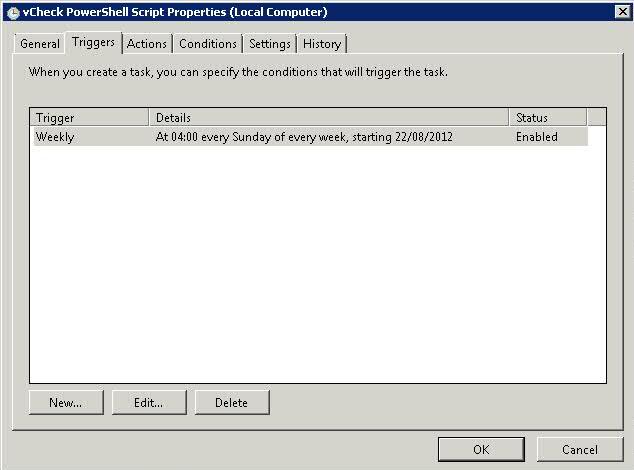
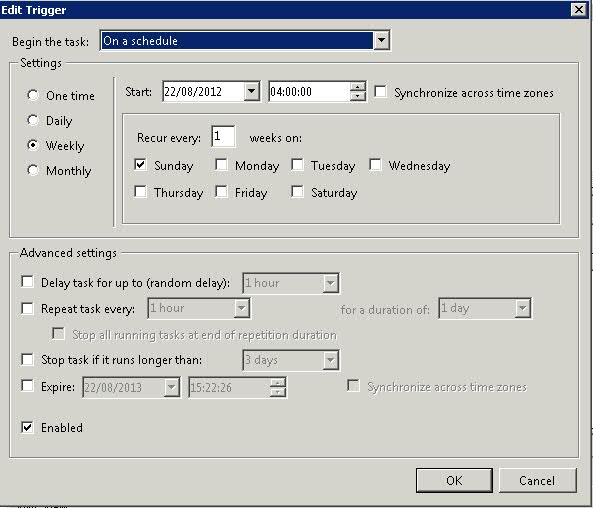
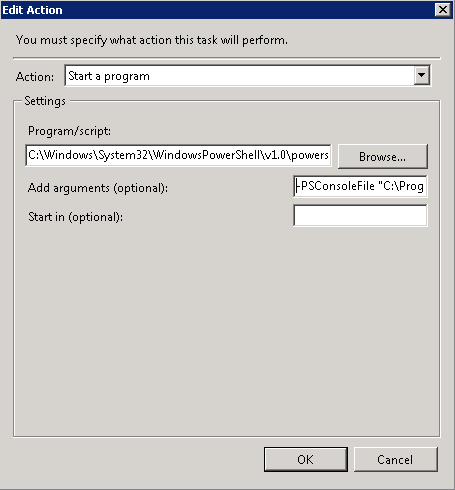
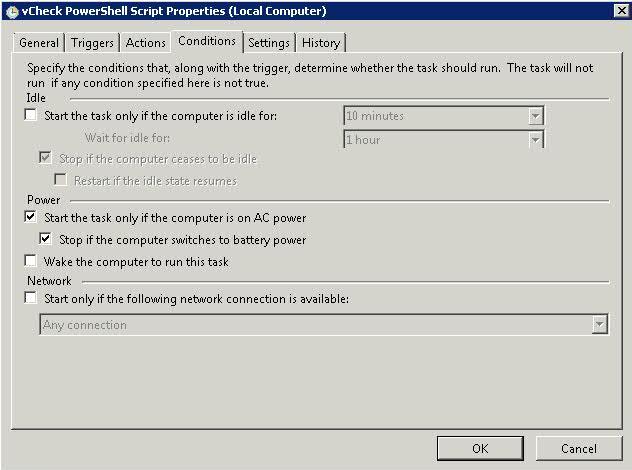
What is the Comprestimator?
Comprestimator is a command line host-based utility that can be used to estimate
expected compression rate for block-devices. The Comprestimator utility uses
advanced mathematical and statistical formulas to perform the sampling and
analysis process in a very short and efficient way. The utility also displays its
accuracy level by showing the maximum error range of the results achieved based
on the formulas it uses. The utility runs on a host that has access to the devices
that will be analyzed, and performs only read operations so it has no effect
whatsoever on the data stored on the device. The following section provides
useful information on installing Comprestimator on a host and using it to analyze
devices on that host. Depending on the environment configuration, in many cases
Comprestimator will be used on more than one host, in order to analyze
additional data types.
It is important to understand block-device behavior when analyzing traditional
(fully-allocated) volumes. Traditional volumes that were created without initially
zeroing the device may contain traces of old data in the block-device level. Such
data will not be accessible or viewable in the file-system level. When using
Comprestimator to analyze such volumes, the expected compression results will
reflect the compression rate that will be achieved for all the data in the blockdevice
level, including the traces of old data. This simulates the volume mirroring
process of the analyzed device into a compressed volume. Later, when volume
mirroring is actually used to compress the data on the storage system, it will
process all data on the device (including both active data and traces of old data)
and get it compressed. After that when storing more active data on the
compressed volume, traces of old data will start getting deleted by new data that
is written into the volume. As more active data accumulates in the device the
compression rate achieved will be adjusted to reflect the accurate savings
achieved for the active data. This block-device behavior is limited to traditional
volumes and will not occur when analyzing thinly provisioned volumes
Regardless of the type of block-device being scanned, it is also important to
understand a few characteristics of common file-systems space management.
When files are deleted from a file-system, the space they occupied before being
deleted will be freed and available to the file-system even though the data on disk
was not actually deleted but rather the file-system index and pointers were
updated to reflect this change. When using Comprestimator to analyze a block-device used by a file-system – all underlying data in the device will be analyzed, regardless of whether this data belongs to files that were already deleted from the file-system. For example – you can fill a 100GB file-system and make it 100% used, then delete all the files in the file-system making it 0% used. When scanning the block-device used for storing the file-system in this example, Comprestimator (or any other utility for that matter) will access the data that belongs to the files that were already deleted.
In order to reduce the impact of block-device and file-system behavior mentioned above it is highly recommended to use Comprestimator to analyze volumes that contain as much active data as possible rather than volumes that are mostly empty of data. This increases accuracy level and reduces the risk of analyzing old data that is already deleted but may still have traces on the device.
Your primary resource for sizing and implementing: Real-time Compression in SAN Volume Controller and Storwize V7000 Redpaper
http://www.redbooks.ibm.com/Redbooks.nsf/RedpieceAbstracts/redp4859.html?Open
Instructions on how to set up IBM Real-time Compression for 45 Day Evaluation Real-time Compression Evaluation User Guide
http://www.ibm.com/support/docview.wss?uid=ssg1S7003988
Compatibility
- Red Hat Enterprise Linux Version 5 (64-bit)
- ESXi 5.0
- AIX V6.1, V7.1
- Windows 2003 Server, Windows 2008 Server (32-bit and 64-bit
Instructions for use with ESX
- Download the installer and you should see the following zip file containing the below folders
- Click on the Host > Configuration > Security Profile > Properties > Select Remote Tech Support > Click Options > Start > This will enable you to connect to the host remotely using Putty and WinSCP
- Copy the installer to the server you want to run WinSCP and Putty on and make sure it is unzipped
- Log into the host using Winscp and copy across the Comprestimator_Linux to the /tmp folder on the host
- Next Putty into the host and login
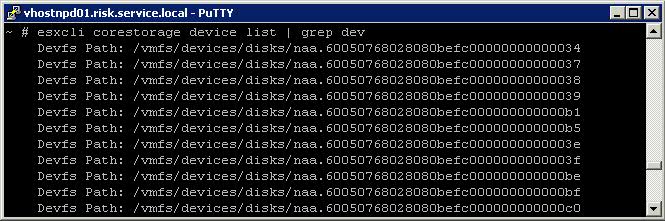
- Run the following command to get the list of devices
- esxcli corestorage device list | grep dev
- Type cd tmp to get to the diretcory you copied the Comprestimator_Linux Tool into
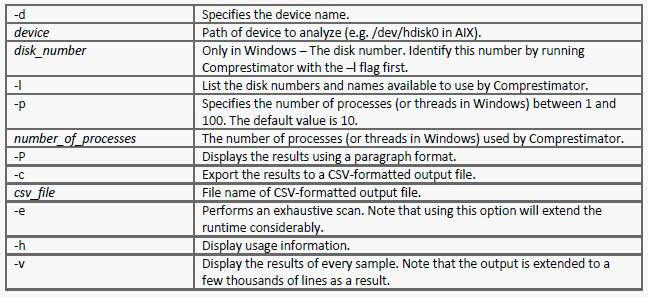
- Type ./comprestimator_linux -d /vmfs/devices/disks/naa.60050768028080befc00000000000034 -p 10 -P -e -h -c outputfile -v
- Type ./comprestimator_linux -d /vmfs/volumes/099b2072-7bd8dac0-7c5c-015dcc8bfc70 -p 10 -P -h -e -c outputfile -v
- Type ./comprestimator_linux -d /vmware/volumes/-p 10 -P -h -e -c outputfle -v
- Run this tool for each device