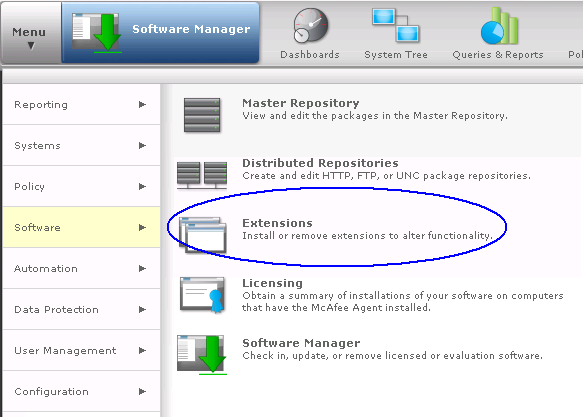
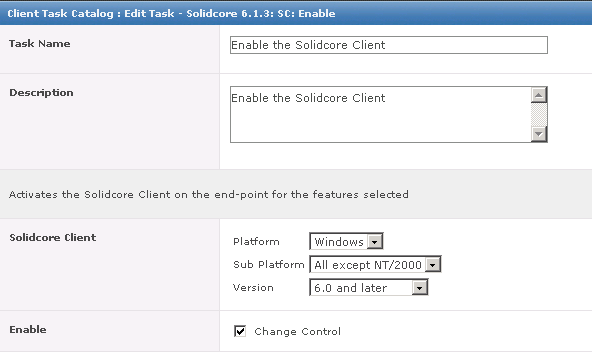
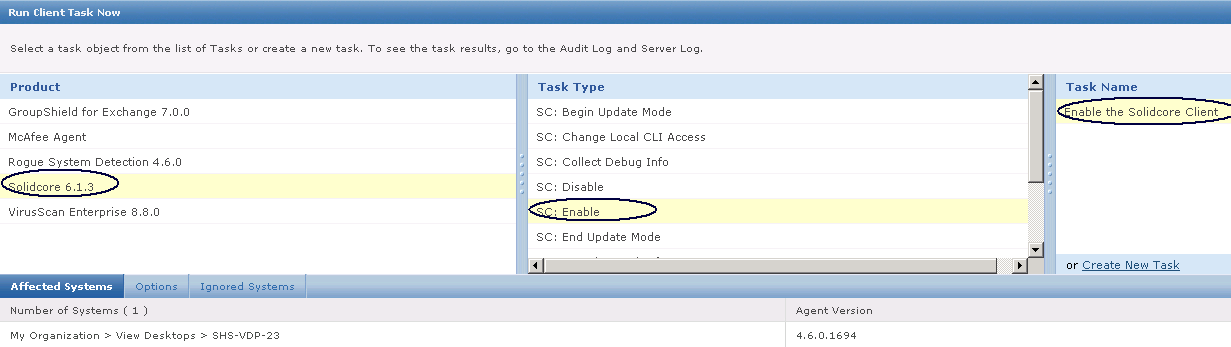
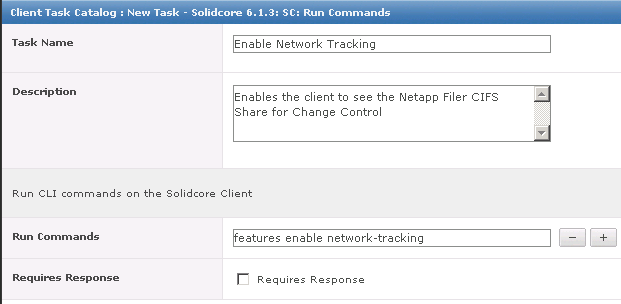
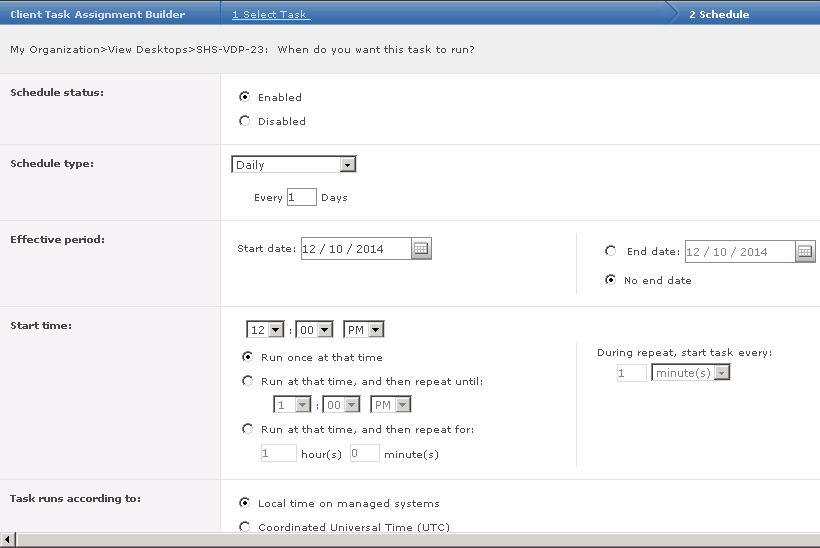
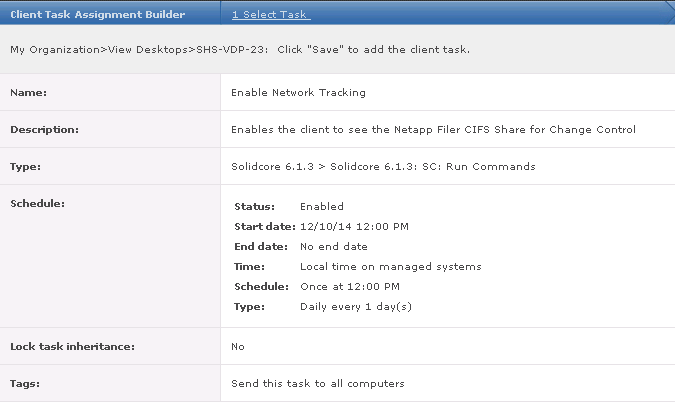
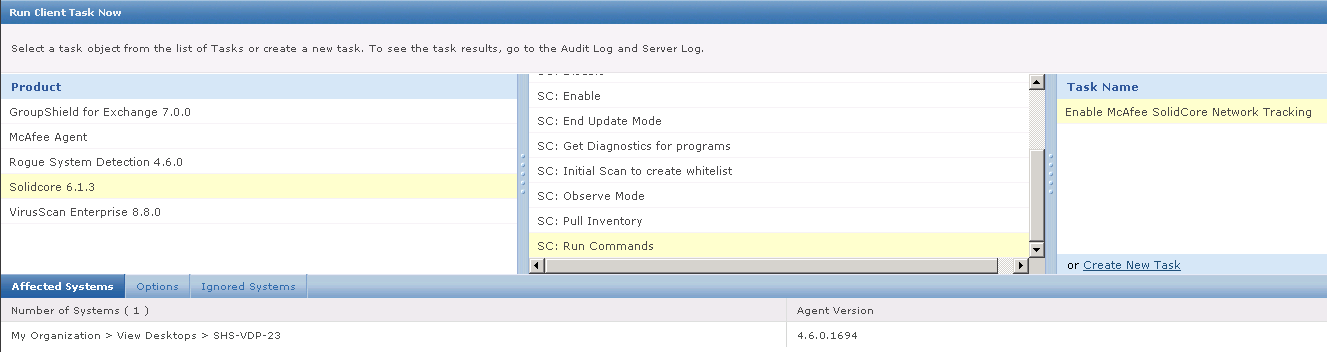
What is HttpWatch?
HttpWatch is an HTTP sniffer for IE, Firefox, iPhone & iPad that provides new insights into how your website loads and performs. All web applications make extensive use of the HTTP protocol (or HTTPS for secure sites). Even simple web pages require the use of multiple HTTP requests to download HTML, graphics and javascript. The ability to view the HTTP interaction between the browser and web site is crucial to these areas of web development.
We needed to use this software to see what underlying sites a main site was linking to as we used Kerio Web Proxy which was blocking some websites we couldn’t see and needed to add to a whitelist.
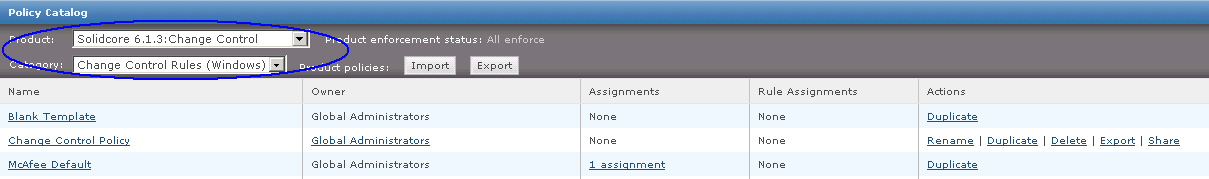
HttpWatch Features
- Easily monitor HTTPS, HTTP and SPDY without using proxies or changing network settings
- Supports IE/Firefox on Windows and iOS app for iPhone / iPad
- Real-time page and request level time charts
- Users and customers can send you log files for free
- Automatically detects potential configuration, performance and security related issues on your web server
- Can be automated using most programming languages, e.g. C#, Ruby, Javascript, Ruby
- Provides millisecond accurate timings
HttpWatch has two components; a plug-in used to collect, view and save HTTP traffic within IE or Firefox, and a standalone log file viewer know as HttpWatch Studio.
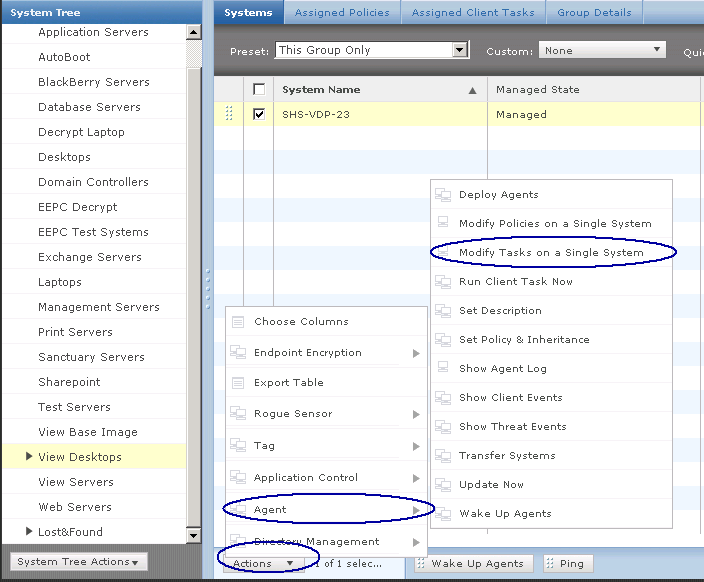
How can HttpWatch Help?
- HttpWatch integrates with Internet Explorer and Firefox browsers to show you exactly what HTTP traffic is triggered when you access a web page. If you access a site that uses secure HTTPS connections, HttpWatch automatically displays the decrypted form of the network traffic.
- Conventional network monitoring tools just display low level data captured from the network. In contrast, HttpWatch has been optimized for displaying HTTP traffic and allows you to quickly see the values of headers, cookies and query strings.
HttpWatch also supports non-interactive examination of HTTP data. When log files are saved, a complete record of the HTTP traffic is saved in a compact file. You can even examine log files that your customers and suppliers have recorded using the free basic edition.
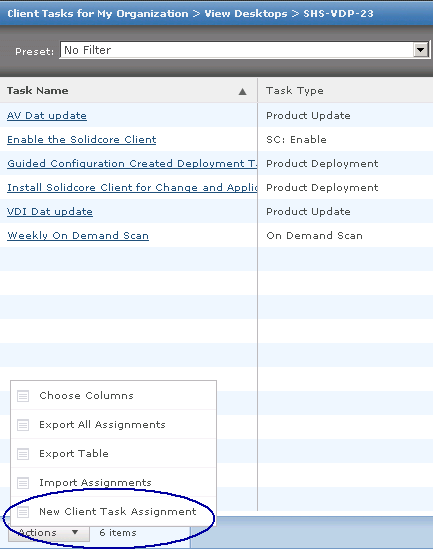
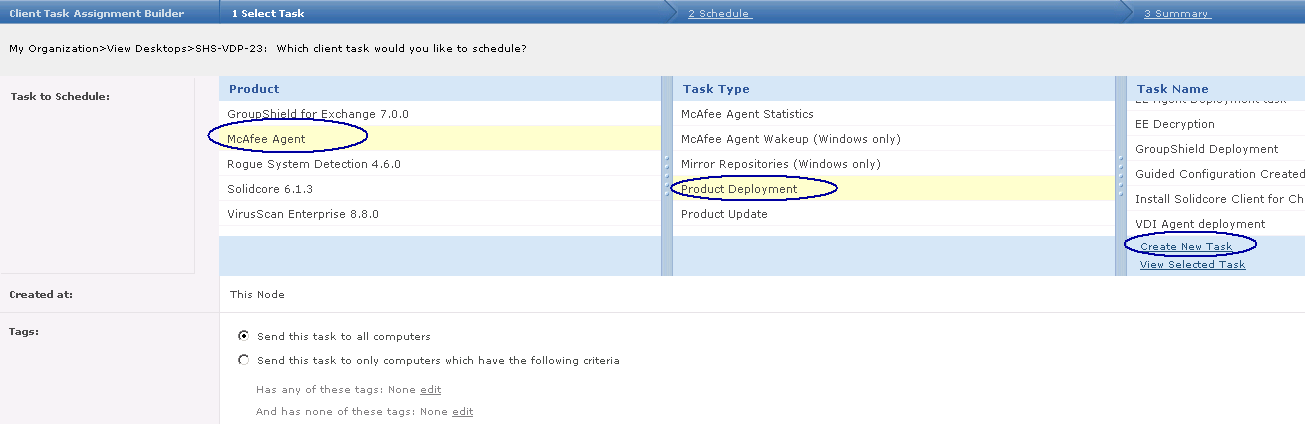
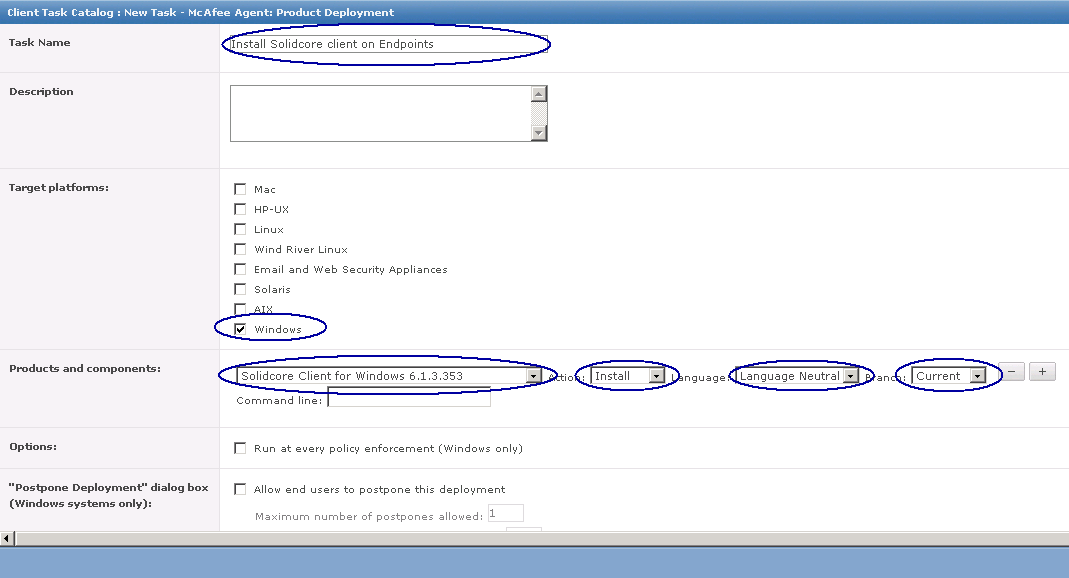
How to use HttpWatch
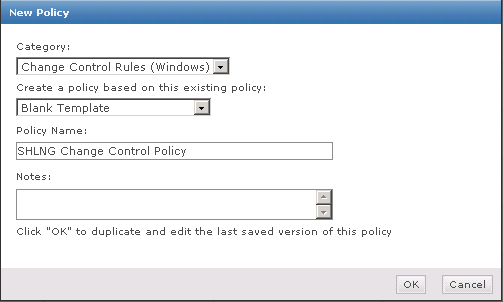
- Install from the website listed above
- If you are not able to access HttpWatch using one of the methods below please check that all HttpWatch entries are enabled in the Tools->Add-ons window of each browser/.
- Also, with IE it may also be necessary to restart Windows before the HttpWatch plug-in is correctly installed
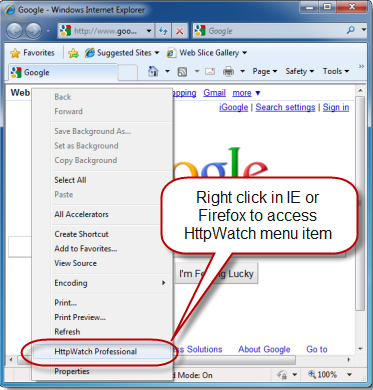
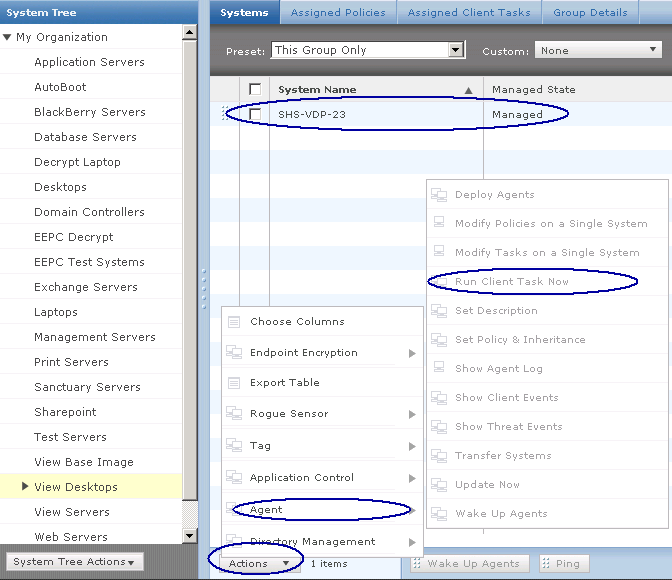
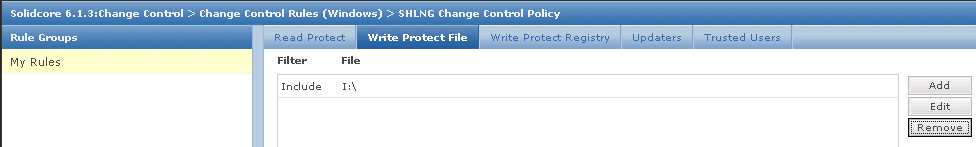
- The HttpWatch plug-in can be displayed in the lower part of the Internet Explorer (IE) or Firefox window by using one of the following methods:
- Right click in a webpage and select HttpWatch Basic or HttpWatchProfessional
or
- Use the shortcut key Shift+F2
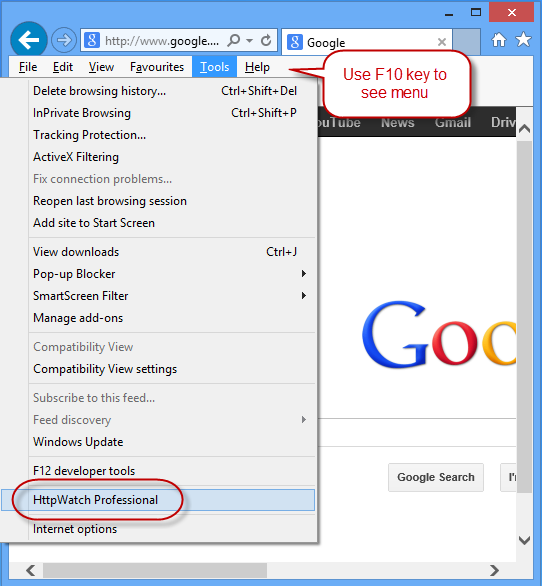
- Use the HttpWatch menu item on the Tools menu. In later versions of IE and Firefox you may need to press F10 to display the menu:
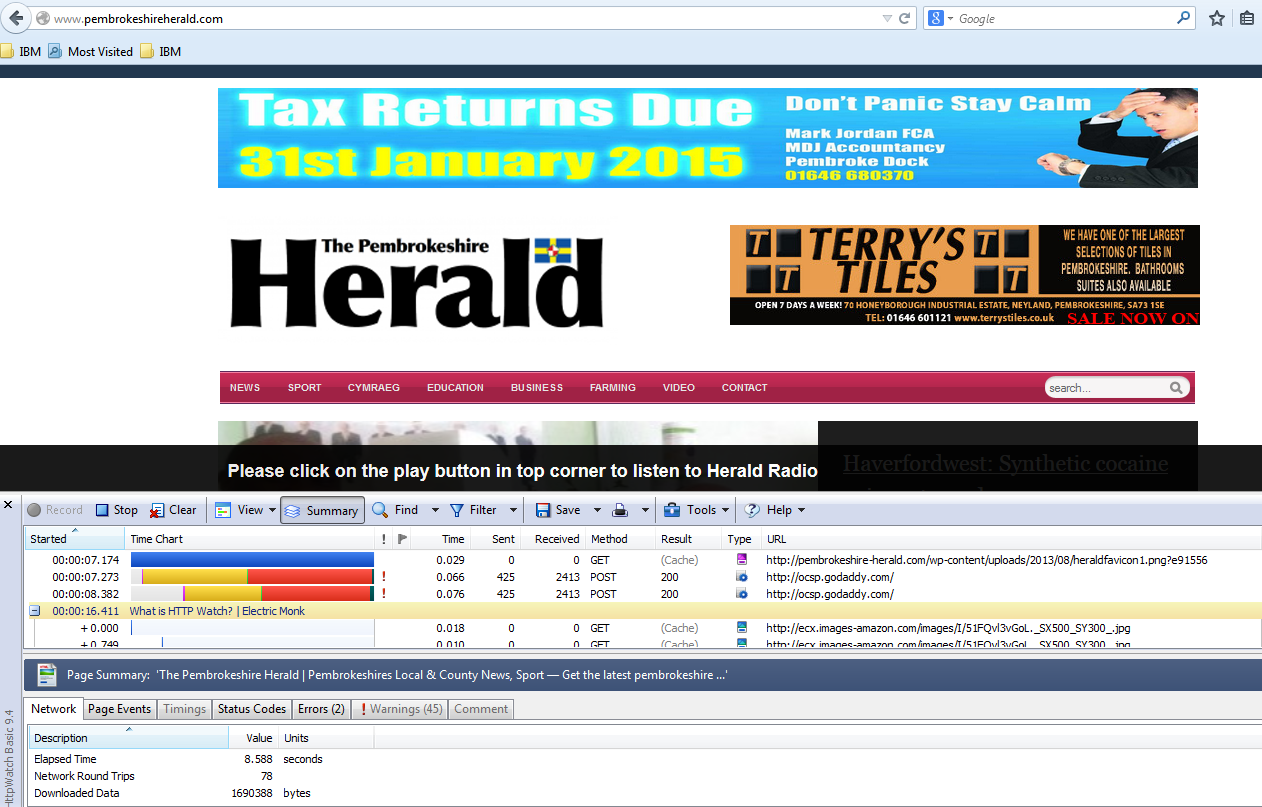
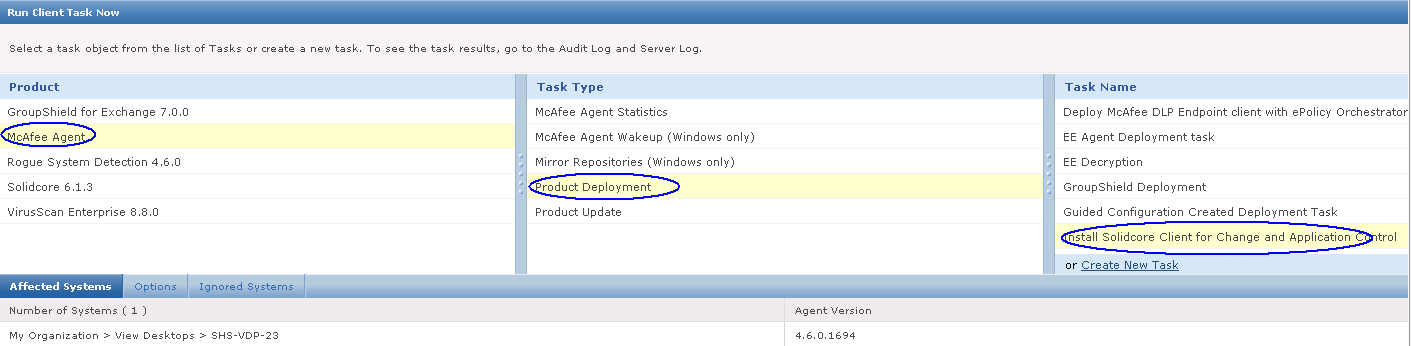
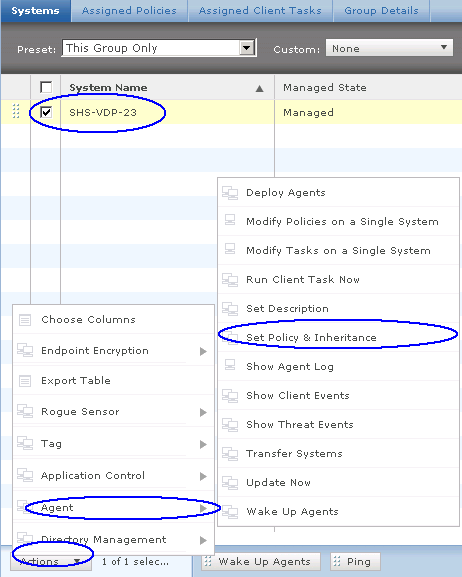
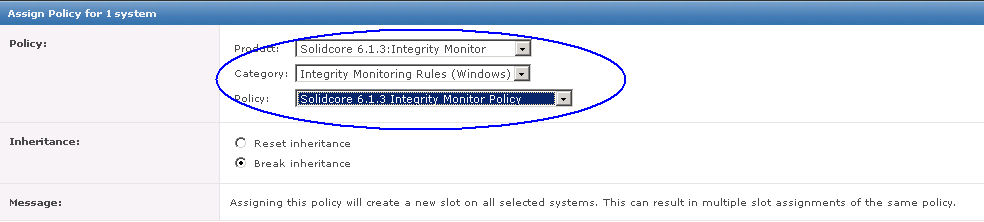
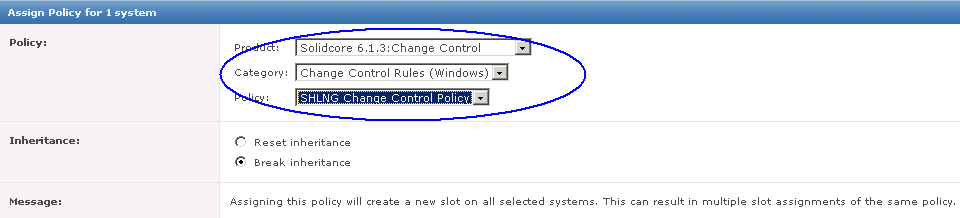
- Once you have HttpWatch displayed in the browser, press the Record button to start recording HTTP requests.
- If you are using the free Basic Edition then extended HTTP information is only displayed for sites in the Alexa Top 20 or httpwatch.com
- As an example I have tested http://pembrokeherald.com
- You can then see all the underlying websites