ESXi Security
By introducing a layer of abstraction between the physical hardware and virtualized systems running IT services, virtualization technology provides a powerful means to deliver cost savings via server consolidation as well as increased operational efficiency and flexibility. However, the added functionality introduces a virtualization layer that itself becomes a potential avenue of attack for the virtual services being hosted. Because a single host system can house multiple virtual machines, the security of that host becomes even more important. Because it is based on a light‐weight kernel optimized for virtualization, VMware ESX and VMware ESXi are less susceptible to viruses and other problems that affect general‐purpose operating systems. However, ESX/ESXi is not impervious to attack, and you should take proper measures to harden it, as well as the VMware VirtualCenter management server, against malicious activity or unintended damage
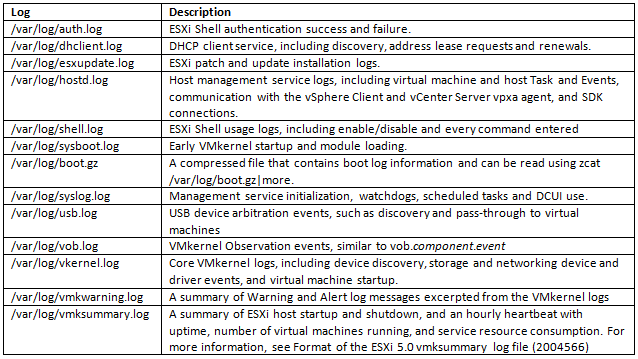
The log files provide an important tool for diagnosing breaches of security as well as other system issues. They also provide audit information. In addition to storing information in files on the local host, you can also send this information to a remote syslog server
As with ESX, ESXi maintains its configuration state in a set of configuration files. However, on ESXi these files can be accessed only using the remote file access API, and there are far fewer files involved. These files normally are not modified directly. Instead, their contents normally change indirectly because of some action invoked on the host. However, the file access API does allow for direct modification of these files, and some modifications might be warranted in special circumstances. Therefore, you should monitor all of these files for integrity and unauthorized tampering, either by periodically downloading them and tracking their contents or by using a commercial tool designed to do this.



Leave a Reply