For this post, I built 2 Test Virtual Machines called DACVNLB001 and DACVNLB002 to test setting up Network Load Balancing. These VMs are running Windows Server 2008 R2
- Once your VMs are built, go into Server Manager or Initial Configuration Tasks and Click Add Features
- Select Network Load Balancing > Next > Install (On Both Servers)
- Reboot
- Open Network Load Balancing Manager on the first server
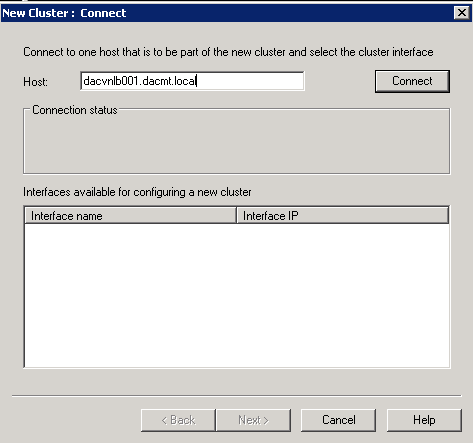
- Right click Network Load Balancing Clusters and choose New Cluster. Put in the first server name
- Click Connect
- Click Next
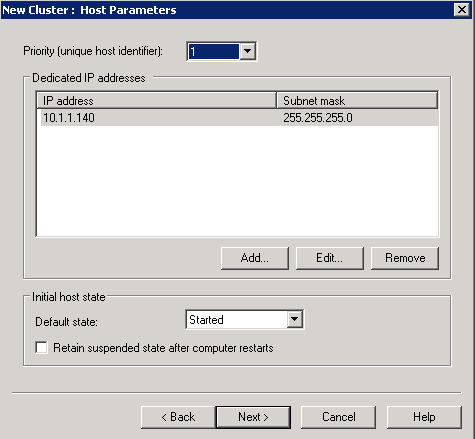
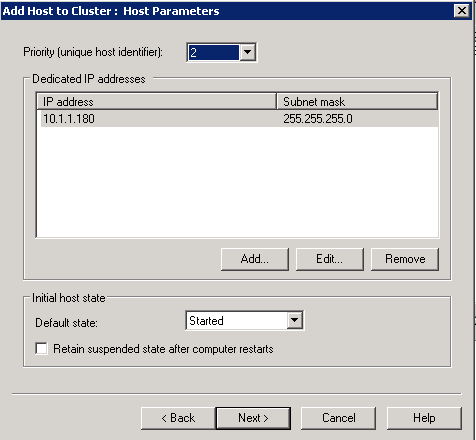
- Priority is set to 1 because this is a new cluster and this is the first host in the cluster
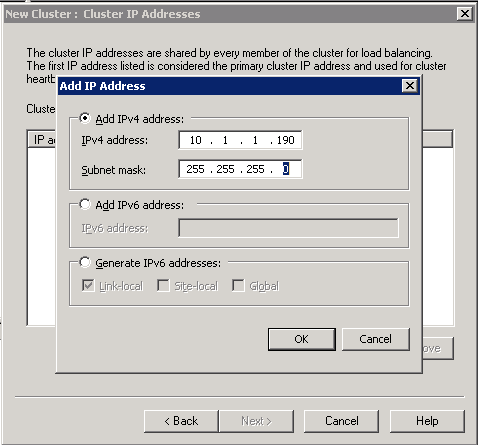
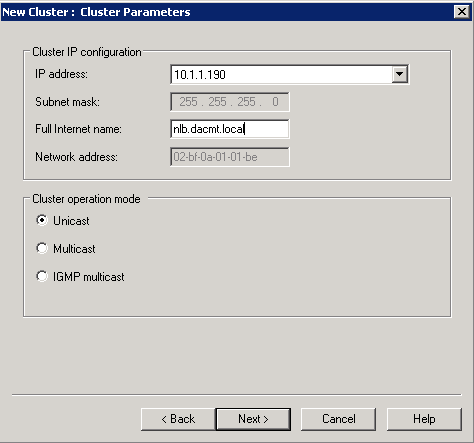
- Click Next. We are now on the Cluster IP Address Page. This must be a unique IP Address in the same network as the 2 NLB Nodes
- Click OK and Next
- Put a full internet name in and choose cluster operation node as Unicast (More described later on this
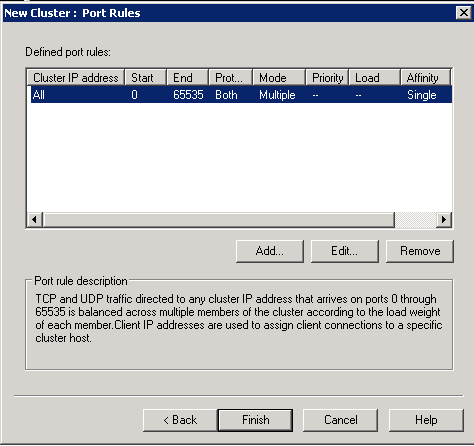
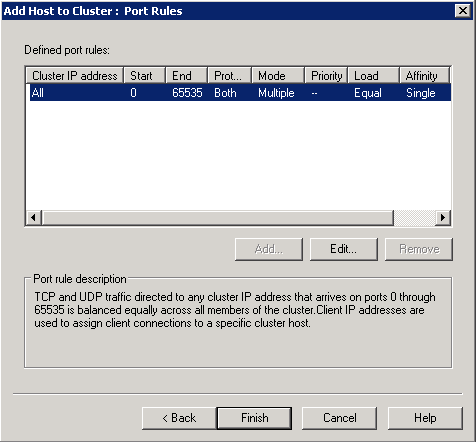
- Click Finish on Port Rules
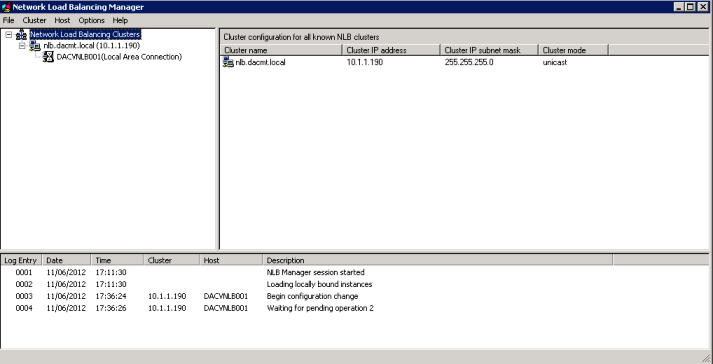
- You should now see the below screen
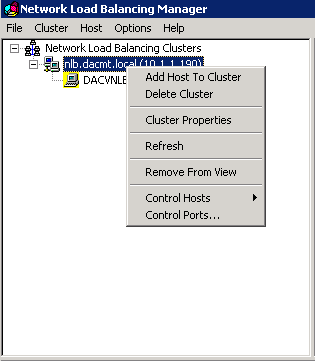
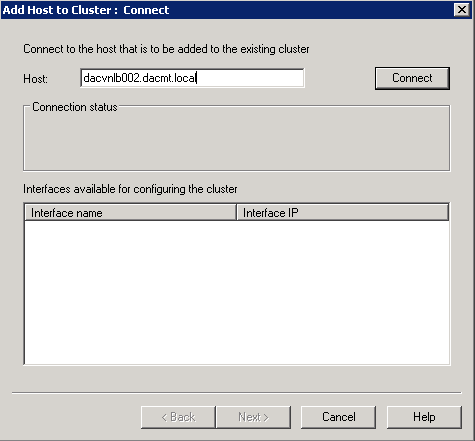
- Now we need to add the other host so right click your cluster name/IP Address in this case 10.1.1.190 and select Add Host to Cluster
- Type in the 2nd node name
- Click Connect
- Check the screen below is correct and click Next
- Click Next on the Ports screen
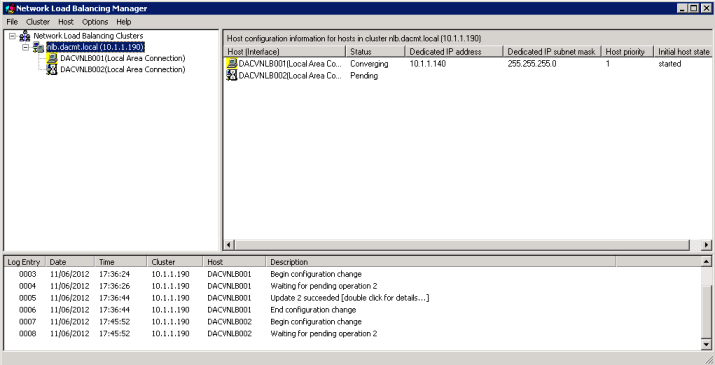
- Wait for them to converge
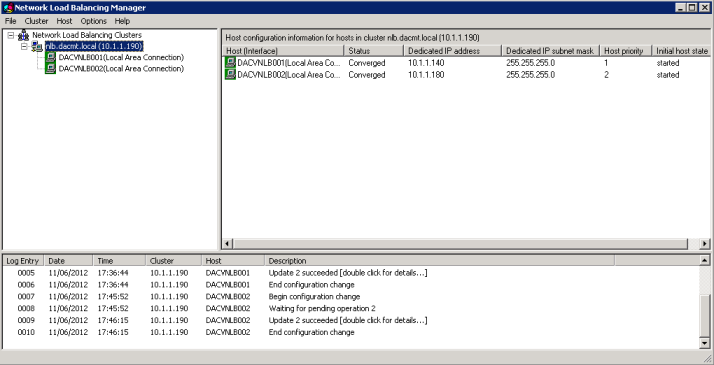
- You are Complete and should look like the below
Unicast and Multicast
Applies To: Windows Server 2003, Windows Server 2003 R2, Windows Server 2003 with SP1, Windows Server 2003 with SP2
All cluster hosts in a cluster receive all incoming client requests that are destined for the virtual IP address that is assigned to the cluster. The Network Load Balancing load-balancing algorithm, which runs on each cluster host, is responsible for determining which cluster host processes and responds to the client request.
You can distribute incoming client requests to cluster hosts by using unicast or multicast methods. Both methods send the incoming client requests to all hosts by sending the request to the cluster’s MAC address.
When you use the unicast method, all cluster hosts share an identical unicast MAC address. Network Load Balancing overwrites the original MAC address of the cluster adapter with the unicast MAC address that is assigned to all the cluster hosts.
When you use the multicast method, each cluster host retains the original MAC address of the adapter. In addition to the original MAC address of the adapter, the adapter is assigned a multicast MAC address, which is shared by all cluster hosts. The incoming client requests are sent to all cluster hosts by using the multicast MAC address.
Select the unicast method for distributing client requests, unless only one network adapter is installed in each cluster host and the cluster hosts must communicate with each other. Because Network Load Balancing modifies the MAC address of all cluster hosts to be identical, cluster hosts cannot communicate directly with one another when using unicast. When peer-to-peer communication is required between cluster hosts, include an additional network adapter or select multicast mode. When the unicast method is inappropriate, select the multicast method
Selecting the Unicast Method
- The cluster adapters for all cluster hosts are assigned the same unicast MAC address.
- The outgoing MAC address for each packet is modified, based on the cluster host’s priority setting, to prevent upstream switches from discovering that all cluster hosts have the same MAC address.
- The modification of the outgoing MAC address is appropriate for switches. When a hub is used to connect the cluster hosts, disable the modification of the outgoing MAC address. On Windows Server 2003, you can disable modification of outgoing addresses by setting the value of the registry entry MaskSourceMAC, of data type REG_DWORD, to 0x0. MaskSourceMAC is located in HKLM\SYSTEM\CurrentControlSet\Services\WLBS\Parameters\Interface\Adapter-GUID (where Adapter-GUID is the long GUID assigned to the network adapter in the server).
- The unicast MAC address is derived from the cluster’s IP address to ensure uniqueness outside the cluster hosts.
- Communication between cluster hosts, other than Network Load Balancing–related traffic (such as heartbeat), is only available when you install an additional adapter, because the cluster hosts all have the same MAC address.
Although the unicast method works in all routing situations, it has the following disadvantages:
- A second network adapter is required to provide peer-to-peer communication between cluster hosts.
- If the cluster is connected to a switch, incoming packets are sent to all the ports on the switch, which can cause switch flooding.
Selecting the Multicast Method
- The cluster adapter for each cluster host retains the original hardware unicast MAC address (as specified by the hardware manufacture of the network adapter).
- The cluster adapters for all cluster hosts are assigned a multicast MAC address.
- The multicast MAC is derived from the cluster’s IP address.
- Communication between cluster hosts is not affected, because each cluster host retains a unique MAC address
By using the multicast method with Internet Group Membership Protocol (IGMP), you can limit switch flooding, if the switch supports IGMP snooping. IGMP snooping allows the switch to examine the contents of multicast packets and associate a port with a multicast address. Without IGMP snooping, switches might require additional configuration to tell the switch which ports to use for the multicast traffic. Otherwise, switch flooding occurs, as with the unicast method.
The multicast method has the following disadvantages:
- Upstream routers might require a static Address Resolution Protocol (ARP) entry. This is because routers might not accept an ARP response that resolves unicast IP addresses to multicast MAC addresses.
- Without IGMP, switches might require additional configuration to tell the switch which ports to use for the multicast traffic.
- Upstream routers might not support mapping a unicast IP address (the cluster IP address) with a multicast MAC address. In these situations, you must upgrade or replace the router. Otherwise, the multicast method is unusable.