
What problem do I need to solve?
I have a vSphere 6.7U3 cluster using vSAN and VM encryption. I need to move the vSAN cluster to another vCenter. The new vCenter is set up with the same Thales KeySecure KMS server as the original vCenter I am migrating from. The machines all copy over fine and will boot and be accessible however they cannot vMotion between any other hosts. This is because the KeySecure server keys for these VMs are permissioned to the old vCenter and not the new vCenter. While doing a test of 3 VMs means we could simply reapply permisssions to these 3 VMs on the KeySecure KMS server, this is definitely not practical for 1000s of VMs. What I’m going to test today is a shallow and deep rekey of my test VMs to see if I can force them to rekey using the new vCenter.
Link for migrating vSAN Clusters
https://kb.vmware.com/s/article/2151610
How do we get started with this?
Some great folks at VMware have created a PowerCLI module called VMware.VMEncryption. This can be found at the githib link below
https://github.com/vmware/PowerCLI-Example-Scripts/tree/master/Modules/VMware.VMEncryption
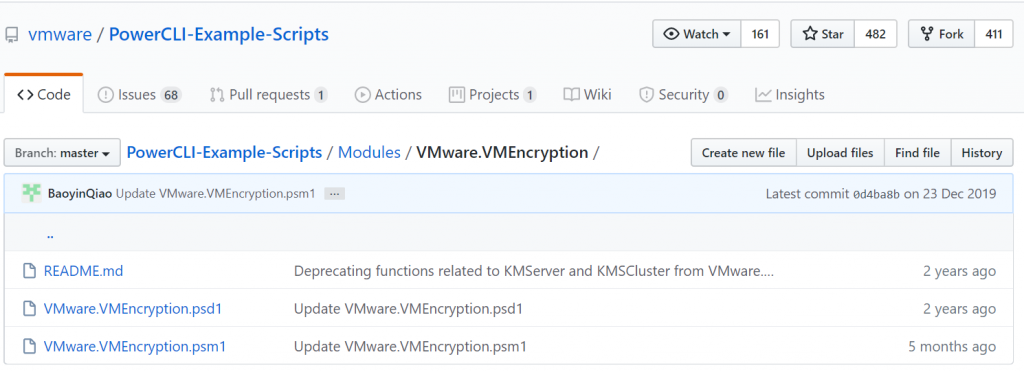
Prerequisites/Steps to use this module
- This module only works for vSphere products that support VM Encryption. E.g. vSphere 6.5 and later.
- All the functions in this module only work for KMIP Servers.
- Install the latest version of Powershell and PowerCLI.
- Import this module by running: Import-Module -Name “location of this module”
- Get-Command -Module VMware.VMEncryption to list all available functions.
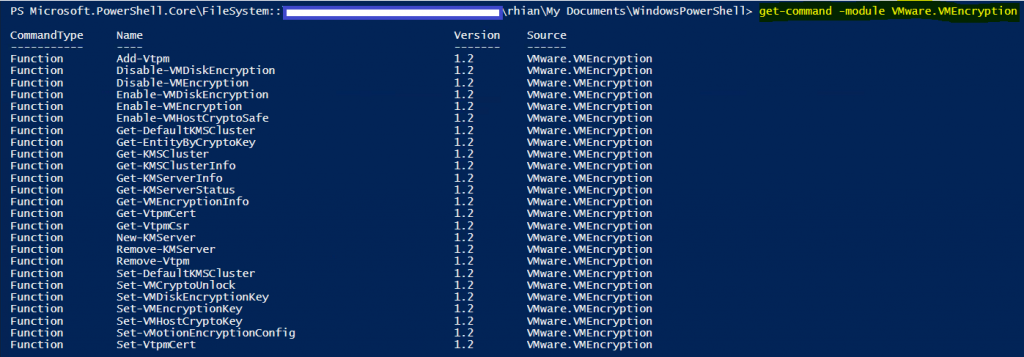
Steps to get started
- You want to save the VMware.VMEncryption modules in the correct place that PowerShell expects to find the module. to check this, type $env:PSModulePath in Powershell
- Open PowerShell and type import-module VMware.VMEncryption
- To check if it has loaded and also to check any other modules, type get-module VMware* -ListAvailable
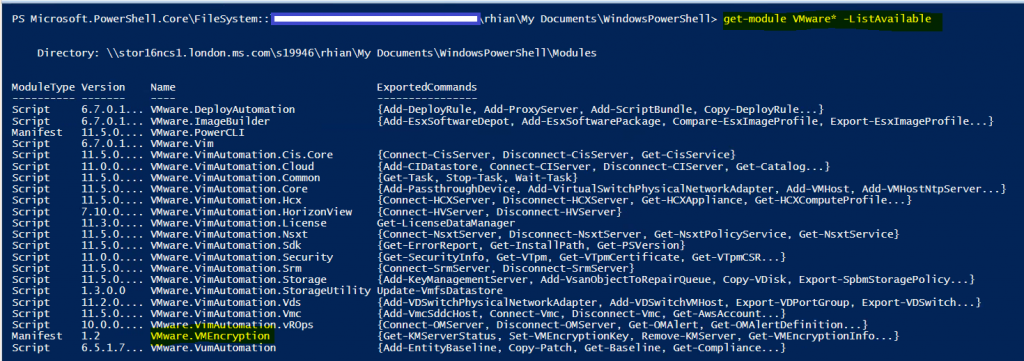
- Connect to your new vCenter using the connect-viserver <vcenter-server> command
- Run the following command to do a shallow rekey
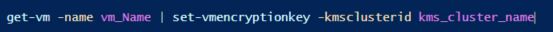
- Test a vMotion – All looks good.
Automating the shallow rekeying of VMs in this situation
All credit to James Doyle for providing a blog 2 PowerCLI scripts on GitHub to apply the rekeying on all VMs needed in a cluster. Details below
https://thevirtualpaddy.wordpress.com/2017/08/23/vmware-vm-encryption-powershell-scripts
https://github.com/jameseydoyle/VMware-VM-Encryption-Powershell-scripts/
Useful PowerCLI commands for viewing keys
(get-view -id $(get-vmhost esxihostname).ExtensionData.ConfigManager.CryptoManager).ListKeys($null)
(get-view -id $(get-viserver vcenter-name).ExtensionData.ConfigManager.CryptoManager).ListKeys($null)
(get-vm vmname).ExtensionData.Config.keyID
get-vmhost | select Name,KMSserver
Checking the vCenter logs for problems associated with encryption
grep -i cryptomanager /var/log/vmware/vpxd/vpxd.log

