Introduction
One of the nice features introduced in Windows Server 2008R2 AD DS is the ability to configure fine grained password policies through GUI.. You can use fine-grained password policies to apply different restrictions for password and account lockout policies to different sets of users in a domain
Fine-grained password policies apply only to user objects (or inetOrgPerson objects if they are used instead of User objects) and Global Security Groups. They cannot be applied to Computer objects.
Instructions
- Log into your DC and type Start > Run > gpmc.msc or Start > Administrative Tools > Group Policy Management
- Expand Forest: yourforest.com.
- Expand Domains: yourdomain.com.
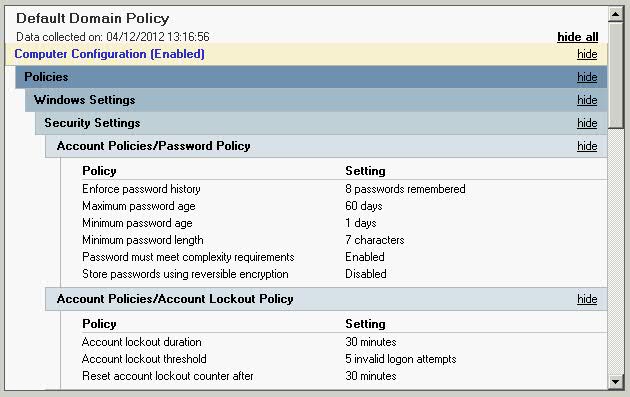
- Click Default Domain Policy and Click Settings in the right hand pane
- Check the current Password Policy
- When you have finished noting the settings you currently have you can minimise the Group Policy Console
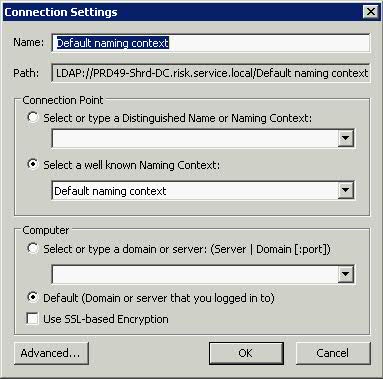
- Next type Start > Run > adsiedit.msc
- Right-click on ADSIEdit > connect to:
- Click OK
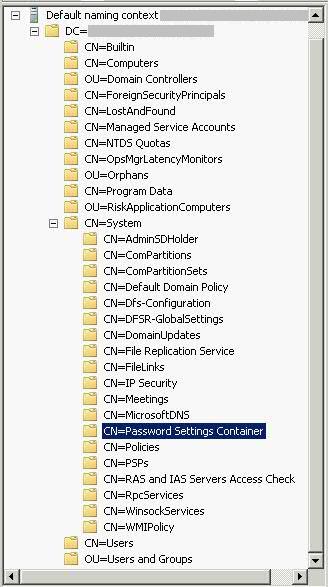
- Expand to Default Naming content > DC=yourdomain,DC=com\CN=System\CN=Password Settings Container\
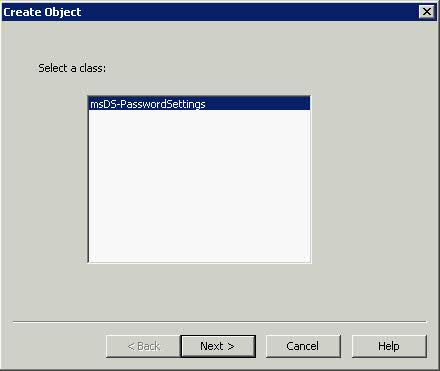
- Right-Click Password Settings Container and click New > Object.
- Select msDS-PasswordSettings > Next
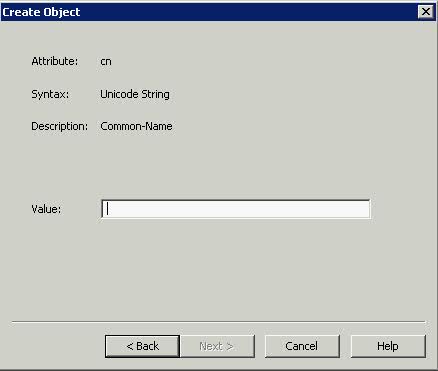
- Type a Value such as NewPasswordPolicy > Next
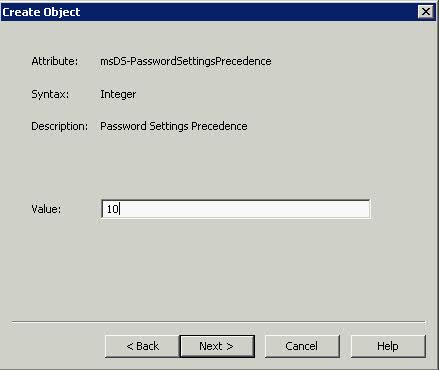
- This box msDS-PasswordsSettingsPrecedence as you can see above is an integer value that is used to resolve conflicts if multiple PSOs are applied to a user or group object. If you have multiple PSOs, the PSO with the lowest priority takes precedence. Try typing 10 > Next
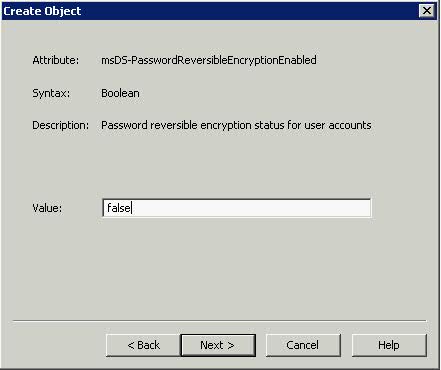
- Type False for the box above msDS-PasswordReversibleEncryptionEnabled > Next
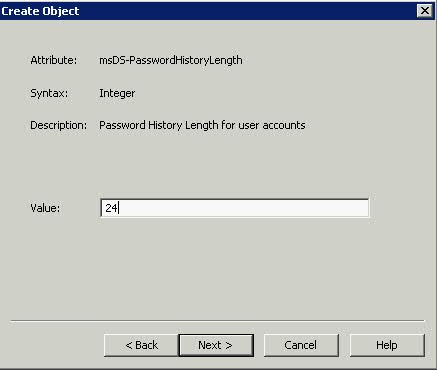
- Type 24 for msDS-PasswordHistoryLength to stop people keeping the same password for 2 years (24 months) > Next
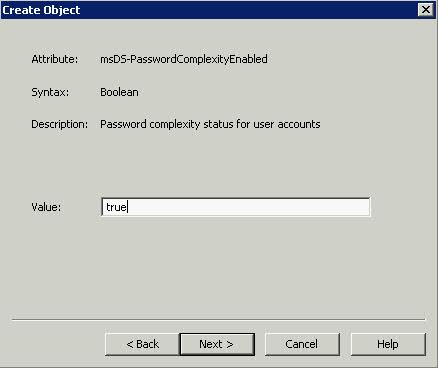
- Type True for msDS-PasswordComplexityEnabled to allow complexity of Caps, Lower Case, Numbers and Special Characters > Next
- Type 8 for msDS-MinimumPasswordLength for the minimum characters a password can be > Next
- Now we get into the next section of configuration where different rules apply.
- When you use ADSI Edit to create the following Password Settings objects (PSOs), enter the values of the four time-related PSO attributes (msDS-MaximumPasswordAge, msDS-MinimumPasswordAge, msDS-LockoutObservationWindow, and msDS-LockoutDuration) in d:hh:mm:ss format.
- Please see this link for detailed settings
- http://technet.microsoft.com/en-us/library/cc754461.aspx
- Type 1:00:00:00 for msDS-MinimumPasswordAge for a 1 day age of password before a user can change it > Next
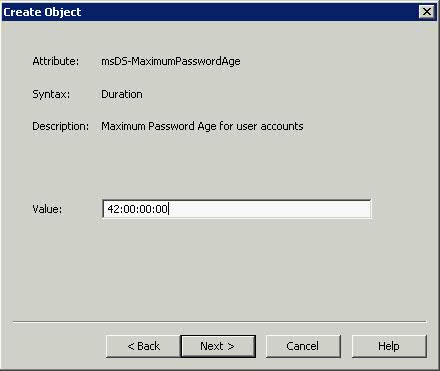
- Type 42 for msDS-MaximumPasswordAge. This will set 42 days before a user is prompted to change their Password > Next
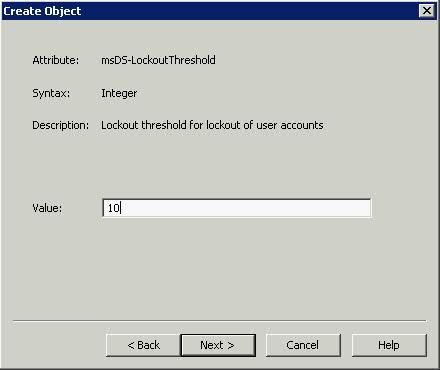
- Type 10 for the amount of Password Attempts that are made before the account is locked out > Next
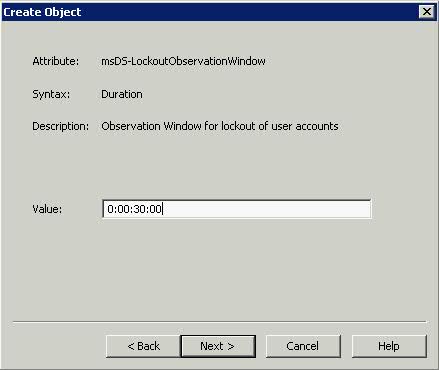
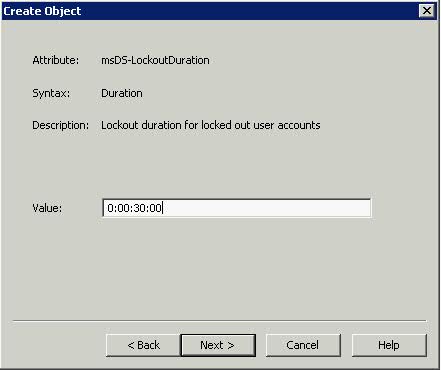
- Type 30 for msDS-LockoutObservationWindow. This setting specifies how long the system should collect bad password attempts to compare to the msDS-LockoutThreshold value. The Lockout Observation window must be smaller than or equal to the lockout duration for a password policy
- Type 0:00:30:00 for msDS-LockoutDuration to set a 30 minute account lockout duration. The lockout duration must be greater than or equal to the lockout observation time for a password policy > Next
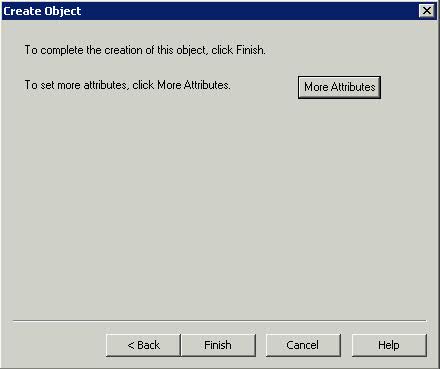
- You can either click Finish or Click on More Attributes
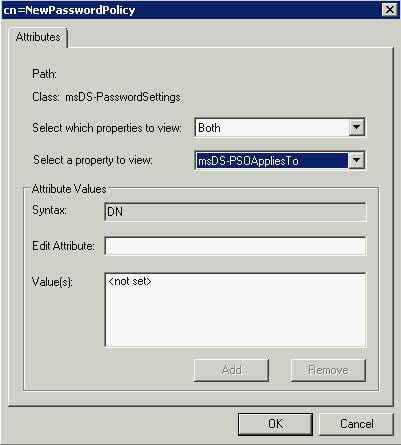
- Select Both for Select which Properties to View
- Click the Drop down on Select a Property to View and choose msDS-PSOAppliesTo
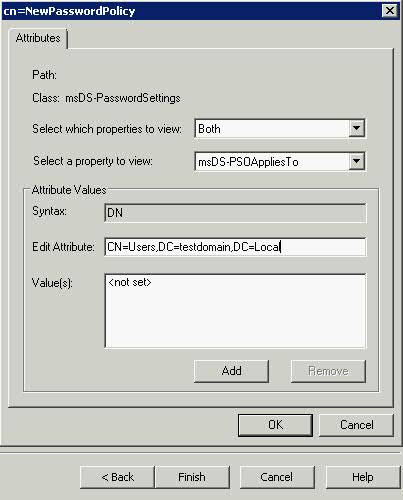
- Click Edit Attribute
- In Edit Attribute, add the distinguished names of users or global security groups that the PSO is to be applied to, and then click Add. E.g CN=Users,DC=testdomain,DC=Local
- You are all Complete with a separate Password Policy applied to a subset of your Active Directory
Link to Step by Step Guide