What is a Network Protocol?
A network protocol defines rules and conventions for communication between network devices. Protocols for computer networking all generally use packet switching techniques to send and receive messages in the form of packets.
Network protocols include mechanisms for devices to identify and make connections with each other, as well as formatting rules that specify how data is packaged into messages sent and received. Some protocols also support message acknowledgement and data compression designed for reliable and/or high-performance network communication. Hundreds of different computer network protocols have been developed each designed for specific purposes and environments.
In modern protocol design, protocols are “layered” according to the OSI 7 layer model or a similar layered model. Layering is a design principle which divides the protocol design into a number of smaller parts, each part accomplishing a particular sub-task and interacting with the other parts of the protocol only in a small number of well-defined ways. Layering allows the parts of a protocol to be designed and tested while keeping each design relatively simple. Layering also permits familiar protocols to be adapted to unusual circumstances
Common Network protocols
- Fibre Channel network protocols
- Internet Protocol Suite or TCP/IP model or TCP/IP stack (TCP/UDP)
- OSI protocols family of information exchange standards developed jointly by the ISO and the ITU-T
- Routing protocols EIGRP, OSPF and BGP
- List of IP protocol numbers, protocol numbers used in the Protocol field of the IPv4 header and the Next Header field of IPv6 header
- RTPS protocol, an interoperability protocol
- SSH Secure Shell
- FTP File Transfer Protocol
- SMTP Simple Mail Transfer Protocol
- Telnet Telephone Network
- HTTP Hyper Text Transfer Protocol
- HTTPS Secure Hyper Text Transfer Protocol
- SFTP Secure File Transfer Protocol
- SSL Secure Socket Layer
- TLS Transport Layer Security
- POP post office protocol
- ARP Address Resolution Protocol
- ICMP Internet Control Mangement Protocol
- H.323 Real-time transfer of audio and video data over packet networks
- SNMP Monitor network availability and performance
- SOCKS Allow clients to communicate with proxy servers (or VPN servers) through network firewalls.
- NTP Network Time Protocol
- CDP Cisco Discovry Protocol
- LLDP Link Layer Discovery Protocol
- NNTP Network News Transfer Protocol
- Telnet
- SSH Secure Shell
- DNS
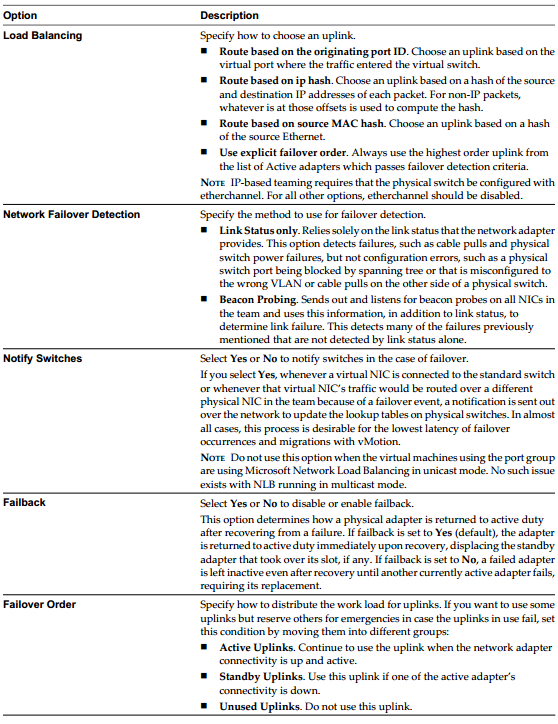
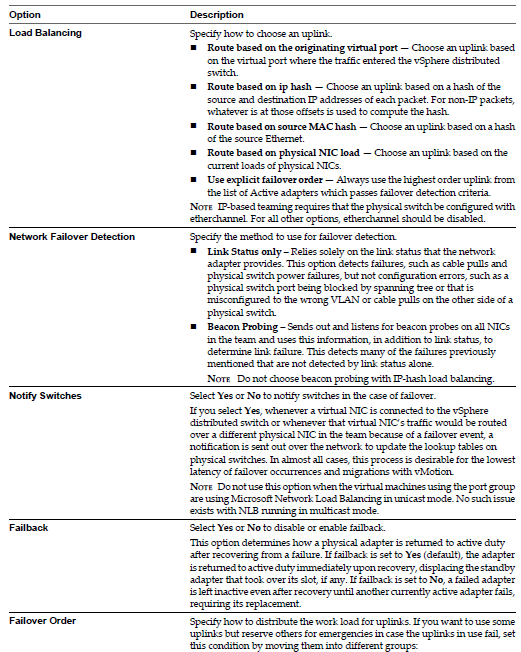
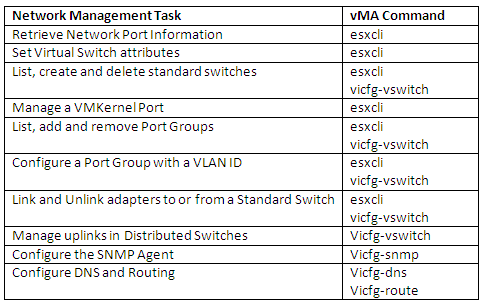
NIC Teaming Protocols used in vSphere
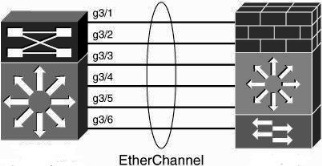
Etherchannel
EtherChannel technologies create a single logical link by bundling multiple physical Ethernet-based links (such as Gigabit Ethernet or Ten Gigabit Ethernet links) together. As such, EtherChannel links can provide for increased redundancy, capacity, and load-balancing. To optimize the load balancing of traffic over multiple links, it is recommended to deploy EtherChannels in powers of two (two, four, or eight) physical links. EtherChannel links can operate at either L2 or L3
EtherChannel links can be created using Cisco Port Aggregation Protocol (PAgP), which performs a negotiation prior to forming a channel, to ensure compatibility and administrative policies. You can configure PAgP in four channeling modes:
- On: Forces the LAN port to channel unconditionally. In the on mode, a usable EtherChannel exists only when a LAN port group in the on mode is connected to another LAN port group in the on mode. Ports configured in the on mode do not negotiate to form EtherChannels: They just do or do not, depending on the other port’s configuration.
- Off: Precludes the LAN port from channeling unconditionally.
- Desirable: Places a LAN port into an active negotiating state in which the port initiates negotiations with other LAN ports to form an EtherChannel by sending PAgP packets. A port in this mode forms an EtherChannel with a peer port that is in either auto or desirable PAgP mode.
- Auto: (Default) Places a LAN port into a passive negotiating state in which the port responds to PAgP packets it receives but does not initiate PAgP negotiation. A port in this mode forms an EtherChannel with a peer port that is in desirable PAgP mode (only)
LACP
Alternatively, EtherChannels can be negotiated with the IEEE 802.3ad Link Aggregation Control Protocol (LACP), which similarly allows a switch to negotiate an automatic bundle by sending LACP packets to the peer. LACP supports two channel negotiation modes:
- Active: Places a port into an active negotiating state in which the port initiates negotiations with other ports by sending LACP packets. A port in this mode forms a bundle with a peer port that is in either active or passive LACP mode.
- Passive: (Default) Places a port into a passive negotiating state in which the port responds to LACP packets it receives but does not initiate LACP negotiation. A port in this mode forms a bundle with a peer port that is in active LACP mode (only).
Similar to PAgP, LACP requires only a single command on the physical interface when configured as a L2 link. Optionally, you can change the LACP mode from the default “passive” negotiation mode
Note that PAgP and LACP do not interoperate with each other; ports configured to use PAgP cannot form EtherChannels with ports configured to use LACP, and can ports configured to use LACP cannot form EtherChannels with ports configured to use PAgP. EtherChannel plays a critical role in provisioning network link redundancy, especially at the campus distribution and core layers. Furthermore, an evolution of EtherChannel technology plays a key role the Cisco Virtual Switching System