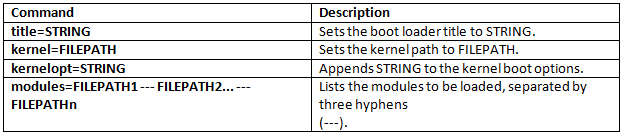
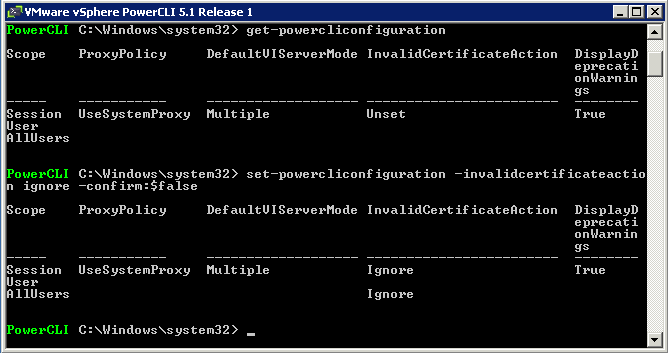
What is ESXi Image Builder CLI?
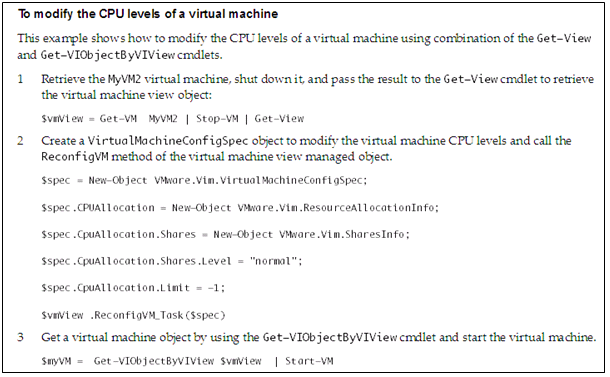
The ESXi Image Builder CLI is a set of PowerCLI cmdlets that you can use to manage vSphere image profiles and VIB packages, such as driver VIBs and update VIBs. You can also use Image Builder cmdlets to export an image profile to an ISO or offline depot ZIP file that you can use to install ESXi with a customized set of updates, patches, and drivers.
- Manage software depots
- Manage image profiles
- Manage Software packages (VIBs).
- Image profiles and VIBs specify the software you want to use during installation or upgrade of an ESXi host.
ESXi Image Builder Requirements
- Microsoft .NET 2.0
- Microsoft PowerShell 1.0 or 2.0
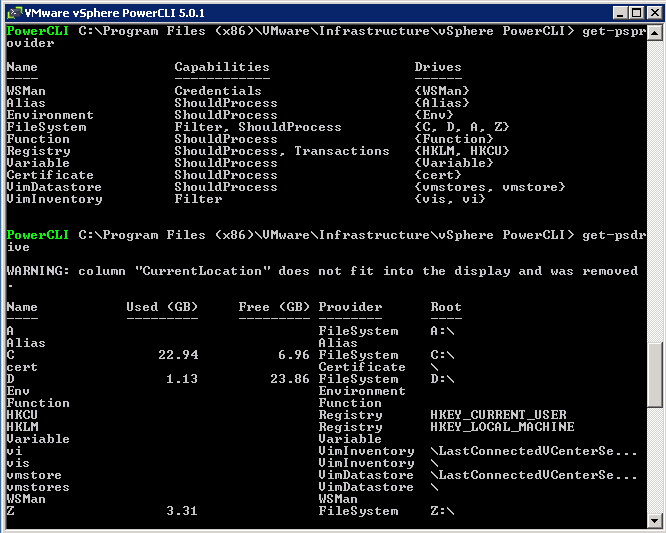
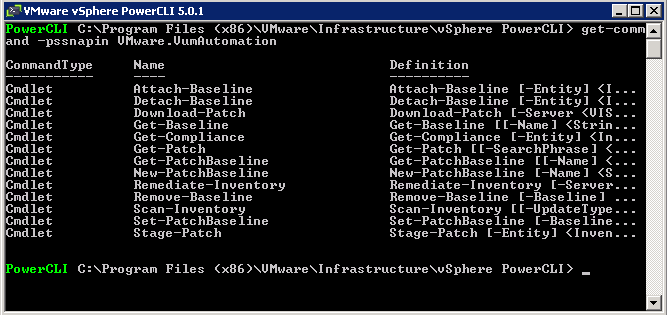
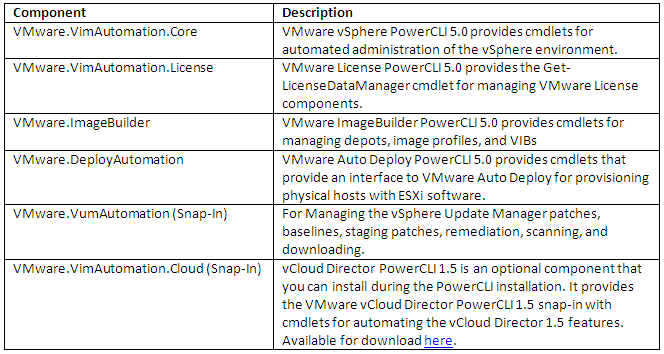
- vSphere PowerCLI (includes Image Builder cmdlets)
- Turn off IE ESC in Server Manager – Allows you to download TFTP Boot Zip file and AutoDeploy Log Files
Image Builder Overview
You use Image Builder cmdlets for managing the software to deploy to your ESXi hosts in several different scenarios.
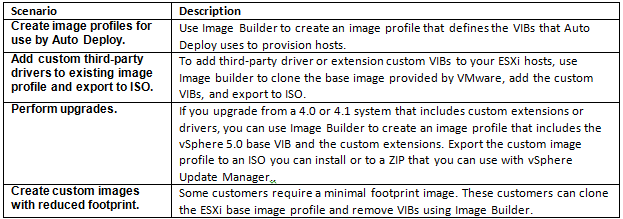
The Image Builder PowerCLI cmdlets take image profiles and VIBs as input and produce different outputs.
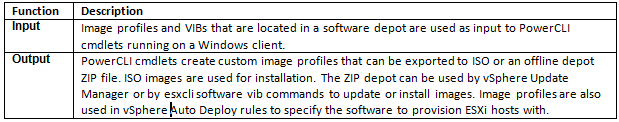
Image Builder Architecture
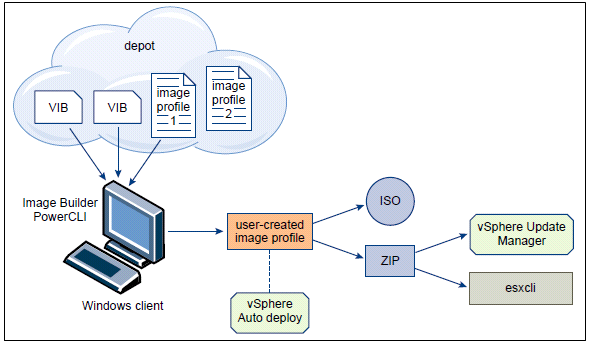
Terms and Definitions

Requirements
You can create a custom image profile from scratch or clone an existing profile and add or remove VIBs. A profile must meet the following requirements to be valid.
- Each image profile must have a unique name and vendor combination.
- Each image profile has an acceptance level. When you add a VIB to an image profile with an Image Builder PowerCLI cmdlet, Image Builder checks that the VIB matches the acceptance level defined for the profile.
- You cannot remove VIBs that are required by other VIBs.
- You cannot include two versions of the same VIB in an image profile. When you add a new version of a VIB, the new version replaces the existing version of the VIB.
Image Profile Validation
An image profile and its VIBs must meet several criteria to be valid.
- Image profiles must contain at least one base VIB and one bootable kernel module
- If any VIB in the image profile depends on another VIB, that other VIB must also be included in the image profile. VIB creators store that information in the SoftwarePackage object’s Depends property.
- VIBs must not conflict with each other. VIB creators store conflict information in the SoftwarePackage object’s Conflicts property.
- Two VIBs with the same name, but two different versions, cannot coexist. When you add a new version of a VIB, the new version replaces the existing version of the VIB.
- No acceptance level validation issues exist.
When you make a change to an image profile, Image Builder checks that the change does not invalidate the profile.
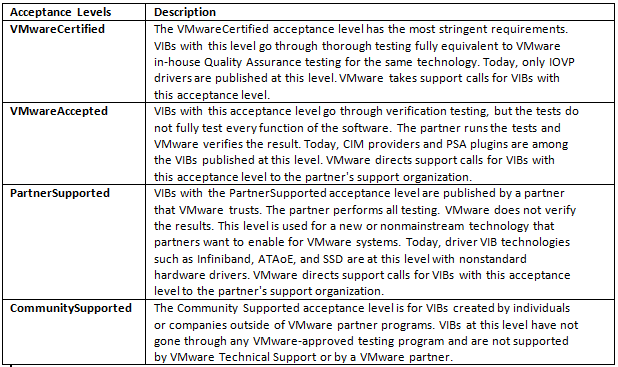
Acceptance Levels
Each VIB is released with an acceptance level that cannot be changed. The host acceptance level determines which VIBs can be installed to a host. You can change the host acceptance levels with esxcli commands.
Create an Image Profile
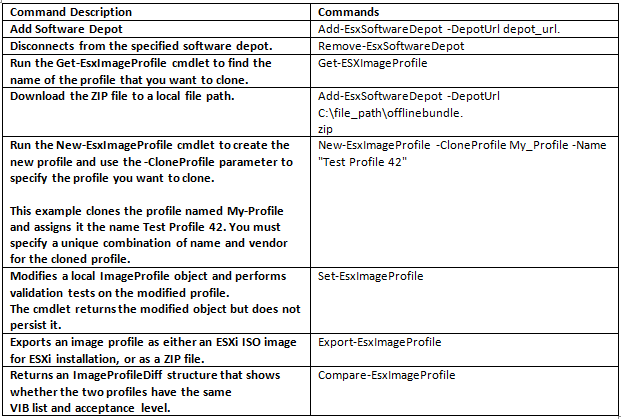
Cloning a published profile is the easiest way to create a custom image profile. Cloning a profile is especially useful if you want to remove a few VIBs from a profile, or if you want to use hosts from different vendors and want to use the same basic profile, but want to add vendor-specific VIBs. VMware partners or large installations might consider creating a profile from scratch.
Add VIBs to an Image Profile
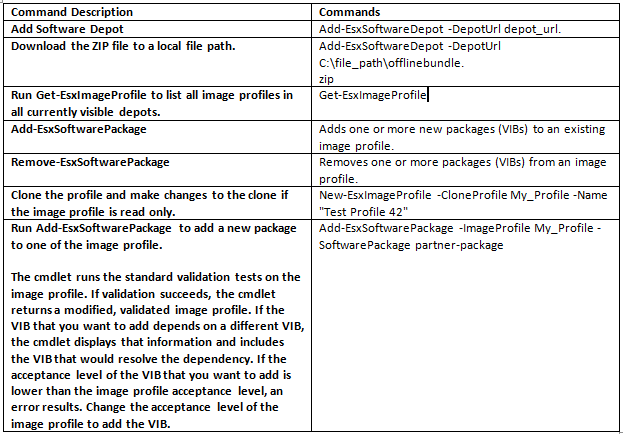
You can add one or more VIBs to an image profile if that image profile is not set to ReadOnly. If the new VIB depends on other VIBs or conflicts with other VIBs in the profile, a message is displayed at the PowerShell prompt and the VIB is not added.
You can add VIBs from VMware or from VMware partners to an image profile. If you add VMware VIBs, the Image Builder PowerCLI performs validation. If you add VIBs from two or more OEM partners, no errors are reported but the resulting image profile might not work. Install VIBs from only one OEM vendor at a time.
Custom drivers can be found in the “Drivers & Tools” section in the vSphere 5.0 “Support and Downloads” pages.
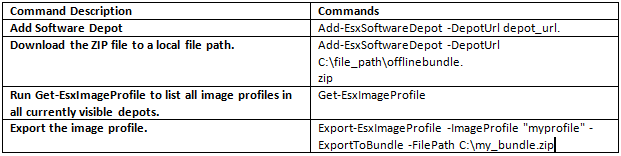
Export an Image Profile to ISO or Offline Bundle ZIP
You can export an image profile to an ISO image or a ZIP file of component files and folders. You cannot create both by running the cmdlet once. You can use the ISO image as an ESXi installer or upload the ISO into vSphere Update Manager for upgrades. You can use the ZIP file, which contains metadata and the VIBs specified in the image profile, for upgrades to ESXi 5.0 and later.
Export an image profile to ISO from the PowerCLI prompt.
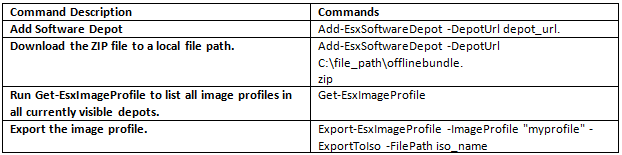
Export an image profile to an offline bundle ZIP from the PowerCLI prompt.
Demo
- Log in to the console of the Windows system on which vCenter Server is installed with administrator privileges, either directly or by using RDP.
- Download the ESXi Depot ZIP file from the VMware Web site to a location the PowerCLI Windows system can access.
- Typically, you will start by downloading the VMware software depot from http://www.vmware.com/downloads. This depot contains the ESXi VIBs provided by VMware. Choose the zip file
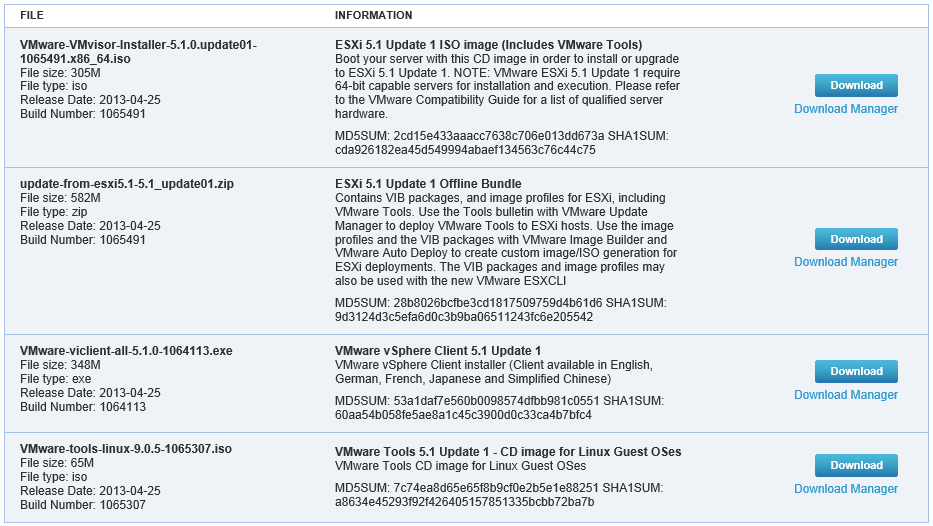
- The file has a name that follows this pattern: VMware-Esxi-5.0.0-xxxxx-depot.zip.
- Save the ZIP file to your local D:\ drive or any volume with enough space and note the location of the file. I am using E:\depot
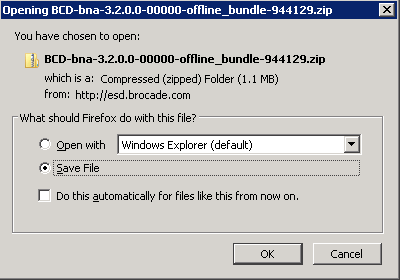
- Download a VIB from a manufacturers website like Brocade and save this into your depot
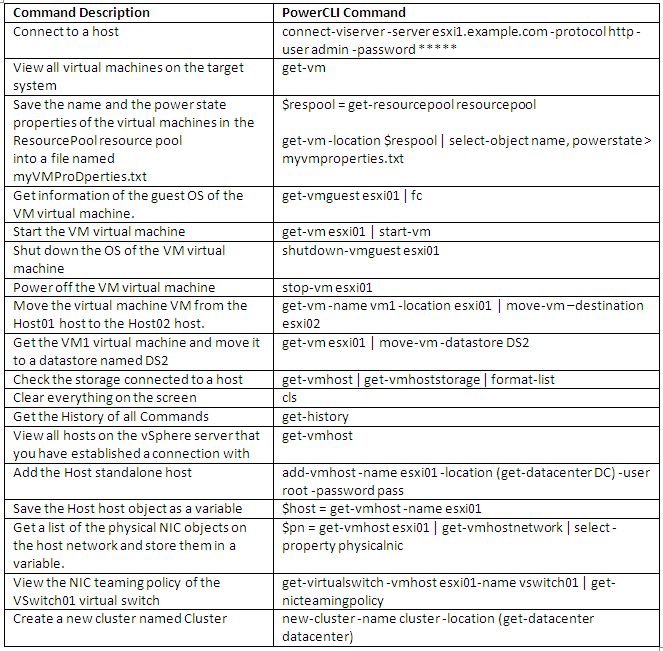
- Start a PowerCLI session and run the following cmdlets at the prompt.
- Connect-VIServer -Server your_vc_hostname -User username -Password password
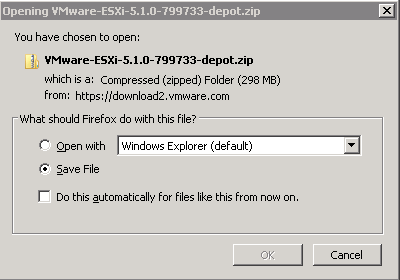
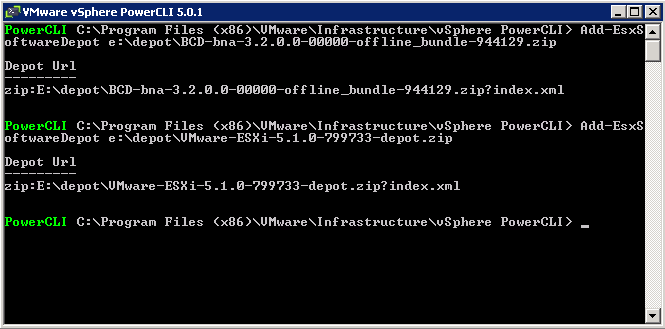
- Add-EsxSoftwareDepot E:\Depot\VMware-ESXi-5.1.0-799733-depot.zip
- Add-EsxSoftwareDepot E:\Depot\BCD-bna-3.2.0.0-00000-offline_bundle-944129.zip
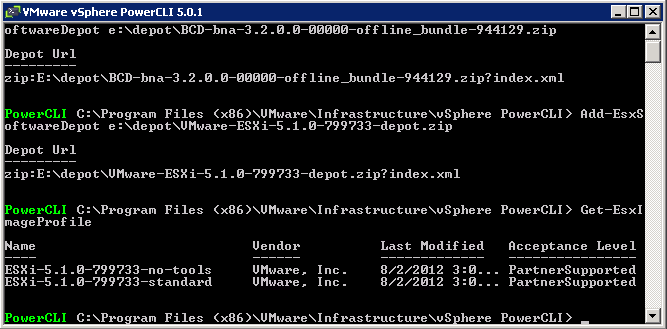
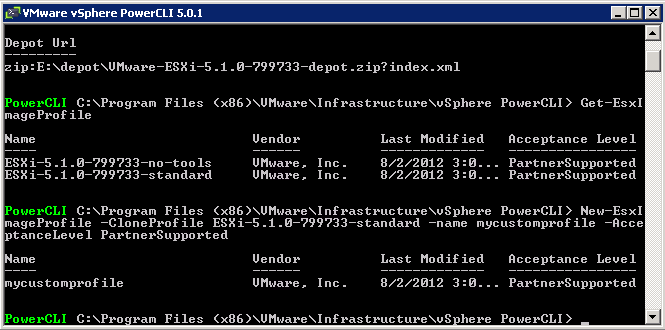
- Clone an existing profile to use as your starting point
- New-EsxImageProfile -CloneProfile ESXi-5.1.0-799733-standard -name mycustomprofile -AcceptanceLevel PartnerSupported
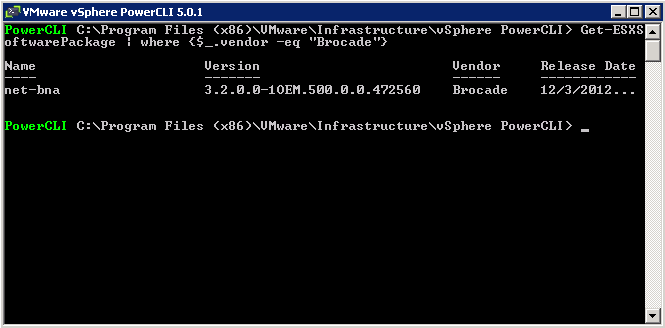
- Next add the Brocade software package to the mycustomprofile
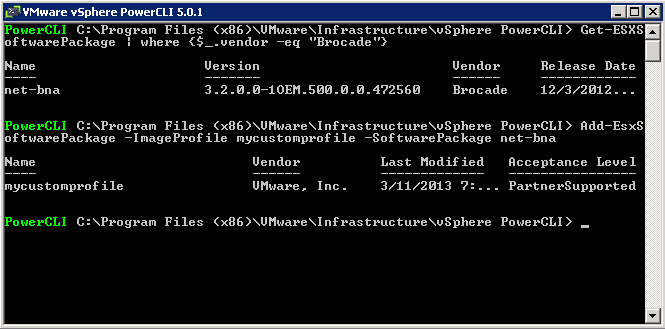
- Type Get-ESXSoftwarePackage | where {$_.vendor -eq Brocade} to see your software
- Then type Add-EsxSoftwarePackage -ImageProfile mycustomprofile -SoftwarePackage net-bna
- Note you can also remove software by typing remove-esxsoftwarepackage -imageprofile mycustomprofile -softwarepackage net-bna
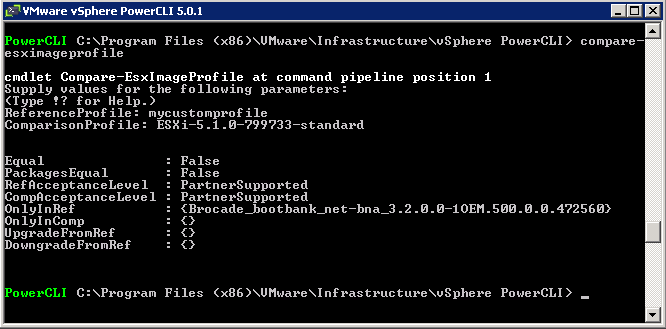
- If you want you can compare the original profile with your custom profile to check the Software Package has been added
- compare-esximageprofile and then input the Reference profile (ESXi-5.1.0-799733-standard) with the Comparison profile (mycustomprofile)
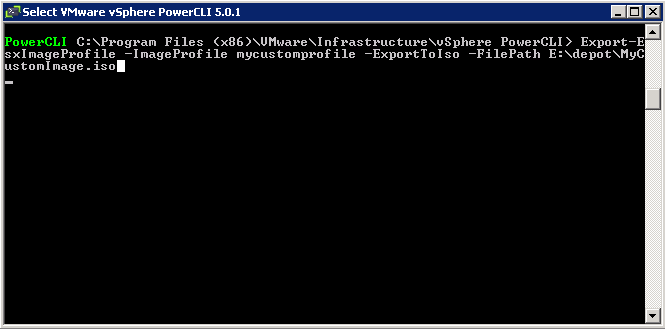
- After adding the VIBs, you need to save/export the Image Profile which you can do to a zip file or an ISO file
See below 2 commands (ZIP and ISO)
- For ISO, type Export-EsxImageProfile -ImageProfile mycustomprofile -ExportToIso -FilePath E:\depot\MyCustomImage.iso
- For ZIP, type Export-EsxImageProfile -ImageProfile mycustomprofile -ExportToIso -FilePath E:\depot\MyCustomImage.zip
- Check the depot for your new custom iso

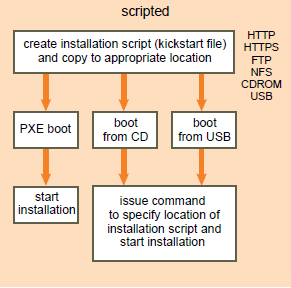
Given a Scenario, Determine when to Customize a Configuration
- If you are deploying a single or a few hosts, you will tend to go for an interactive install.
- When deploying a larger number of hosts, it is a good idea to choose a scripted installation or use Auto Deploy
- Auto Deploy is under the highest licensing package VMware offer so the functionality depends on what licensing you have
- Staff will require skills in command line configuration
- Time taken to write scripts and test custom builds may be not feasible in some IT Departments