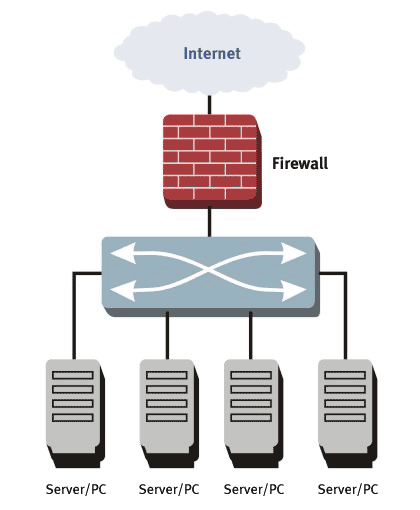
A firewall is a software or hardware device that filters the information coming through the internet. Only information that allowed by the firewall policy can go through.
There are several firewall filtering criteria:
- IP address — a firewall can block all traffic to or from a certain IP address.
- Domain names — a firewall can block all access to certain domain names, or allow access only to specific domain names.
- Protocols — a firewall may set up a few hosts to handle a specific protocol and ban that protocol on other hosts.
- Ports — a firewall can block the access of certain ports on all the hosts inside the LAN.
- Keywords — a firewall can search through each packet for an exact match of the keywords listed in the filter.
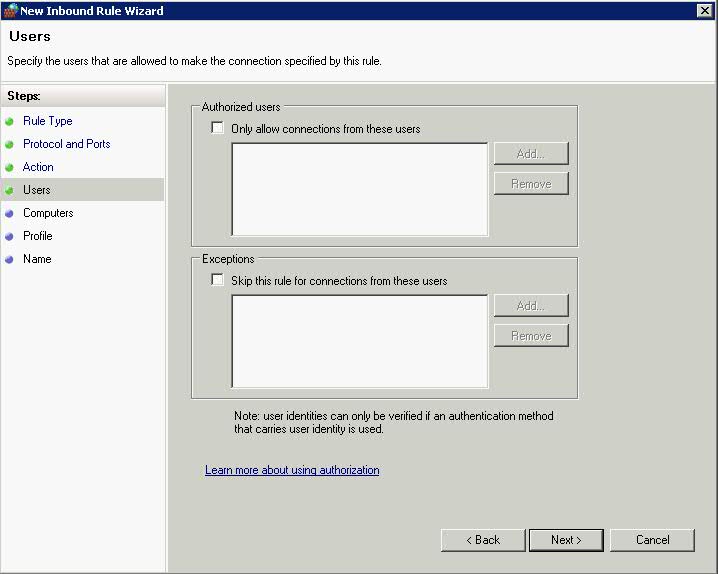
- User Accounts
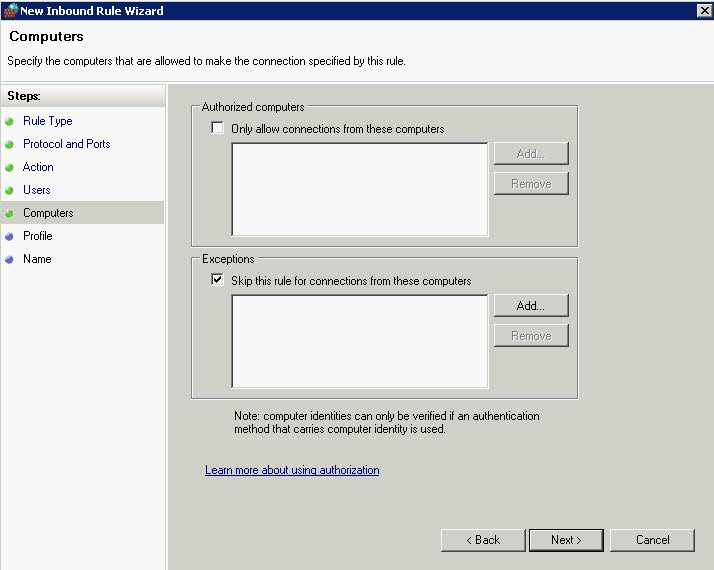
- Computer Accounts
The level of security you set for the firewall will determine how many security threats can be stopped by the firewall. Although higher level of security is more safe, it also limits your internet connectivity — more information, useful or not, will be blocked
WFAS
Windows Firewall with Advanced Security will enable you to configure rules which are applied on which network location awareness profile is active (Domain/Public or Private) and whether the connection is a secure network interface as well as the criteria above
Configuring Inbound Rules
Inbound rules allow a specific type of traffic specified by the rule. When a firewall intercepts an incoming packet, it evaluates the packet against the list of inbound rules. If the packet matches any of the inbound rules, it is processed according to those rules. If it matches no inbound rules then the packet is dropped. Windows Server 2008 when enabled for the IIS Role, automatically configures itself for inbound HTTP traffic on Port 80 and incoming HTTPS Traffic on Port 442
Inbound Rules
- Start > All Programs > Administrative Tools > WFAS
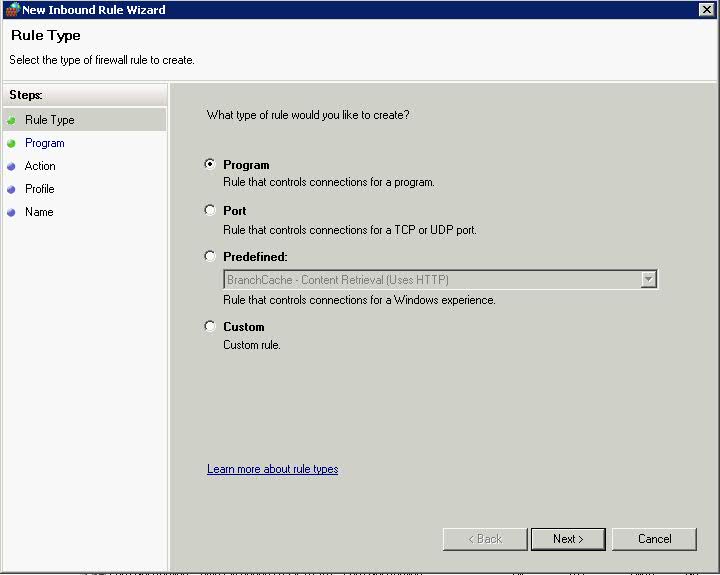
- The first Page of the Inbound Rules allows you to select which type of rule you create
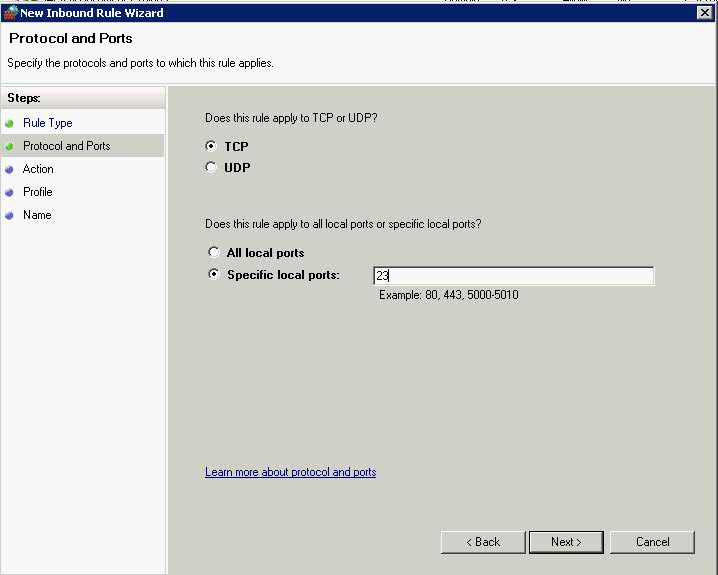
- Click Port > Next > Protocols and Ports
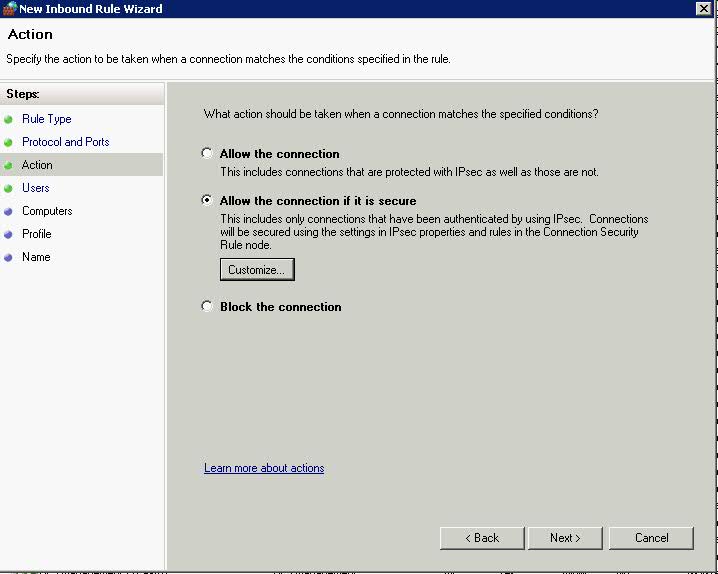
- Choose 23 as the Telnet Port > Next > Choose Allow the connection if it is secure. This adds an extra page where you can specify users and computers using AD to the wizard
- You can click Customise at this point to see this screen
- Click Ok and you are back to the original screen > Click Next > Choose Users to authenticate
- Click Next and Choose which computers to authenticate
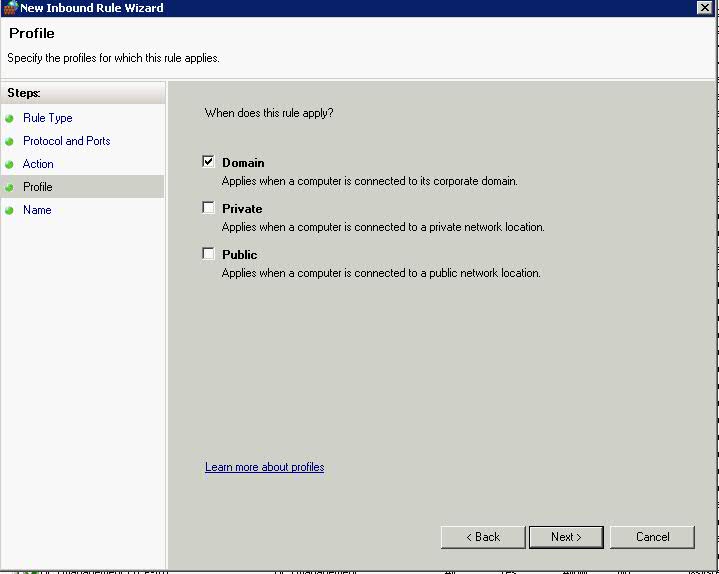
- Click Next > Choose a Profile – Domain for this Rule
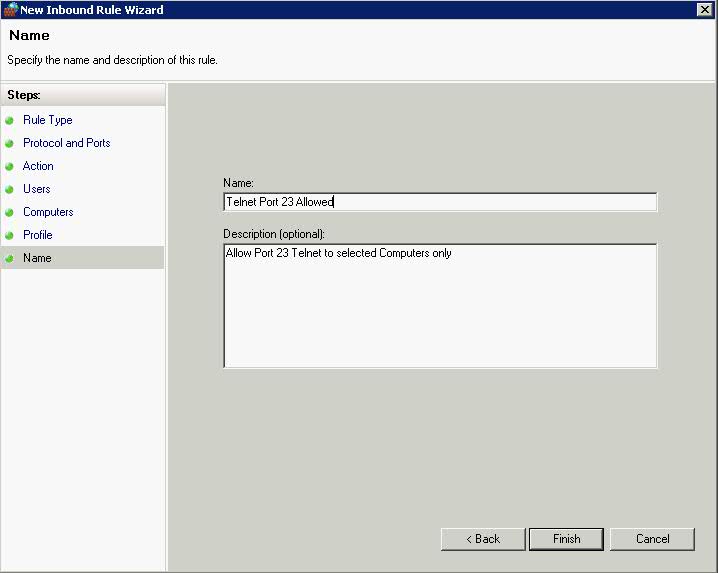
- Click Next and give the Rule a name and a coherent description
Profiles
Computers that are running Windows Vista, Windows Server 2008, Windows 7, and Windows Server 2008 R2 detect the following network location types:
- Public. By default, the public network location type is assigned to any new networks when they are first connected. A public network is considered to be shared with the world, with no protection between the local computer and any other computer. Therefore, the firewall rules associated with the public profile are the most restrictive.
- Private. The private network location type can be manually selected by a local administrator for a connection to a network that is not directly accessible by the public. This connection can be to a home or office network that is isolated from publicly accessible networks by using a firewall device or a device that performs network address translation (NAT). Wireless networks assigned the private network location type should be protected by using an encryption protocol such as Wi-Fi Protected Access (WPA) or WPAv2. A network is never automatically assigned the private network location type; it must be assigned by the administrator. Windows remembers the network, and the next time that you connect to it, Windows automatically assigns the network the private network location type again. Because of the higher level of protection and isolation from the Internet, private profile firewall rules typically allow more network activity than the public profile rule set.
- Domain. The domain network location type is detected when the local computer is a member of an Active Directory domain, and the local computer can authenticate to a domain controller for that domain through one of its network connections. An administrator cannot manually assign this network location type. Because of the higher level of security and isolation from the Internet, domain profile firewall rules typically permit more network activity than either the private or public profile rule sets. On a computer that is running Windows 7 or Windows Server 2008 R2, if a domain controller is detected on any network adapter, then the Domain network location type is assigned to that network adapter. On computers that are running Windows Vista or Windows Server 2008, then the Domain network location type is applied only when a domain controller can be detected on the networks attached to every network adapter.