What does SAML stand for?
Security Access Markup Language
What is SAML used for?
SAML is an XML-based open-standard for transferring identity data between two parties: an identity provider and a service provider. SAML enables Single-Sign On (SSO), a term that means users can log in once, and those same credentials can be reused to log into other service providers. The OASIS Consortium approved SAML v2 in 2005. SAML 2.0 changed significantly from 1.1 and the versions are incompatible.
What is XML used for in relation to SAML?
SAML transactions use Extensible Markup Language (XML) to communicate between the identity provider and service providers. SAML is the link between the authentication of a user’s identity and the authorization to use a service.
How does authentication and authorization work in SAML?
SAML implements a secure method of transferring user authentications and authorizations between the identity provider and service providers. When a user logs into a SAML enabled application, the service provider requests authorization from the appropriate identity provider. The identity provider authenticates the user’s credentials and then returns the authorization for the user to the service provider, and the user is now able to use the application.
SAML authentication is the process of checking the user’s identity and credentials. SAML authorization tells the service provider what access to grant the authenticated user.
What is a SAML provider?
There are two primary types of SAML providers, service provider, and identity provider.
- The identity provider carries out the authentication and passes the user’s identity and authorization level to the service provider.
- A service provider needs the authentication from the identity provider to grant authorization to the user.
Advantages of SAML
- Users only need to sign in once to access several service providers. This means a faster authentication process and the user does not need to remember multiple login credentials for every application.
- SAML provides a single point of authentication
- SAML doesn’t require user information to be maintained and synchronized between directories.
- Identity management best practices require user accounts to be both limited to only the resources the user needs to do their job and to be audited and managed centrally. Using an SSO solution will allow you to disable accounts and remove access to resources simultaneously when needed.
Visualising SAML
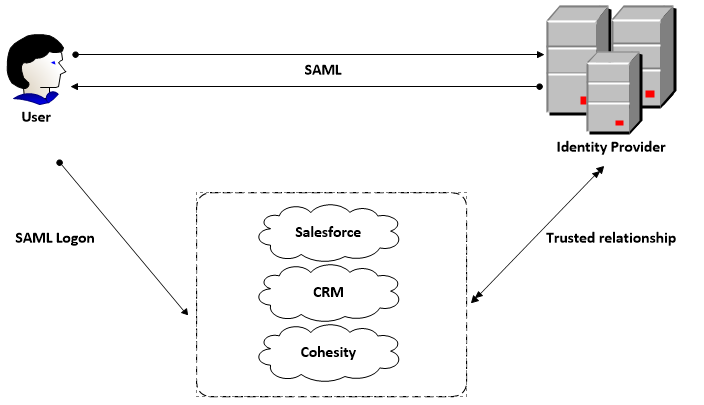
SAML Example
SAML uses a claims-based authentication workflow. When a user tries to access an application or site, the service provider asks the identity provider to authenticate the user. Then, the service provider uses the SAML assertion issued by the identity provider to grant the user access.
- The user opens a browser and navigates to the service provider’s web application, which uses an identity provider for authentication.
- The web application responds with a SAML request.
- The browser passes the SAML request to the identity provider.
- The identity provider parses the SAML request.
- The identity provider authenticates the user by prompting for a username and password or some other authentication factor. NOTE: The identity provider will skip this step if the user is already authenticated.
- The identity provider generates the SAML response and returns it to the user’s browser.
- The browser sends the generated SAML response to the service provider’s web application which verifies it.
- If the verification succeeds, the web application grants the user access.

