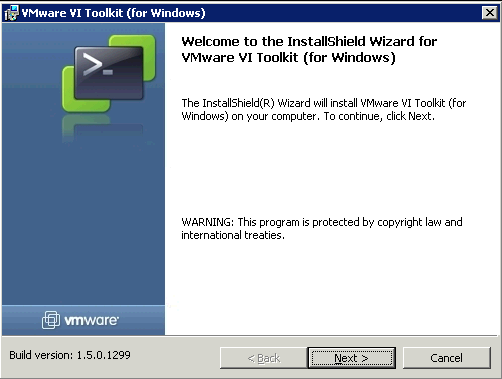
The ESXi Firewall
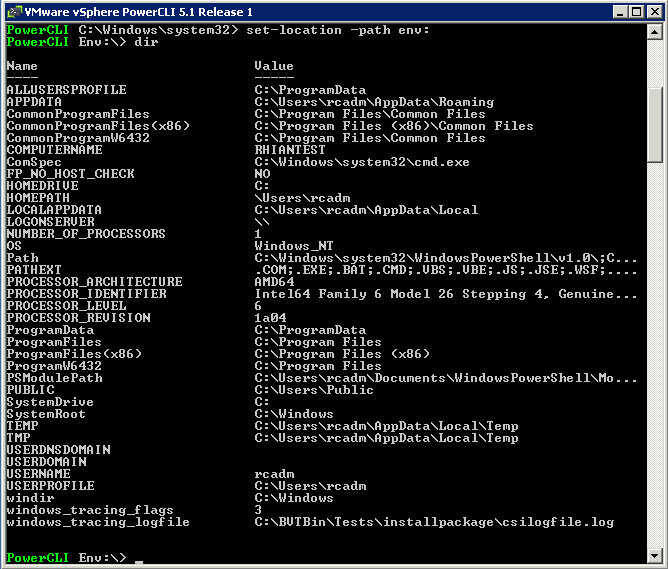
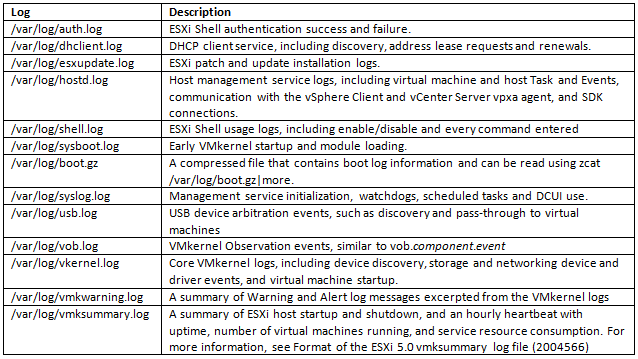
Supported services and management agents that are required to operate the host are described in a rule set configuration file in the ESXi firewall directory /etc/vmware/firewall/. The file contains firewall rules and lists each rule’s relationship with ports and protocols.
By default, when ESXi is installed, the firewall is enabled. The default configuration is to permit only the required operational traffic and to deny all other
Identify esxcli firewall configuration commands
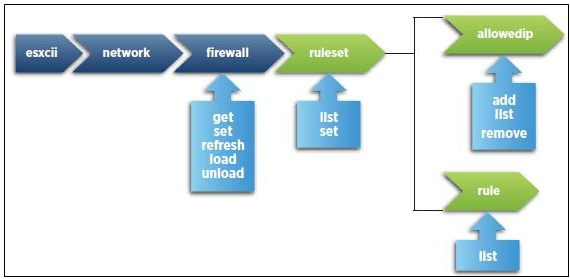
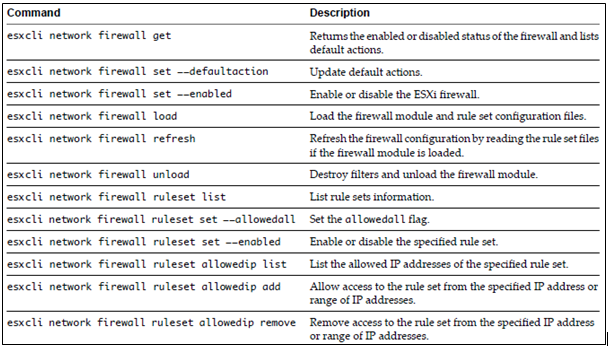
Example Commands of esxcli network firewall
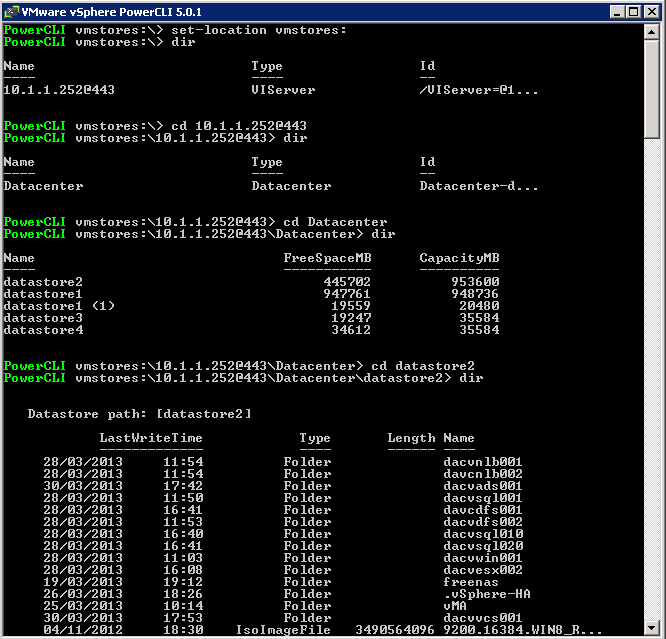
List Firewall Rules
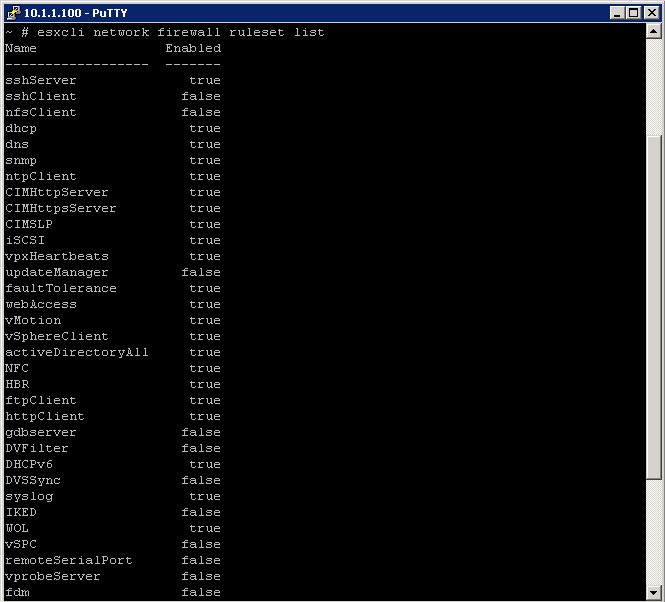
- esxcli network firewall ruleset list
Enable and Disable the FTP Client Rulset
- esxcli network firewall ruleset set –ruleset-id ftpClient –enabled true
- esxcli network firewall ruleset set –ruleset-id ftpClient –enabled false
Explain the three Firewall Security Levels
Enable/Disable pre-configured services

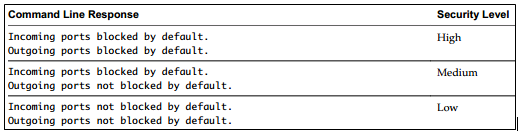
Configure service behavior automation
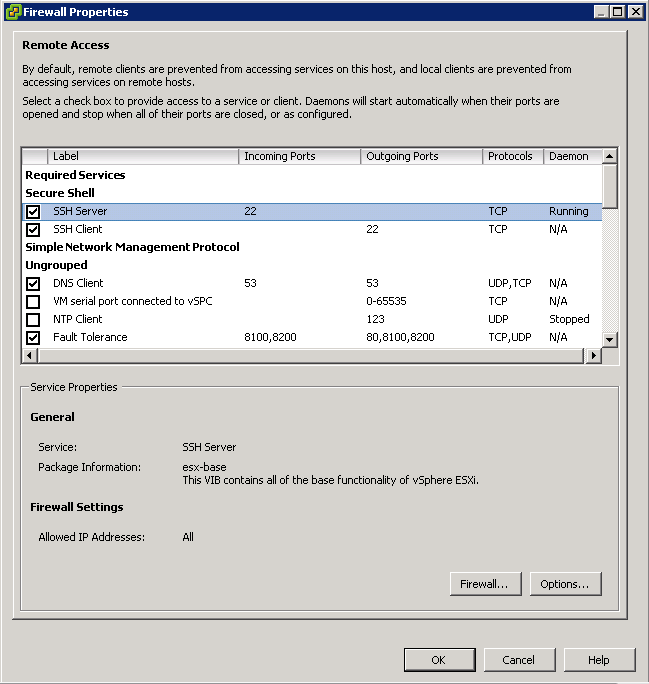
Select a host > Configuration > Software > Security Profile > Services > Properties > Options
- Start automatically if any ports are open, and stop when all ports are closed: The default setting for these services that VMware recommends. If any port is open, the client attempts to contact the network resources pertinent to the service in question. If some ports are open, but the port for a particular service is closed, the attempt fails, but there is little drawback to such a case. If and when the applicable outgoing port is opened, the service begins completing its tasks.
- Start and stop with host: The service starts shortly after the host starts and closes shortly before the host shuts down. Much like Start automatically if any ports are open, and stop when all ports are closed, this option means that the service regularly attempts to complete its tasks, such as contacting the specified NTP server. If the port was closed but is subsequently opened, the client begins completing its tasks shortly thereafter.
- Start and stop manually: The host preserves the user-determined service settings, regardless of whether ports are open or not. When a user starts the NTP service, that service is kept running as long as the host is powered on. If the service is started and the host is powered off, the service is stopped as part of the shutdown process.
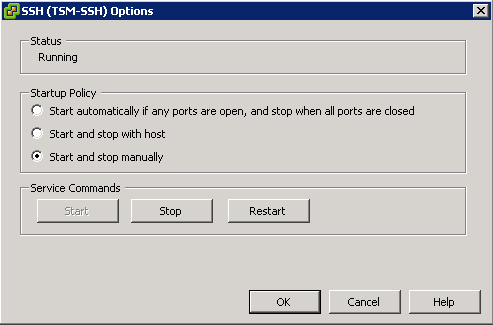
Open/Close ports in the firewall
- Login to vSphere client
- Enter the Hosts and Clusters View
- Select a host
- Click the Configuration tab
- Under the Software view, select Security Profile
- Under Security Profile > Firewall, click Properties
- Highlight a service
- To enable a firewall rule, check the check box next to the traffic label
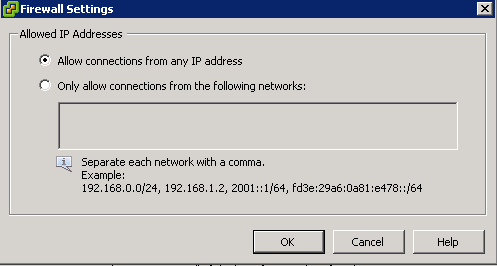
Allowing connections from an IP Address or a network
- All connections may be allowed or it can be restricted to a single IPv4 or IPv6 addresses and/or IPv4 or IPv6 networks.
Example esxcli network firewall commands
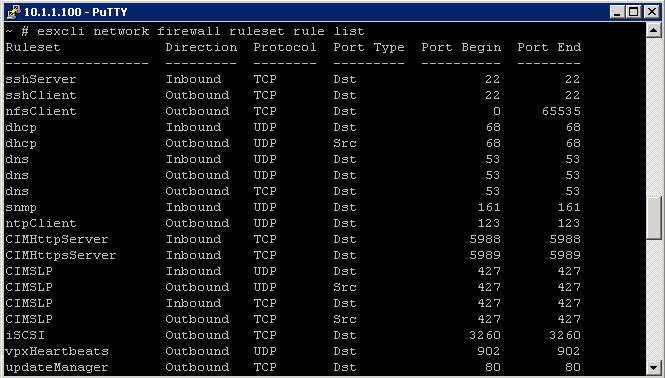
List the Firewall rules and their ports
- esxcli network firewall ruleset rule list
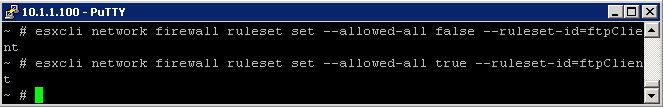
Disable and Enable the All IPs allowed rule for the ftpClient Rule
- esxcli network firewall ruleset set –allowed-all false –ruleset-id=ftpClient
- esxcli network firewall ruleset set –allowed-all true –ruleset-id=ftpClient
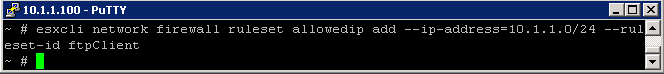
Specify an allowed network range 10.1.1./24 for the ftpClient Firewall Rule
- esxcli network firewall ruleset allowedip add –ip-address=10.1.1.0/25 –ruleset-id ftpClient
Create a custom service
Rule set configuration files are located in the /etc/vmware/firewall directory and you will see there are 2 files there already
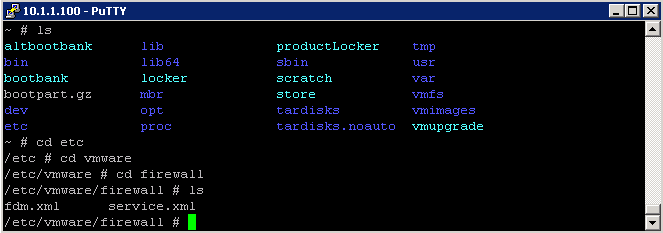
Create a custom service file for a service
- Log into WinSCP and navigate to /etc/vmware/firewall/
- Copy the service.xml file to your machine
- I copied the format for an individual service within the service.xml file and created a new Wordpad file initially where I adjusted the service id to a unique ID, the id to my service name – RhianService and chose a new port number 800
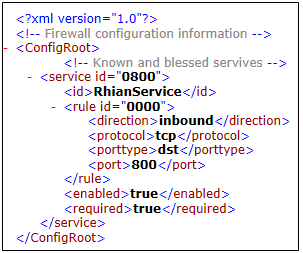
- I then saved the file as RhianService.xml
- Next copy this file to the /etc/vmware/firewall directory
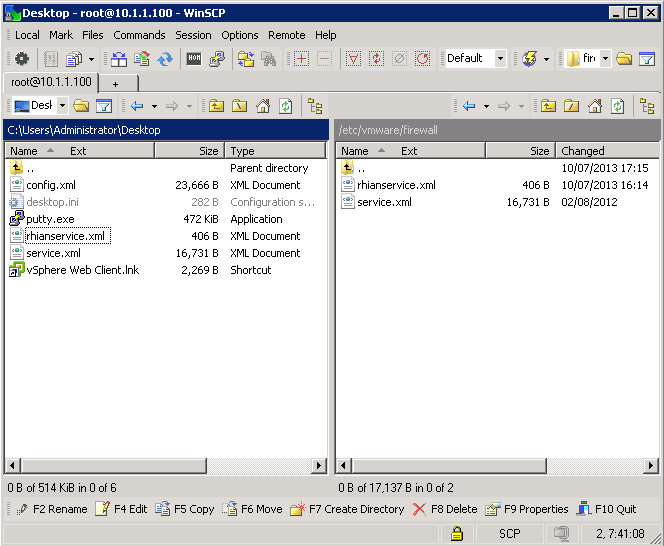
- Next Putty into your host and run the following commands as seen in the screenprint below
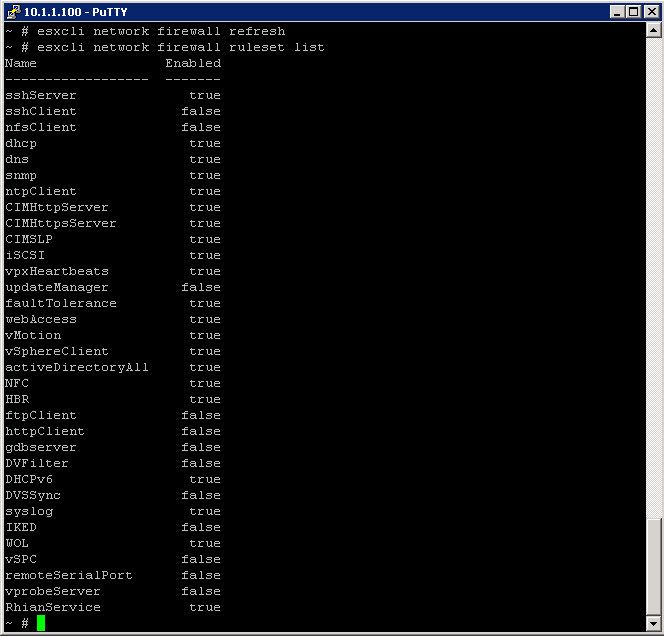
- esxcli network firewall refresh
- esxcli network firewallrulset list and you should see your new service
- In vCenter look at Configuration > Software > Security Profile. You should see your custom profile
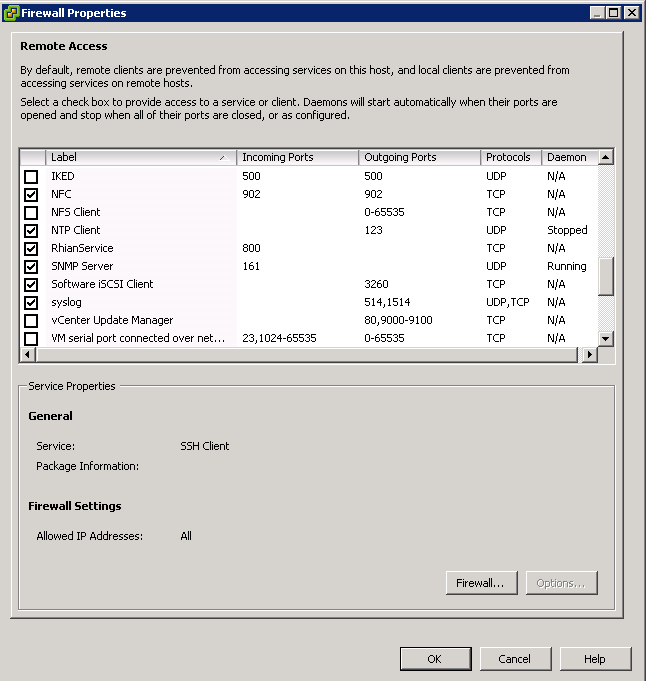
Adding a Custom Service
To add a service to the host security profile, VMware partners can create a VIB that contains the port rules for the service in a configuration file. VIB authoring tools are available to VMware partners only. Each set of rules for a service in the rule set configuration file contains the following information
- A numeric identifier for the service, if the configuration file contains more than one service.
- A unique identifier for the rule set, usually the name of the service.
- For each rule, the file contains one or more port rules, each with a definition for direction, protocol, port type, and port number or range of port numbers.
- An indication of whether the service is enabled or disabled when the rule set is applied.
- An indication of whether the rule set is required and cannot be disabled
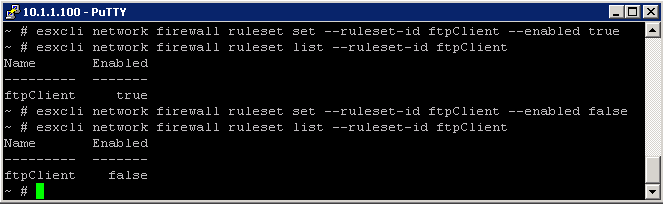
Set Firewall Security Level
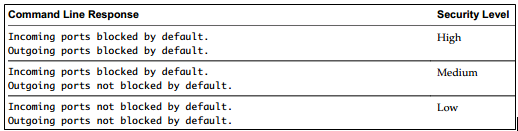
- High Security (Default) – Firewall is configured to block all incoming and outgoing traffic, except for ports 22,123,427,443,902,5989, and 5988. These are ports used for basic ESXi communication
- Medium Security – All incoming traffic is blocked, except on the default ports and any ports you specifically open. Outgoing traffic is not blocked
- Low Security – There are no ports blocked on either incoming or outgoing traffic. This setting is equivalent to removing the fireall
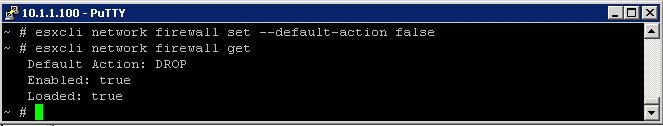
Set High
- esxcli network firewall set –default-action false
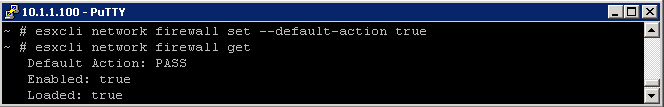
Set Low
- esxcli network firewall set –default-action true
Restart hostd at the command line following Security Level changes by typing service mgmt-vmware restart